Figure 1. How a typical network-based ATM malware attack is carried out
REF: http://blog.trendmicro.com/trendlabs-security-intelligence/an-elaborate-atm-threat-crops-up-network-based-atm-malware-attacks/
2017年9月30日 星期六
Security.txt Standard Proposed, Similar to Robots.txt
According to the current IETF draft, website owners would be able to create security.txt files that look like this:
#This is a comment
Contact: security@example.com
Contact: +1-201-555-0123
Contact: https://example.com/security
Encryption: https://example.com/pgp-key.txt
Acknowledgement: https://example.com/acknowledgements.html
Disclosure: FullREF: https://www.bleepingcomputer.com/news/security/security-txt-standard-proposed-similar-to-robots-txt/
TrendLabs: Tech Support Scams
2017年9月26日 星期二
TrendLabs: The Apache HTTP Server Now Bleeds
Figure 3. Memory leak resulting from a misconfigured .htaccess file
REF: http://blog.trendmicro.com/trendlabs-security-intelligence/optionsbleed-apache-http-server-now-bleeds/
GCP: Expanding Kubernetes in the enterprise
vmware-pivotal-google-cloud
Google Container Engine + Pivotal Container Service
REF: https://www.blog.google/topics/google-cloud/vmware-and-pivotal-launch-new-hybrid-kubernetes-solution-optimized-gcp/
2017年9月24日 星期日
TrendLabs: Spam Campaigns Upgraded
Figure 3. Distribution of second spam campaign
REF: http://blog.trendmicro.com/trendlabs-security-intelligence/locky-ransomware-pushed-alongside-fakeglobe-upgraded-spam-campaigns/
2017年9月23日 星期六
USN-3426-1: Samba vulnerabilities
REF: https://usn.ubuntu.com/usn/usn-3426-1/
Details
Stefan Metzmacher discovered that Samba incorrectly enforced SMB signing in
certain situations. A remote attacker could use this issue to perform a man
in the middle attack. (CVE-2017-12150)
certain situations. A remote attacker could use this issue to perform a man
in the middle attack. (CVE-2017-12150)
Stefan Metzmacher discovered that Samba incorrectly handled encryption
across DFS redirects. A remote attacker could use this issue to perform a
man in the middle attack. (CVE-2017-12151)
across DFS redirects. A remote attacker could use this issue to perform a
man in the middle attack. (CVE-2017-12151)
Yihan Lian and Zhibin Hu discovered that Samba incorrectly handled memory
when SMB1 is being used. A remote attacker could possibly use this issue to
obtain server memory contents. (CVE-2017-12163)
when SMB1 is being used. A remote attacker could possibly use this issue to
obtain server memory contents. (CVE-2017-12163)
2017年9月22日 星期五
TrendLabs: RETADUP Variants Hit South America
http://blog.trendmicro.com/trendlabs-security-intelligence/new-retadup-variants-hit-south-america-turn-cryptocurrency-mining/
CephFS as SDS
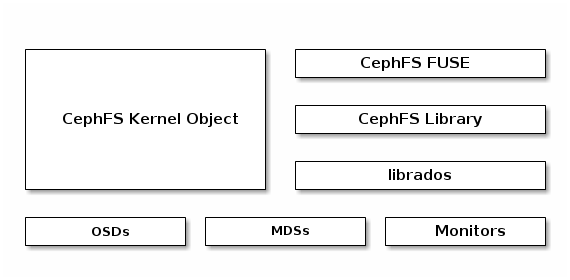
To run the Ceph File System, you must have a running Ceph Storage Cluster with at least one Ceph Metadata Server (MDS) running. For details on installing the Ceph Storage Cluster, see the Installation Guide for Red Hat Enterprise Linux or Installation Guide for Ubuntu. See Chapter 2, Installing and Configuring Ceph Metadata Servers (MDS) for details on installing the Ceph Metadata Server.
REF: https://access.redhat.com/documentation/en-us/red_hat_ceph_storage/2/html/ceph_file_system_guide_technology_preview/what_is_the_ceph_file_system_cephfs
TrendLabs: Bluetooth exploits
BlueBorne is a combination of vulnerabilities related to vague and outdated definitions of the Bluetooth protocol, including authorization and authentication issues. The absence or wrong validation of different protocol parameters in the Bluetooth stack code can result in stack or heap overflow in the kernel address space. When combined with an outdated implementation, they can lead to remote code execution (RCE).
REF: http://blog.trendmicro.com/trendlabs-security-intelligence/blueborne-reportedly-affects-billions-bluetooth-enabled-devices/
REF: http://blog.trendmicro.com/trendlabs-security-intelligence/blueborne-reportedly-affects-billions-bluetooth-enabled-devices/
2017年9月20日 星期三
Blackmagic Design IBC 2017
The all new Ultimatte 12 is more than the world’s best keyer, it’s an advanced real time compositing processor designed for the next generation of broadcast graphics. It features entirely new algorithms and color science, incredible edge handling, greater color separation, amazing color fidelity and better spill suppression than ever before.
REF: https://www.blackmagicdesign.com/products/ultimatte
REF: https://www.blackmagicdesign.com/products/ultimatte
2017年9月19日 星期二
Remote Desktop with X2Go
...you can start your graphical session by clicking the white box that includes your session name on the top-right side of the screen.
REF: https://www.digitalocean.com/community/tutorials/how-to-setup-a-remote-desktop-with-x2go-on-debian-8
2017年9月18日 星期一
Free software in hackathons
Hackathons fit the spirit of a community in which people take an attitude of cooperation and respect towards each other. The software that accords with this spirit is free (libre) software, free as in freedom. Free software carries a license that gives its users (including programmers) freedom to cooperate. Thus, hackathons make sense within the free software community. Hardware design projects also can and ought to be free.
REF: https://www.gnu.org/philosophy/hackathons.html
REF: https://www.gnu.org/philosophy/hackathons.html
TrendLabs: DoS to Android
A denial-of-service vulnerability we recently disclosed to Google can do exactly that and more. Designated as CVE-2017-0780, we’ve confirmed it to be in the latest Nexus and Pixel devices. The security flaw can let attackers illicitly and remotely crash their victims’ Android Messages app by sending a malformed multimedia message (MMS). The app will also be incapable of recovering from the crash even if the device/system is rebooted or booted in safe mode.
REF: http://blog.trendmicro.com/trendlabs-security-intelligence/cve-2017-0780-denial-service-vulnerability-android-messages-app/
REF: http://blog.trendmicro.com/trendlabs-security-intelligence/cve-2017-0780-denial-service-vulnerability-android-messages-app/
Phones with free software
We don't have a freedom-respecting drop-in replacement for the iPhone. Apple's government-subsidized DRM and massive legal intimidation team make developing and distributing a freedom-respecting smartphone very difficult. But we are nonetheless getting closer. You can have a solid, basic smartphone today by running Replicant, a free software version of Android. You can install it yourself on supported models, or buy one pre-installed from Technoethical. You can give the Replicant project a boost, and help them to implement missing features, by donating. Also, check out F-Droid, an app repository of exclusively free software for Android.
REF: http://www.fsf.org/blogs/community/the-apple-is-still-rotten-why-you-should-avoid-the-new-iphone
REF: http://www.fsf.org/blogs/community/the-apple-is-still-rotten-why-you-should-avoid-the-new-iphone
Google Cloud Interconnect
Google Cloud Dedicated Interconnect extends your on-premises network to Google's network through a dedicated, private connection.
REF: https://cloud.google.com/interconnect/docs/
ResourceSpace: facial recognition and more!
13TH SEPTEMBER 2017

TrendLabs: Abuse of Malicious Attachments
The Hangul Word Processor (HWP) is a word processing application which is fairly popular in South Korea. It possesses the ability to run PostScript code, which is a language originally used for printing and desktop publishing, although it is a fully capable language. Unfortunately, this ability is now being exploited in attacks involving malicious attachments.
REF: http://blog.trendmicro.com/trendlabs-security-intelligence/hangul-word-processor-postscript-abused-malicious-attachments/
REF: http://blog.trendmicro.com/trendlabs-security-intelligence/hangul-word-processor-postscript-abused-malicious-attachments/
Proxmox VE 5.1: new Ceph, Kernel, ZFS, LXC 2.1
The upcoming Proxmox VE 5.1 will get production ready Ceph Luminous LTS, a new 4.13 Linux Kernel, latest ZFS and LXC 2.1. Our beta repositories already contain quite stable Ceph 12.2.x packages and the GUI integration includes a new cool features, e.g. creating Ceph storages for VMs and Containers with just one click on the "Create Ceph Pool" wizard. (This will also copy all needed authentication keys.)
REF: https://forum.proxmox.com/threads/planning-proxmox-ve-5-1-ceph-luminous-kernel-4-13-latest-zfs-lxc-2-1.36943/
REF: https://forum.proxmox.com/threads/planning-proxmox-ve-5-1-ceph-luminous-kernel-4-13-latest-zfs-lxc-2-1.36943/
2017年9月10日 星期日
Internet Governance 2017 Sep
- 18000 people for maintainence of GFW.
- 1996 starts GFW - > golden shield
- domain names ip
- keywords
- VPN : 90,000,000 people using in China
- cyber regulations
2017年9月9日 星期六
Digital Asset Management improves document preservation at PASIG 2017

TrendLabs: EMOTET Spreading via Spam Botnet
Figure 2: EMOTET Infection Diagram for the recent wave of attacks
REF: http://blog.trendmicro.com/trendlabs-security-intelligence/emotet-returns-starts-spreading-via-spam-botnet/
2017年9月7日 星期四
THE ARMY GROUNDS ITS DJI DRONES OVER SECURITY CONCERNS
REF: https://www.wired.com/story/army-dji-drone-ban/
THE US ARMY has increasingly used small consumer drones in the field, purchasing them as needed from consumer manufacturers like the well-known Chinese maker DJI. But documents indicate that the Army Aviation Directorate is now enforcing new orders, banning DJI drones “due to increased awareness of cyber vulnerabilities associated with DJI products.”
2017 CloudSec
- SecDevOps
- CSO: 24x7 dedicated professional
- CEO engagement
- IoT: GPS, USB plug interception
- Active Defense
- Education and Drill, down to individual
- SOC 2.0: hunter team
- Red Army: attack team to our infra
- outsourcing attack
- PPT: people, process, technology
- misconfiguration of DNS resolvers
Oops! 185,000-plus Wi-Fi cameras on the web with insecure admin panels
REF: https://www.theregister.co.uk/2017/03/09/185000_wifi_cameras_naked_on_net/
Get ready for the next camera-botnet: a Chinese generic wireless webcam sold under more than 1,200 brands from 354 vendors has a buggy and exploitable embedded web server.
Puppet Fundamentals
Duration
3 days
Course Content
The fundamental component roles that make up Puppet Enterprise (and Puppet Open Source).
The core concepts for the Puppet DSL, including:
- Modules and Classes
- Classification
- Resources
- Relationships
- Language Constructs
Separating logic from presentation by using Templates.
Modeling repeatable portions of your configuration by using Defined Resource Types.
Building a foundation for building more complex configurations by using Advanced Classes:
- Parameterized Classes
- Introduction to Inheritance
- Introduction to Data Separation using Hiera
- Revisiting Classification using parameterized classes & ADB
An introduction to using modules from the Puppet Forge and Supported Modules.
A brief introduction to the Roles and Profiles design pattern.
REF: https://learn.puppet.com/instructor-led-training/puppet-fundamentals2017年9月3日 星期日
Copying a Joomla! website
Copying a website using SSH command line (method for experienced users)
Copying the files using a compressed archive file method
Copying a large number of individual files using FTP can sometimes be unreliable. If you have command-line access to the both source and destination systems then you can create a compressed archive file containing all the files on the source system, then transfer that single file to the destination system where it can be decompressed.
Copying the database with MySQL command line method
2017年9月2日 星期六
Wowza Transcode Live Streams
Supported video and audio formats
Wowza Transcoder can decode and encode the following video and audio codecs:
Video decoding (source streams)
|
Audio decoding (source streams)
|
Video encoding (outbound renditions)
|
Audio encoding (outbound renditions)
|
| H.264 MPEG-2 MPEG-4 Part 2 VP8 VP9 | AAC G.711 (µ-law and A-law) MPEG-1 Layer 1/2 MPEG-1 Layer 3 (MP3) Speex Vorbis Opus | H.264 H.263v2 VP8 VP9 | AAC Vorbis Opus |
trendLabs: Android Mobile Ransomware
http://blog.trendmicro.com/trendlabs-security-intelligence/android-mobile-ransomware-evolution/
訂閱:
文章 (Atom)
