nmap is easy to use for simple simple vulnerability assessment. For example, checking port 445 for preventing SMB attacks from WannaCry:
nmap -PN 192.0.0/24 -p 445 | grep -B 4 "tcp open"
-PN: Treat all hosts as online -- skip host discovery
2017年5月30日 星期二
Linux container socket issue
Container running on Linux such as OpenVZ may encounter socket error issue when the application heavily utilize network socket I/O, very frequent or persistent. For example, Real Time automation for TV operations. Thus, such application may better run on physical machine or a full virtualization, such as KVM instead.


2017年5月28日 星期日
Wana Decrypt0r 2.0 Ransomware
REF: https://community.sophos.com/kb/en-us/126733
What to do
Please ensure all of your Windows environments have been updated as described in Microsoft Security Bulletin MS17-010 - Critical. Microsoft is providing Customer Guidance for WannaCrypt attacks
Microsoft has made the decision to make the Security Update for platforms in custom support only, Windows XP, Windows 8, and Windows Server 2003, broadly available for download:
| Windows Server 2003 SP2 x64 | Windows Server 2003 SP2 x86 | |
| Windows 8 x64 | Windows 8 x86 | |
| Windows XP SP2 x64 | Windows XP SP3 x86 | Windows XP Embedded SP3 x86 |
Applying the Microsoft patches MS17-010 should be enough to protect against the EternalBlue Exploit that enabled the rapid spread of the Wanna ransomware attack. Microsoft and others are advising that customers should consider blocking legacy protocols on their networks in particular SMBv1 as an additional defense-in-depth strategy to further protect against attacks.
Customers considering disabling SMBv1 should proceed with caution since this could cause software and other services that depend on SMB to stop functioning correctly. In particular, please see the following article for information regarding disabling SMBv1 for Sophos products: What to do if you decide to disable SMBv1 as a response to Wanna ransomware
The Wanna malware variants that we have seen include a lookup to a URL. If the malware gets a response, the attack stops. This has been described in some media reports as a “kill switch”. The domain for the URL was registered and activated by an independent malware analyst intending to track the malware, meaning that if current variants of the ransomware can reach the URL the attack would stop.
As a result, the National Cyber Security Centre (NCSC) provide this advice: Finding the kill switch to stop the spread of ransomware. NCSC recommends the following domains be whitelisted in your environment:
- www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
- www[.]ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
2017年5月27日 星期六
Antivirus scans for WannaCry
| SHA256: | 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c |
| File name: | 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c.exe |
| Detection ratio: | 51 / 59 |
| Analysis date: | 2017-05-26 05:07:28 UTC ( 21 hours, 57 minutes ago ) |
REF: https://virustotal.com/en/file/24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c/analysis/
2017年5月26日 星期五
RFC 2196
Abstract This handbook is a guide to developing computer security policies and procedures for sites that have systems on the Internet. The purpose of this handbook is to provide practical guidance to administrators trying to secure their information and services. The subjects covered include policy content and formation, a broad range of technical system and network security topics, and security incident response.
REF: https://www.rfc-editor.org/rfc/rfc2196.txt
Digi-Cloud Alliance
- validated solutions
- modular building blocks
- future looking of composable infrastructure, via API orchestration
- ex Azure IaaS not profitable, but PaaS, IoT ok
- cloud 1.0 : vendor, tech driven; 2.0: user, solution driven
- IoT gateway for data transmission
Edge computing
From wiki:
Edge computing is a method of optimising cloud computing systems by performing data processing at the edge of the network, near the source of the data. This reduces the communications bandwidth needed between sensors and the central datecentre by performing analytics and knowledge generation at or near the source of the data. This approach requires leveraging resources that may not be continuously connected to a network such as laptops, smartphones, tablets and sensors.[1] Edge Computing covers a wide range of technologies including wireless sensor networks, mobile data acquisition, mobile signature analysis, cooperative distributed peer-to-peer ad hoc networking and processing also classifiable as local cloud/fog computing and grid/mesh computing, dew computing,[2] mobile edge computing,[3][4] cloudlet, distributed data storage and retrieval, autonomic self-healing networks, remote cloud services, augmented reality, and more.[5]
REF: https://en.wikipedia.org/wiki/Edge_computing
2017年5月23日 星期二
2017 SAP Forum Taipei
- digital supply chain connected to everything
- changing and reinventing
- real-time BI decision
- if you can't measure it, you can't improve it.
- enterprise level data warehouse
- design thinking
- system for log, for engagement, for innovation
- people, thing, business
- reinvent, reimagine, and four other R
- SAP edge computing filtered then send to cloud, IoT foundation
- Digital Twin
- predictive maintenance management
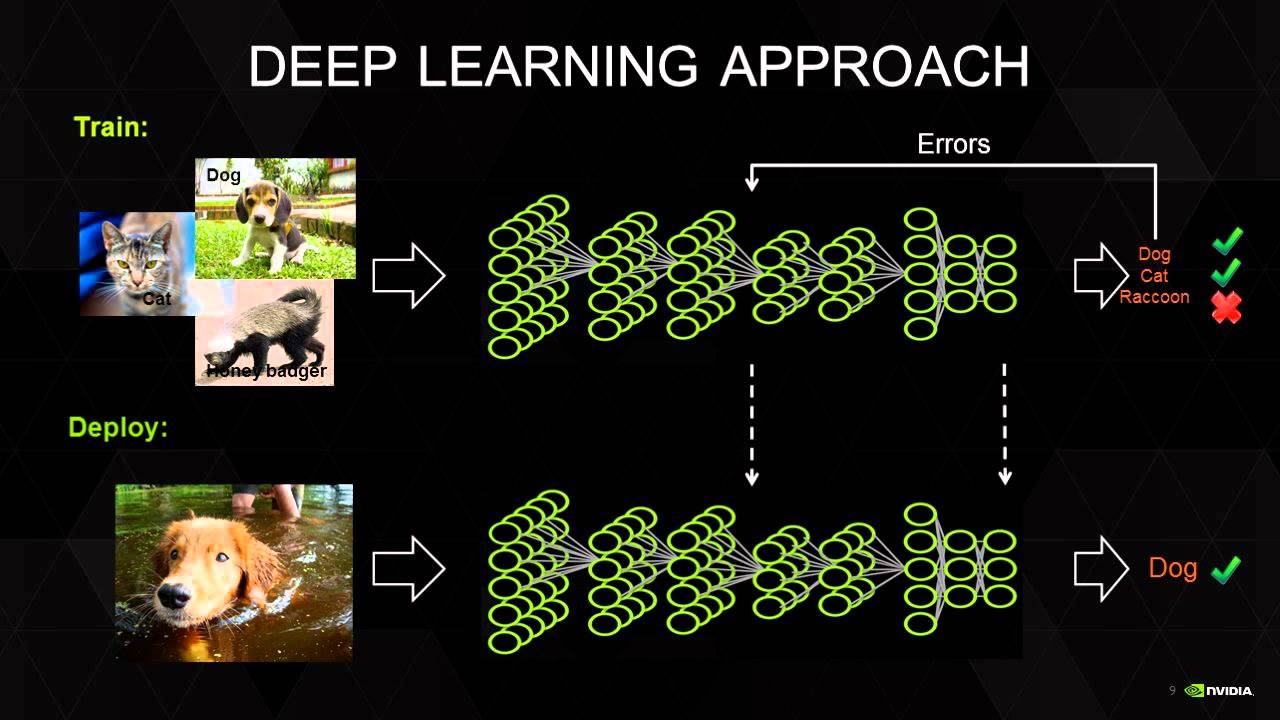
data for deep learning
deep learning actually requires lots of data for training. otherwise won't work.
2017年5月21日 星期日
Conficker, MS08-067
Spread of WannaCry today is similar to Conficker ten years ago...
REF: https://technet.microsoft.com/en-us/security/dd452420.aspx
About Conficker
On October 23, 2008, Microsoft released a critical security update, MS08-067, to resolve a vulnerability in the Server service of Windows that, at the time of release, was facing targeted, limited attack. The vulnerability could allow an anonymous attacker to successfully take full control of a vulnerable system through a network-based attack, the sort of vectors typically associated with network "worms." Since the release of MS08-067, the Microsoft Malware Protection Center (MMPC) has identified the following variants of Win32/Conficker:
- Worm:Win32/Conficker.A: identified by the MMPC on November 21, 2008
- Worm:Win32/Conficker.B: identified by the MMPC on December 29, 2008
- Worm:Win32/Conficker.C: identified by the MMPC on February 20, 2009*
- Worm:Win32/Conficker.D: identified by the MMPC on March 4, 2009**
- Worm:Win32/Conficker.E: identified by the MMPC on April 8, 2009
| *Also known as Conficker B++ | |
| **Also known as Conficker.C and Downadup.C |
Baculum, web UI for Bacula
web UI is available at demo site.

REF: http://blog.bacula.org/baculum-official-rpm-and-deb-package-repositories/
REF: http://blog.bacula.org/baculum-official-rpm-and-deb-package-repositories/
訂閱:
文章 (Atom)
