Figure 2. Geographical distribution of deployed unsecured Redis instances
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/more-than-8000-unsecured-redis-instances-found-in-the-cloud/
2020年5月31日 星期日
[USN-4370-1] ClamAV vulnerabilities
---------- Forwarded message ---------
From: Marc Deslauriers
Date: May 22, 2020 2:46AM
It was discovered that ClamAV incorrectly handled parsing ARJ archives. A
remote attacker could possibly use this issue to cause ClamAV to crash,
resulting in a denial of service. (CVE-2020-3327)
It was discovered that ClamAV incorrectly handled parsing PDF files. A
remote attacker could possibly use this issue to cause ClamAV to crash,
resulting in a denial of service. (CVE-2020-3341)
References:
https://usn.ubuntu.com/4370-1
CVE-2020-3327, CVE-2020-3341
From: Marc Deslauriers
Date: May 22, 2020 2:46AM
It was discovered that ClamAV incorrectly handled parsing ARJ archives. A
remote attacker could possibly use this issue to cause ClamAV to crash,
resulting in a denial of service. (CVE-2020-3327)
It was discovered that ClamAV incorrectly handled parsing PDF files. A
remote attacker could possibly use this issue to cause ClamAV to crash,
resulting in a denial of service. (CVE-2020-3341)
References:
https://usn.ubuntu.com/4370-1
CVE-2020-3327, CVE-2020-3341
Cloudflare: Keepalives considered harmful
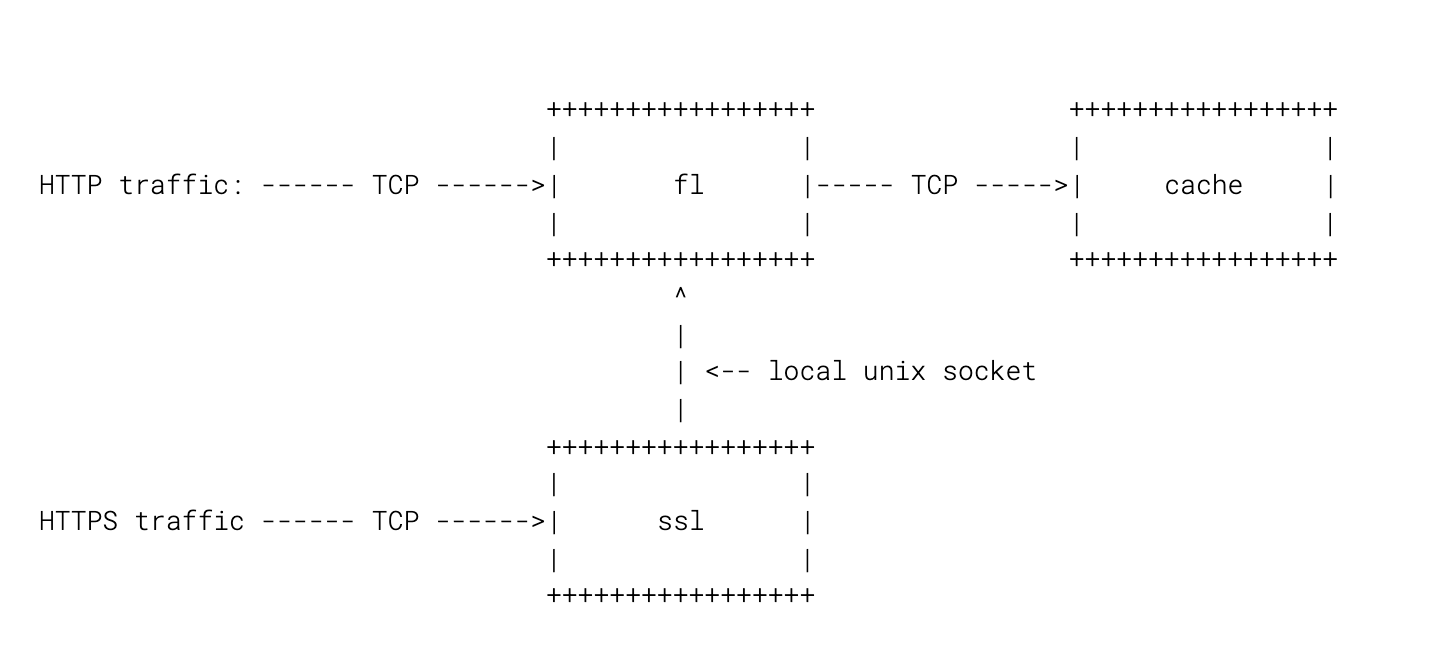
Proxmox VE 6.2 released
Here are the highlights:
- Debian Buster (10.4) and a Linux Kernel 5.4
- QEMU 5.0, LXC 4.0, and ZFS 0.8.3
- Ceph Nautilus (14.2.9)
- Create templates for containers on directory-based storage
- Zstandard for Backup/Restore
- New LDAP sync enables synchronization of LDAP users and groups
- API tokens: Full support and integration
- and a lot more...
Forum announcement
Watch the video
Press release
Roku: New movie releases coming straight to streaming.
17 movies coming straight to streaming in June
From Artemis Fowl to The King of Staten Island, check out the most anticipated movies skipping the box office to premiere at your house this June.
[USN-4372-1] QEMU vulnerabilities
---------- Forwarded message ---------
From: Marc Deslauriers
Date: May 22, 2020 2:46AM
It was discovered that QEMU incorrectly handled bochs-display devices. A
local attacker in a guest could use this to cause a denial of service or
possibly execute arbitrary code in the host. This issue only affected
Ubuntu 19.10. (CVE-2019-15034)
It was discovered that QEMU incorrectly handled memory during certain VNC
operations. A remote attacker could possibly use this issue to cause QEMU
to consume resources, resulting in a denial of service. This issue only
affected Ubuntu 16.04 LTS, Ubuntu 18.04 LTS, and Ubuntu 19.10.
(CVE-2019-20382)
It was discovered that QEMU incorrectly generated QEMU Pointer
Authentication signatures on ARM. A local attacker could possibly use this
issue to bypass PAuth. This issue only affected Ubuntu 19.10.
(CVE-2020-10702)
Ziming Zhang discovered that QEMU incorrectly handled ATI VGA emulation. A
local attacker in a guest could use this issue to cause QEMU to crash,
resulting in a denial of service. This issue only affected Ubuntu 20.04
LTS. (CVE-2020-11869)
Aviv Sasson discovered that QEMU incorrectly handled Slirp networking. A
remote attacker could use this issue to cause QEMU to crash, resulting in a
denial of service, or possibly execute arbitrary code. This issue only
affected Ubuntu 16.04 LTS, Ubuntu 18.04 LTS, and Ubuntu 19.10.
(CVE-2020-1983)
References:
https://usn.ubuntu.com/4372-1
CVE-2019-15034, CVE-2019-20382, CVE-2020-10702, CVE-2020-11869,
CVE-2020-1983
From: Marc Deslauriers
Date: May 22, 2020 2:46AM
It was discovered that QEMU incorrectly handled bochs-display devices. A
local attacker in a guest could use this to cause a denial of service or
possibly execute arbitrary code in the host. This issue only affected
Ubuntu 19.10. (CVE-2019-15034)
It was discovered that QEMU incorrectly handled memory during certain VNC
operations. A remote attacker could possibly use this issue to cause QEMU
to consume resources, resulting in a denial of service. This issue only
affected Ubuntu 16.04 LTS, Ubuntu 18.04 LTS, and Ubuntu 19.10.
(CVE-2019-20382)
It was discovered that QEMU incorrectly generated QEMU Pointer
Authentication signatures on ARM. A local attacker could possibly use this
issue to bypass PAuth. This issue only affected Ubuntu 19.10.
(CVE-2020-10702)
Ziming Zhang discovered that QEMU incorrectly handled ATI VGA emulation. A
local attacker in a guest could use this issue to cause QEMU to crash,
resulting in a denial of service. This issue only affected Ubuntu 20.04
LTS. (CVE-2020-11869)
Aviv Sasson discovered that QEMU incorrectly handled Slirp networking. A
remote attacker could use this issue to cause QEMU to crash, resulting in a
denial of service, or possibly execute arbitrary code. This issue only
affected Ubuntu 16.04 LTS, Ubuntu 18.04 LTS, and Ubuntu 19.10.
(CVE-2020-1983)
References:
https://usn.ubuntu.com/4372-1
CVE-2019-15034, CVE-2019-20382, CVE-2020-10702, CVE-2020-11869,
CVE-2020-1983
[USN-4369-1] Linux kernel vulnerabilities
---------- Forwarded message ---------
From: Steve Beattie
Date: May 21, 2020 1:02PM
It was discovered that the btrfs implementation in the Linux kernel did not
properly detect that a block was marked dirty in some situations. An
attacker could use this to specially craft a file system image that, when
unmounted, could cause a denial of service (system crash). (CVE-2019-19377)
Tristan Madani discovered that the file locking implementation in the Linux
kernel contained a race condition. A local attacker could possibly use this
to cause a denial of service or expose sensitive information.
(CVE-2019-19769)
It was discovered that the Serial CAN interface driver in the Linux kernel
did not properly initialize data. A local attacker could use this to expose
sensitive information (kernel memory). (CVE-2020-11494)
It was discovered that the linux kernel did not properly validate certain
mount options to the tmpfs virtual memory file system. A local attacker
with the ability to specify mount options could use this to cause a denial
of service (system crash). (CVE-2020-11565)
It was discovered that the OV51x USB Camera device driver in the Linux
kernel did not properly validate device metadata. A physically proximate
attacker could use this to cause a denial of service (system crash).
(CVE-2020-11608)
It was discovered that the STV06XX USB Camera device driver in the Linux
kernel did not properly validate device metadata. A physically proximate
attacker could use this to cause a denial of service (system crash).
(CVE-2020-11609)
It was discovered that the Xirlink C-It USB Camera device driver in the
Linux kernel did not properly validate device metadata. A physically
proximate attacker could use this to cause a denial of service (system
crash). (CVE-2020-11668)
It was discovered that the block layer in the Linux kernel contained a race
condition leading to a use-after-free vulnerability. A local attacker could
possibly use this to cause a denial of service (system crash) or execute
arbitrary code. (CVE-2020-12657)
References:
https://usn.ubuntu.com/4369-1
CVE-2019-19377, CVE-2019-19769, CVE-2020-11494, CVE-2020-11565,
CVE-2020-11608, CVE-2020-11609, CVE-2020-11668, CVE-2020-12657
From: Steve Beattie
Date: May 21, 2020 1:02PM
It was discovered that the btrfs implementation in the Linux kernel did not
properly detect that a block was marked dirty in some situations. An
attacker could use this to specially craft a file system image that, when
unmounted, could cause a denial of service (system crash). (CVE-2019-19377)
Tristan Madani discovered that the file locking implementation in the Linux
kernel contained a race condition. A local attacker could possibly use this
to cause a denial of service or expose sensitive information.
(CVE-2019-19769)
It was discovered that the Serial CAN interface driver in the Linux kernel
did not properly initialize data. A local attacker could use this to expose
sensitive information (kernel memory). (CVE-2020-11494)
It was discovered that the linux kernel did not properly validate certain
mount options to the tmpfs virtual memory file system. A local attacker
with the ability to specify mount options could use this to cause a denial
of service (system crash). (CVE-2020-11565)
It was discovered that the OV51x USB Camera device driver in the Linux
kernel did not properly validate device metadata. A physically proximate
attacker could use this to cause a denial of service (system crash).
(CVE-2020-11608)
It was discovered that the STV06XX USB Camera device driver in the Linux
kernel did not properly validate device metadata. A physically proximate
attacker could use this to cause a denial of service (system crash).
(CVE-2020-11609)
It was discovered that the Xirlink C-It USB Camera device driver in the
Linux kernel did not properly validate device metadata. A physically
proximate attacker could use this to cause a denial of service (system
crash). (CVE-2020-11668)
It was discovered that the block layer in the Linux kernel contained a race
condition leading to a use-after-free vulnerability. A local attacker could
possibly use this to cause a denial of service (system crash) or execute
arbitrary code. (CVE-2020-12657)
References:
https://usn.ubuntu.com/4369-1
CVE-2019-19377, CVE-2019-19769, CVE-2020-11494, CVE-2020-11565,
CVE-2020-11608, CVE-2020-11609, CVE-2020-11668, CVE-2020-12657
2020年5月23日 星期六
[USN-4353-1] Firefox vulnerabilities
---------- Forwarded message ---------
From: Chris Coulson
Date: May 7, 2020 11:18PM
Multiple security issues were discovered in Firefox. If a user were
tricked in to opening a specially crafted website, an attacker could
potentially exploit these to cause a denial of service, bypass security
restrictions, spoof the URL bar, or execute arbitrary code.
(CVE-2020-6831, CVE-2020-12387, CVE-2020-12390, CVE-2020-12391,
CVE-2020-12394, CVE-2020-12395, CVE-2020-12396)
It was discovered that the Devtools’ ‘Copy as cURL’ feature did not
properly HTTP POST data of a request. If a user were tricked in to using
the ‘Copy as cURL’ feature to copy and paste a command with specially
crafted data in to a terminal, an attacker could potentially exploit this
to obtain sensitive information from local files.
(CVE-2020-12392)
References:
https://usn.ubuntu.com/4353-1
CVE-2020-12387, CVE-2020-12390, CVE-2020-12391, CVE-2020-12392,
CVE-2020-12394, CVE-2020-12395, CVE-2020-12396, CVE-2020-6831
From: Chris Coulson
Date: May 7, 2020 11:18PM
Multiple security issues were discovered in Firefox. If a user were
tricked in to opening a specially crafted website, an attacker could
potentially exploit these to cause a denial of service, bypass security
restrictions, spoof the URL bar, or execute arbitrary code.
(CVE-2020-6831, CVE-2020-12387, CVE-2020-12390, CVE-2020-12391,
CVE-2020-12394, CVE-2020-12395, CVE-2020-12396)
It was discovered that the Devtools’ ‘Copy as cURL’ feature did not
properly HTTP POST data of a request. If a user were tricked in to using
the ‘Copy as cURL’ feature to copy and paste a command with specially
crafted data in to a terminal, an attacker could potentially exploit this
to obtain sensitive information from local files.
(CVE-2020-12392)
References:
https://usn.ubuntu.com/4353-1
CVE-2020-12387, CVE-2020-12390, CVE-2020-12391, CVE-2020-12392,
CVE-2020-12394, CVE-2020-12395, CVE-2020-12396, CVE-2020-6831
TrendLabs: Raccoon Stealer’s Abuse of Google Cloud Services and Multiple Delivery Techniques
Figure 3. Countries affected by Raccoon malware since April 2019
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/raccoon-stealers-abuse-of-google-cloud-services-and-multiple-delivery-techniques/
[USN-4345-1] Linux kernel vulnerabilities
---------- Forwarded message ---------
Al Viro discovered that the Linux kernel for s390x systems did not properly
perform page table upgrades for kernel sections that use secondary address
mode. A local attacker could use this to cause a denial of service (system
crash) or execute arbitrary code. (CVE-2020-11884)
It was discovered that the Intel Wi-Fi driver in the Linux kernel did not
properly check for errors in some situations. A local attacker could
possibly use this to cause a denial of service (system crash).
(CVE-2019-16234)
Tristan Madani discovered that the block I/O tracing implementation in the
Linux kernel contained a race condition. A local attacker could use this to
cause a denial of service (system crash) or possibly expose sensitive
information. (CVE-2019-19768)
It was discovered that the vhost net driver in the Linux kernel contained a
stack buffer overflow. A local attacker with the ability to perform ioctl()
calls on /dev/vhost-net could use this to cause a denial of service (system
crash). (CVE-2020-10942)
It was discovered that the OV51x USB Camera device driver in the Linux
kernel did not properly validate device metadata. A physically proximate
attacker could use this to cause a denial of service (system crash).
(CVE-2020-11608)
It was discovered that the STV06XX USB Camera device driver in the Linux
kernel did not properly validate device metadata. A physically proximate
attacker could use this to cause a denial of service (system crash).
(CVE-2020-11609)
It was discovered that the Xirlink C-It USB Camera device driver in the
Linux kernel did not properly validate device metadata. A physically
proximate attacker could use this to cause a denial of service (system
crash). (CVE-2020-11668)
It was discovered that the virtual terminal implementation in the Linux
kernel contained a race condition. A local attacker could possibly use this
to cause a denial of service (system crash) or expose sensitive
information. (CVE-2020-8648)
Jordy Zomer discovered that the floppy driver in the Linux kernel did not
properly check for errors in some situations. A local attacker could
possibly use this to cause a denial of service (system crash) or possibly
expose sensitive information. (CVE-2020-9383)
References:
https://usn.ubuntu.com/4345-1
CVE-2019-16234, CVE-2019-19768, CVE-2020-10942, CVE-2020-11608,
CVE-2020-11609, CVE-2020-11668, CVE-2020-11884, CVE-2020-8648,
CVE-2020-9383
From: Steve Beattie
Date: Apr 29, 2020 10:30AM
Date: Apr 29, 2020 10:30AM
Al Viro discovered that the Linux kernel for s390x systems did not properly
perform page table upgrades for kernel sections that use secondary address
mode. A local attacker could use this to cause a denial of service (system
crash) or execute arbitrary code. (CVE-2020-11884)
It was discovered that the Intel Wi-Fi driver in the Linux kernel did not
properly check for errors in some situations. A local attacker could
possibly use this to cause a denial of service (system crash).
(CVE-2019-16234)
Tristan Madani discovered that the block I/O tracing implementation in the
Linux kernel contained a race condition. A local attacker could use this to
cause a denial of service (system crash) or possibly expose sensitive
information. (CVE-2019-19768)
It was discovered that the vhost net driver in the Linux kernel contained a
stack buffer overflow. A local attacker with the ability to perform ioctl()
calls on /dev/vhost-net could use this to cause a denial of service (system
crash). (CVE-2020-10942)
It was discovered that the OV51x USB Camera device driver in the Linux
kernel did not properly validate device metadata. A physically proximate
attacker could use this to cause a denial of service (system crash).
(CVE-2020-11608)
It was discovered that the STV06XX USB Camera device driver in the Linux
kernel did not properly validate device metadata. A physically proximate
attacker could use this to cause a denial of service (system crash).
(CVE-2020-11609)
It was discovered that the Xirlink C-It USB Camera device driver in the
Linux kernel did not properly validate device metadata. A physically
proximate attacker could use this to cause a denial of service (system
crash). (CVE-2020-11668)
It was discovered that the virtual terminal implementation in the Linux
kernel contained a race condition. A local attacker could possibly use this
to cause a denial of service (system crash) or expose sensitive
information. (CVE-2020-8648)
Jordy Zomer discovered that the floppy driver in the Linux kernel did not
properly check for errors in some situations. A local attacker could
possibly use this to cause a denial of service (system crash) or possibly
expose sensitive information. (CVE-2020-9383)
References:
https://usn.ubuntu.com/4345-1
CVE-2019-16234, CVE-2019-19768, CVE-2020-10942, CVE-2020-11608,
CVE-2020-11609, CVE-2020-11668, CVE-2020-11884, CVE-2020-8648,
CVE-2020-9383
FSF: Young hackers to deliver opening keynote for LibrePlanet conference

REF: https://www.fsf.org/news/young-hackers-to-deliver-opening-keynote-for-libreplanet-conference
Cloudflare for Teams Free for Small Businesses During Coronavirus Emergency

2020年5月16日 星期六
[USN-4337-1] OpenJDK vulnerabilities
---------- Forwarded message ---------
It was discovered that OpenJDK incorrectly handled certain regular
expressions. An attacker could possibly use this issue to cause a denial of
service while processing a specially crafted regular expression.
(CVE-2020-2754, CVE-2020-2755)
It was discovered that OpenJDK incorrectly handled class descriptors and
catching exceptions during object stream deserialization. An attacker could
possibly use this issue to cause a denial of service while processing a
specially crafted serialized input. (CVE-2020-2756, CVE-2020-2757)
Bengt Jonsson, Juraj Somorovsky, Kostis Sagonas, Paul Fiterau Brostean and
Robert Merget discovered that OpenJDK incorrectly handled certificate messages
during TLS handshake. An attacker could possibly use this issue to bypass
certificate verification and insert, edit or obtain sensitive information. This
issue only affected OpenJDK 11. (CVE-2020-2767)
It was discovered that OpenJDK incorrectly handled exceptions thrown by
unmarshalKeyInfo() and unmarshalXMLSignature(). An attacker could possibly use
this issue to cause a denial of service while reading key info or XML signature
data from XML input. (CVE-2020-2773)
Peter Dettman discovered that OpenJDK incorrectly handled SSLParameters in
setAlgorithmConstraints(). An attacker could possibly use this issue to
override the defined systems security policy and lead to the use of weak
crypto algorithms that should be disabled. This issue only affected
OpenJDK 11. (CVE-2020-2778)
Simone Bordet discovered that OpenJDK incorrectly re-used single null TLS
sessions for new TLS connections. A remote attacker could possibly use this
issue to cause a denial of service. (CVE-2020-2781)
Dan Amodio discovered that OpenJDK did not restrict the use of CR and LF
characters in values for HTTP headers. An attacker could possibly use this
issue to insert, edit or obtain sensitive information. (CVE-2020-2800)
Nils Emmerich discovered that OpenJDK incorrectly checked boundaries or
argument types. An attacker could possibly use this issue to bypass sandbox
restrictions causing unspecified impact. (CVE-2020-2803, CVE-2020-2805)
It was discovered that OpenJDK incorrectly handled application data packets
during TLS handshake. An attacker could possibly use this issue to insert,
edit or obtain sensitive information. This issue only affected OpenJDK 11.
(CVE-2020-2816)
It was discovered that OpenJDK incorrectly handled certain regular
expressions. An attacker could possibly use this issue to cause a denial of
service. (CVE-2020-2830)
References:
https://usn.ubuntu.com/4337-1
CVE-2020-2754, CVE-2020-2755, CVE-2020-2756, CVE-2020-2757,
CVE-2020-2767, CVE-2020-2773, CVE-2020-2778, CVE-2020-2781,
CVE-2020-2800, CVE-2020-2803, CVE-2020-2805, CVE-2020-2816,
CVE-2020-2830
From: Eduardo Barretto
Date: Apr 23, 2020 1:16AM
Date: Apr 23, 2020 1:16AM
It was discovered that OpenJDK incorrectly handled certain regular
expressions. An attacker could possibly use this issue to cause a denial of
service while processing a specially crafted regular expression.
(CVE-2020-2754, CVE-2020-2755)
It was discovered that OpenJDK incorrectly handled class descriptors and
catching exceptions during object stream deserialization. An attacker could
possibly use this issue to cause a denial of service while processing a
specially crafted serialized input. (CVE-2020-2756, CVE-2020-2757)
Bengt Jonsson, Juraj Somorovsky, Kostis Sagonas, Paul Fiterau Brostean and
Robert Merget discovered that OpenJDK incorrectly handled certificate messages
during TLS handshake. An attacker could possibly use this issue to bypass
certificate verification and insert, edit or obtain sensitive information. This
issue only affected OpenJDK 11. (CVE-2020-2767)
It was discovered that OpenJDK incorrectly handled exceptions thrown by
unmarshalKeyInfo() and unmarshalXMLSignature(). An attacker could possibly use
this issue to cause a denial of service while reading key info or XML signature
data from XML input. (CVE-2020-2773)
Peter Dettman discovered that OpenJDK incorrectly handled SSLParameters in
setAlgorithmConstraints(). An attacker could possibly use this issue to
override the defined systems security policy and lead to the use of weak
crypto algorithms that should be disabled. This issue only affected
OpenJDK 11. (CVE-2020-2778)
Simone Bordet discovered that OpenJDK incorrectly re-used single null TLS
sessions for new TLS connections. A remote attacker could possibly use this
issue to cause a denial of service. (CVE-2020-2781)
Dan Amodio discovered that OpenJDK did not restrict the use of CR and LF
characters in values for HTTP headers. An attacker could possibly use this
issue to insert, edit or obtain sensitive information. (CVE-2020-2800)
Nils Emmerich discovered that OpenJDK incorrectly checked boundaries or
argument types. An attacker could possibly use this issue to bypass sandbox
restrictions causing unspecified impact. (CVE-2020-2803, CVE-2020-2805)
It was discovered that OpenJDK incorrectly handled application data packets
during TLS handshake. An attacker could possibly use this issue to insert,
edit or obtain sensitive information. This issue only affected OpenJDK 11.
(CVE-2020-2816)
It was discovered that OpenJDK incorrectly handled certain regular
expressions. An attacker could possibly use this issue to cause a denial of
service. (CVE-2020-2830)
References:
https://usn.ubuntu.com/4337-1
CVE-2020-2754, CVE-2020-2755, CVE-2020-2756, CVE-2020-2757,
CVE-2020-2767, CVE-2020-2773, CVE-2020-2778, CVE-2020-2781,
CVE-2020-2800, CVE-2020-2803, CVE-2020-2805, CVE-2020-2816,
CVE-2020-2830
Cloudflare: On the shoulders of giants: recent changes in Internet traffic
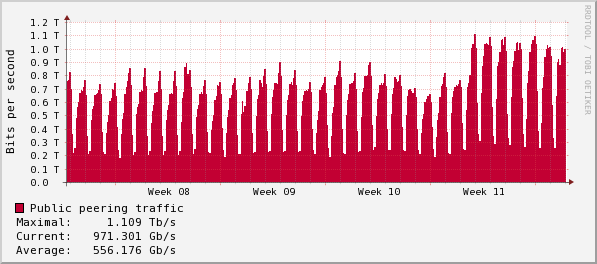
REF: https://blog.cloudflare.com/on-the-shoulders-of-giants-recent-changes-in-internet-traffic/
[USN-4334-1] Git vulnerability
---------- Forwarded message ---------
Carlo Arenas discovered that Git incorrectly handled certain URLs
containing newlines, empty hosts, or lacking a scheme. A remote attacker
could possibly use this issue to trick Git into returning credential
information for a wrong host.
References:
https://usn.ubuntu.com/4334-1
CVE-2020-11008
From: Marc Deslauriers
Date: Apr 21, 2020 9:01PM
Date: Apr 21, 2020 9:01PM
Carlo Arenas discovered that Git incorrectly handled certain URLs
containing newlines, empty hosts, or lacking a scheme. A remote attacker
could possibly use this issue to trick Git into returning credential
information for a wrong host.
References:
https://usn.ubuntu.com/4334-1
CVE-2020-11008
Cloudflare: Announcing the Beta for WARP for macOS and Windows

WARP+ Gets You There Faster
REF: https://blog.cloudflare.com/announcing-the-beta-for-warp-for-macos-and-windows/MagicSoft Recorder ver 3.0.2
| MagicSoft Recorder ver 3 was released and it adds several new features : - support for NDI inputs (both YUV and RGBA modes are supported) - possibility to set a workflow for capturing on 8 bit or 10 bit for the incoming video - a lower CPU and RAM bandwidth consumption are archived for a 8 bit capturing workflow - using an intermediary storage buffer to overcome the storage problems encountered when using an over-the-network storage - added indicators into the user interface for the level of input buffer and storage buffer |
Roku: 18 must-stream TV show premieres in April
The calendar for April is jam-packed with over 18 premiere episodes of shows, including Penny Dreadful: City of Angels, Killing Eve, and Mrs. America.
Take control with Plex Dash
LibreSSL 3.1.1 released
---------- Forwarded message ---------
From: Brent Cook
Date: Sat, May 9, 2020 at 1:35 AM
We have released LibreSSL 3.1.1, which will be arriving in the
LibreSSL directory of your local OpenBSD mirror soon.
This is the first stable release from the 3.1 series, which is included
with OpenBSD 6.7. It includes the following changes from 3.0:
* New Features
- Completed initial TLS 1.3 implementation with a completely new state
machine and record layer. TLS 1.3 is now enabled by default for the client
side, with the server side to be enabled in a future release. Note that
the OpenSSL TLS 1.3 API is not yet visible/available.
- Improved cipher suite handling to automatically include TLSv1.3 cipher
suites when they are not explicitly referred to in the cipher string.
- Provided TLSv1.3 cipher suite aliases to match the names used in RFC 8446.
- Added cms subcommand to openssl(1).
- Added -addext option to openssl(1) req subcommand.
- Added -groups option to openssl(1) s_server subcommand.
- Added TLSv1.3 extension types to openssl(1) -tlsextdebug.
* API and Documentation Enhancements
- Added RSA-PSS and RSA-OAEP methods from OpenSSL 1.1.1.
- Ported Cryptographic Message Syntax (CMS) implementation from OpenSSL
1.1.1 and enabled by default.
* Compatibility Changes
- Improved compatibility by backporting functionality and documentation from
OpenSSL 1.1.1.
- Adjusted EVP_chacha20()'s behavior to match OpenSSL's semantics.
* Testing and Proactive Security:
- Added many new additional crypto test vectors.
- Fix to disallow setting the AES-GCM IV length to zero.
* Internal Improvements
- Many more code cleanups, fixes, and improvements to memory handling and
protocol parsing.
* Portable Improvements
- Default CA bundle location is now configurable in portable builds.
- Improved portable builds to support for use of static MSVC runtimes.
- Fixed portable builds to avoid exporting a sleep() symbol.
* Bug Fixes
- Fixed printing the serialNumber with X509_print_ex() fall back to the
colon separated hex bytes in case greater than int value.
The LibreSSL project continues improvement of the codebase to reflect modern,
safe programming practices. We welcome feedback and improvements from the
broader community. Thanks to all of the contributors who helped make this
release possible.
From: Brent Cook
Date: Sat, May 9, 2020 at 1:35 AM
We have released LibreSSL 3.1.1, which will be arriving in the
LibreSSL directory of your local OpenBSD mirror soon.
This is the first stable release from the 3.1 series, which is included
with OpenBSD 6.7. It includes the following changes from 3.0:
* New Features
- Completed initial TLS 1.3 implementation with a completely new state
machine and record layer. TLS 1.3 is now enabled by default for the client
side, with the server side to be enabled in a future release. Note that
the OpenSSL TLS 1.3 API is not yet visible/available.
- Improved cipher suite handling to automatically include TLSv1.3 cipher
suites when they are not explicitly referred to in the cipher string.
- Provided TLSv1.3 cipher suite aliases to match the names used in RFC 8446.
- Added cms subcommand to openssl(1).
- Added -addext option to openssl(1) req subcommand.
- Added -groups option to openssl(1) s_server subcommand.
- Added TLSv1.3 extension types to openssl(1) -tlsextdebug.
* API and Documentation Enhancements
- Added RSA-PSS and RSA-OAEP methods from OpenSSL 1.1.1.
- Ported Cryptographic Message Syntax (CMS) implementation from OpenSSL
1.1.1 and enabled by default.
* Compatibility Changes
- Improved compatibility by backporting functionality and documentation from
OpenSSL 1.1.1.
- Adjusted EVP_chacha20()'s behavior to match OpenSSL's semantics.
* Testing and Proactive Security:
- Added many new additional crypto test vectors.
- Fix to disallow setting the AES-GCM IV length to zero.
* Internal Improvements
- Many more code cleanups, fixes, and improvements to memory handling and
protocol parsing.
* Portable Improvements
- Default CA bundle location is now configurable in portable builds.
- Improved portable builds to support for use of static MSVC runtimes.
- Fixed portable builds to avoid exporting a sleep() symbol.
* Bug Fixes
- Fixed printing the serialNumber with X509_print_ex() fall back to the
colon separated hex bytes in case greater than int value.
The LibreSSL project continues improvement of the codebase to reflect modern,
safe programming practices. We welcome feedback and improvements from the
broader community. Thanks to all of the contributors who helped make this
release possible.
2020年5月6日 星期三
ADMIN: Setting up DevOps Orchestration Platform
REF: https://www.admin-magazine.com/Archive/2020/56/Setting-up-DevOps-Orchestration-Platform
[USN-4341-1] Samba vulnerabilities
---------- Forwarded message ---------
From: Marc Deslauriers
Date: Apr 29, 2020 2:34AM
Andrei Popa discovered that Samba incorrectly handled certain LDAP queries.
A remote attacker could use this issue to cause Samba to crash, resulting
in a denial of service, or possibly execute arbitrary code. This issue only
affected Ubuntu 19.10 and Ubuntu 20.04 LTS. (CVE-2020-10700)
It was discovered that Samba incorrectly handled certain LDAP queries. A
remote attacker could possibly use this issue to cause Samba to consume
resources, resulting in a denial of service. (CVE-2020-10704)
References:
https://usn.ubuntu.com/4341-1
CVE-2020-10700, CVE-2020-10704
From: Marc Deslauriers
Date: Apr 29, 2020 2:34AM
Andrei Popa discovered that Samba incorrectly handled certain LDAP queries.
A remote attacker could use this issue to cause Samba to crash, resulting
in a denial of service, or possibly execute arbitrary code. This issue only
affected Ubuntu 19.10 and Ubuntu 20.04 LTS. (CVE-2020-10700)
It was discovered that Samba incorrectly handled certain LDAP queries. A
remote attacker could possibly use this issue to cause Samba to consume
resources, resulting in a denial of service. (CVE-2020-10704)
References:
https://usn.ubuntu.com/4341-1
CVE-2020-10700, CVE-2020-10704
TrendLabs: Operation Poisoned News: Hong Kong Users Targeted With Mobile Malware via Local News Links
Figure 2. List of news topics posted by the campaign
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/operation-poisoned-news-hong-kong-users-targeted-with-mobile-malware-via-local-news-links/
Cloudflare: Pwned Passwords Padding
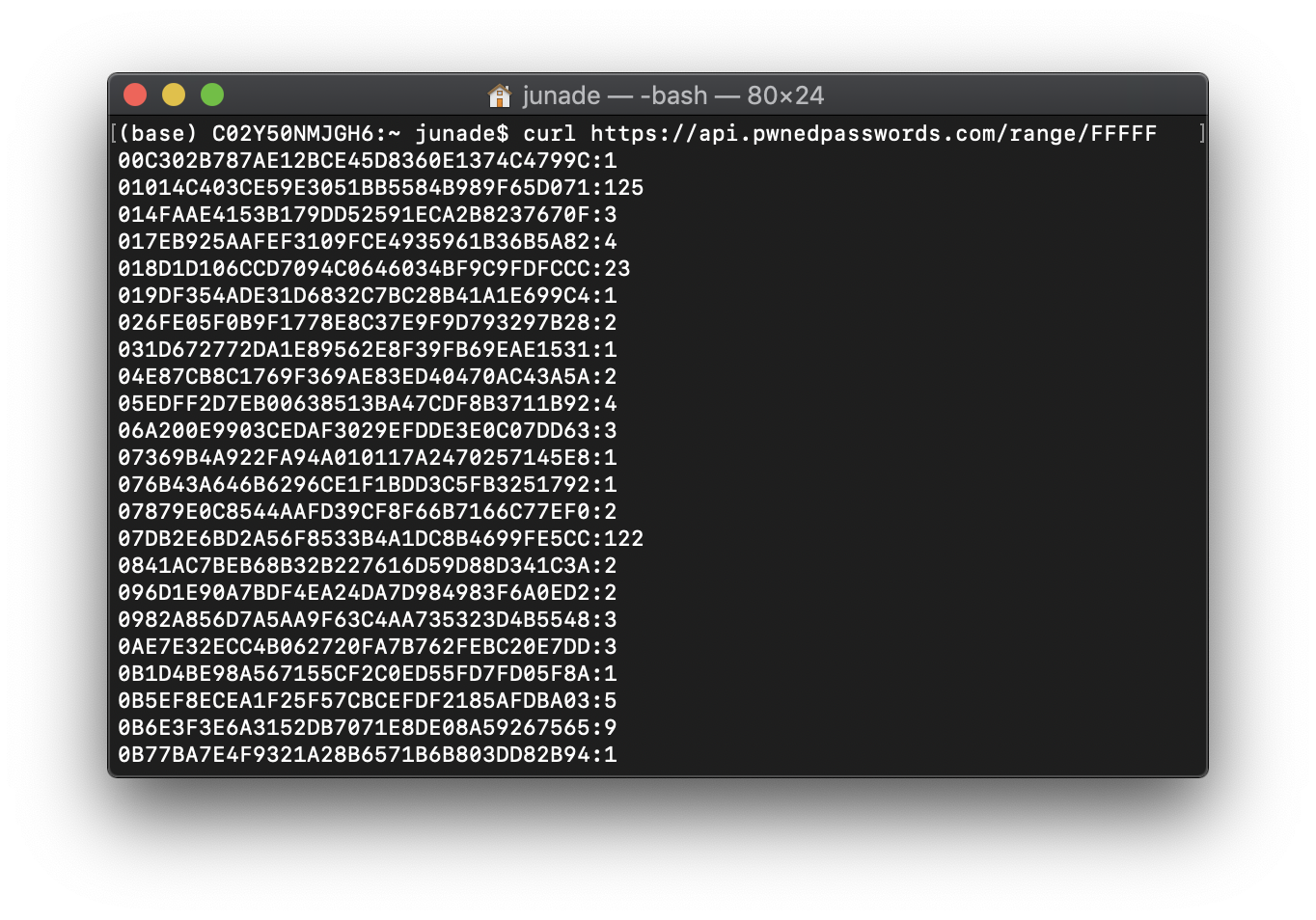
REF: https://blog.cloudflare.com/pwned-passwords-padding-ft-lava-lamps-and-workers/
[USN-4350-1] MySQL vulnerabilities
---------- Forwarded message ---------
From: Marc Deslauriers
Date: May 4, 2020 9:45PM
Multiple security issues were discovered in MySQL and this update includes
new upstream MySQL versions to fix these issues.
MySQL has been updated to 8.0.80 in Ubuntu 19.10 and Ubuntu 20.04 LTS.
Ubuntu 16.04 LTS and Ubuntu 18.04 LTS have been updated to MySQL 5.7.30.
In addition to security fixes, the updated packages contain bug fixes, new
features, and possibly incompatible changes.
Please see the following for more information:
https://dev.mysql.com/doc/relnotes/mysql/5.7/en/news-5-7-30.html
https://dev.mysql.com/doc/relnotes/mysql/8.0/en/news-8-0-20.html
https://www.oracle.com/security-alerts/cpuapr2020.html
References:
https://usn.ubuntu.com/4350-1
CVE-2020-2759, CVE-2020-2760, CVE-2020-2762, CVE-2020-2763,
CVE-2020-2765, CVE-2020-2780, CVE-2020-2804, CVE-2020-2812,
CVE-2020-2892, CVE-2020-2893, CVE-2020-2895, CVE-2020-2896,
CVE-2020-2897, CVE-2020-2898, CVE-2020-2901, CVE-2020-2903,
CVE-2020-2904, CVE-2020-2921, CVE-2020-2922, CVE-2020-2923,
CVE-2020-2924, CVE-2020-2925, CVE-2020-2926, CVE-2020-2928,
CVE-2020-2930
From: Marc Deslauriers
Date: May 4, 2020 9:45PM
Multiple security issues were discovered in MySQL and this update includes
new upstream MySQL versions to fix these issues.
MySQL has been updated to 8.0.80 in Ubuntu 19.10 and Ubuntu 20.04 LTS.
Ubuntu 16.04 LTS and Ubuntu 18.04 LTS have been updated to MySQL 5.7.30.
In addition to security fixes, the updated packages contain bug fixes, new
features, and possibly incompatible changes.
Please see the following for more information:
https://dev.mysql.com/doc/relnotes/mysql/5.7/en/news-5-7-30.html
https://dev.mysql.com/doc/relnotes/mysql/8.0/en/news-8-0-20.html
https://www.oracle.com/security-alerts/cpuapr2020.html
References:
https://usn.ubuntu.com/4350-1
CVE-2020-2759, CVE-2020-2760, CVE-2020-2762, CVE-2020-2763,
CVE-2020-2765, CVE-2020-2780, CVE-2020-2804, CVE-2020-2812,
CVE-2020-2892, CVE-2020-2893, CVE-2020-2895, CVE-2020-2896,
CVE-2020-2897, CVE-2020-2898, CVE-2020-2901, CVE-2020-2903,
CVE-2020-2904, CVE-2020-2921, CVE-2020-2922, CVE-2020-2923,
CVE-2020-2924, CVE-2020-2925, CVE-2020-2926, CVE-2020-2928,
CVE-2020-2930
Roku: 13 new movie releases coming directly to streaming
Check out the highly anticipated, new movies coming to streaming early—like Trolls World Tour, Bloodshot, Pixar’s Onward and much more.
Cloudflare: Seamless remote work with Cloudflare for Teams
訂閱:
文章 (Atom)












