you can write your own rule for testing snort, or to detect specific pattern you desire. a simple icmp sample as below. sid is needed for newer version.
alert icmp any any -> any any (msg: "ICMP traffic"; sid:001;)
2016年9月30日 星期五
mobile battery
battery power issues may cause mobile devices unable to boot normally. two factors need to be checked:
- USB power outlet on the device. For example, Google support suggests many steps regarding re-plugging power with different ways in their official support. (https://support.google.com/nexus/troubleshooter/3337561?hl=en)
- Battery replacement. Consider replacing battery as a hardware fixing option.
2016年9月28日 星期三
Ping RTA
Average of Ping Round-Trip time (RTA) is a easy way to evaluate your network quality affected by switching, routing, or physical distance. Even an L3 routing may cause double of RTA than within an L2 transport. Longer distance may cause packet loss due to unknown physical issue.
2016年9月27日 星期二
snort as IDS
since network packets or net flows contain too much info to analyze, using packaged IDS such as snort for 1st stage scanning may be a time saver. you can either build from tarball or source rpm. dependencies need to be solved.
REF:
https://www.packet6.com/installing-snort-on-centos/
http://rivald.blogspot.tw/2013/08/building-snort-rpms-on-centos-6x-x8664.html
http://www.lijyyh.com/2012/04/snort.html
REF:
https://www.packet6.com/installing-snort-on-centos/
http://rivald.blogspot.tw/2013/08/building-snort-rpms-on-centos-6x-x8664.html
http://www.lijyyh.com/2012/04/snort.html
2016年9月26日 星期一
RStudio
RStudio is a pretty cool GUI front-end of R. It really helps researchers to do their work more easily : ) Some tutorial (in Chinese) as following.
REF: https://joe11051105.gitbooks.io/r_basic/content/environment_settings/RStudio_introduction.html
REF: https://joe11051105.gitbooks.io/r_basic/content/environment_settings/RStudio_introduction.html
2016年9月25日 星期日
2016年9月24日 星期六
wifi dongle
Using a wifi dongle to bridge 3G/4G signal to its wifi AP may be the cheapest solution as ISP service. However, it requires testing of 1) dongle overheated, as well as 2) 3G/4G receiving status, for a longer time.
Decklink buffer overrun
quote: "This error happens when the decklink card is receiving data faster than it is processing it." We may try assigning more threads to the input and/or output processing.
REF: https://forum.blackmagicdesign.com/viewtopic.php?f=12&t=48141
REF: https://forum.blackmagicdesign.com/viewtopic.php?f=12&t=48141
2016年9月22日 星期四
NVIDIA GTC 2016
Here are some notes from NVIDIA GTC 2016, Taipei:
- 95 pc revolution -> 05 mobile revolution -> 15 AI revolution
- AI revolution started from 2012, calculation usage of GPU.
- realistic ray tracing for simulating real world, not only gaming beauty.
- It's not filtering, but re drawing
2016年9月20日 星期二
Check_MK: custom checks
Custom checks for Check_MK can be performed by defining local checks, which is processed by scripts on checked machines. sample scripts and paths as following from official site.
REF: https://mathias-kettner.de/checkmk_localchecks.html
REF: https://mathias-kettner.de/checkmk_localchecks.html
2016年9月19日 星期一
Microsoft app, part 2
This service will keep on getting users' emails unless it is blocked. It won't stop by removing the app, even if the email accounts is deleted from the app, since the fetching process is handled by cloud service. Here it goes: "We provide a service that indexes and accelerates delivery of your email to your device. That means that our service retrieves your incoming and outgoing email messages and securely pushes them to the app on your device.Similarly, the service retrieves the calendar data and address book contacts associated with your email account and securely pushes those to the app on your device. Those messages, calendar events, and contacts, along with their associated metadata, may be temporarily stored and indexed securely both in our servers and locally on the app on your device. If your emails have attachments and you request to open them in our app, the service retrieves them from the mail server, securely stores them temporarily on our servers, and delivers them to the app.”
REF: https://blog.winkelmeyer.com/2015/01/warning-microsofts-outlook-app-for-ios-breaks-your-company-security/
REF: https://blog.winkelmeyer.com/2015/01/warning-microsofts-outlook-app-for-ios-breaks-your-company-security/
2016年9月18日 星期日
Let’s Encrypt
Let's Encrypt is a very easy to use SSL certificate for your public website. And it's free! Simply download the client, run it (Internet access required), and it will check your https from outside (valid domain name required). Finally your ssl.conf will be modified and you'll get a 3-month cert. A cron job could be used to update the cert. This action complies the requirement of A.10.1 Cryptology of ISO27001:2013 !
REF: https://letsencrypt.org/
REF: https://letsencrypt.org/
2016年9月17日 星期六
LINE lock out
LINE system can lock out users who send abusive messages. The mechanism is similar to any user locks out other user one by one, but applied to *ALL* users in this case: people can send you messages but your messages would *NEVER* reach them.
The banned objects should include the specified phone number, as well as phone hardware serials such as IMEI. Therefore old number, phone, as well as ID and email of the spammer may all encounter access failure for new registration.
The banned objects should include the specified phone number, as well as phone hardware serials such as IMEI. Therefore old number, phone, as well as ID and email of the spammer may all encounter access failure for new registration.
2016年9月16日 星期五
geo mapping
geo mapping for Internet address (e.g. IP) is important for linking virtual space to reality. CSI: Cyber has presented various usage of it in their drama. Some vendors such as Splunk also have Google map support in their products. These maps are worth watching since virtual activities are eventually driven by real human.
REF: https://tw.batchgeo.com/
REF: https://tw.batchgeo.com/
2016年9月15日 星期四
Microsoft app
Microsoft Apps may induce unknown security issue due to various purchase of small 'cloud' companies, which may not respect much about 'privacy'. For example, the new Outlook App will collect user email contents to their EC2 instances (kind of SaaS), which is pretty not OK for strict privacy policies.
REF: https://blog.winkelmeyer.com/2015/01/warning-microsofts-outlook-app-for-ios-breaks-your-company-security/
REF: https://blog.winkelmeyer.com/2015/01/warning-microsofts-outlook-app-for-ios-breaks-your-company-security/
2016年9月14日 星期三
authorities in market
People trust authorities. Authorities define standards. What if one authority becomes monopoly in specific field, its standard becomes unchallenged? For example, audience rate from people meters provided by AGB Nielsen is the primary (or ONLY?) standard for TV commercial pricing in Taiwan. Although a lot of alternative sampling methodology other than people meter exist in the world, local market has no courage to challenge or try other methods for their industry. The lack of evolving auditing (evaluation) mindset creates monopoly, then hinders the industry to keep on this fast-pacing world.
REF: http://technews.tw/2016/09/09/nielsens-dar-tool-for-digital-ad-market/
REF: http://technews.tw/2016/09/09/nielsens-dar-tool-for-digital-ad-market/
2016年9月13日 星期二
LiveCD for ISMS
LiveCD such as KNOPPIX is a useful item in your ISMS toolbox.
- system rescue from CD-ROM. for availability.
- read-only OS from CD-ROM. for integrity.
- RAM-only data processing on the OS from CD-ROM. for confidentiality.
2016年9月12日 星期一
server raid
It's a good idea to use the onboard RAID chipset of server hardware. you can simplt build the RAID array before OS installation. pretty useful especially when limited HDDs are available on rack servers.
spamd zone checks
zone listing by blocks, e.g. countries or companies, would be pretty helpful when using grey listing. you can either white list or black list these blocks as a quick 1st-stage filter, then let spamd do its greylisting later. it would save lots of your time.
2016年9月10日 星期六
Facebook promotion
Facebook promotion would give you at least short-term increase of audience REACH numbers, as the example shown below, where green line indicates the boost of commercial promotion by Facebook. However, you also need to observe the long-term increase of your audience base, the blue line, to evaluate whether the promotion boost can be related with it or not. For this example, the boost seems only related with the promotion period without longer influence.

SDN migration
Although both software-defined, ONIE (Open Network Install Environment, such as Cumulus Linux) and OpenFlow work on different strategies which requires carefully planning for SDN migration from traditional infrastructure.
OpenFlow focuses on centralized resource management, which implies more flexible utilization of abundant networking resources. Thus it won't help if your plan is to increase performance by managing 'limited' resources by software more precisely. Then ONIE solutions which provides more powerful network OS may be your better solution. For example, price of an ONIE switch would fall between traditional L2 and L3 products, so it's good to use ONIE if the use case is more than L2 or L2/L3 combined.
OpenFlow focuses on centralized resource management, which implies more flexible utilization of abundant networking resources. Thus it won't help if your plan is to increase performance by managing 'limited' resources by software more precisely. Then ONIE solutions which provides more powerful network OS may be your better solution. For example, price of an ONIE switch would fall between traditional L2 and L3 products, so it's good to use ONIE if the use case is more than L2 or L2/L3 combined.
2016年9月8日 星期四
metadata for MAM
metadata is very important while building and using MAM or DAM (Media/ Digital Asset Management). "Metadata breaks down the standard linear structure of organising files. Rather than placing assets within a hierarchy, where they can only exist in one place at a time, metadata allows resources to be classified in a variety of ways, simultaneously."
REF: http://www.resourcespace.com/feed?27
REF: http://www.resourcespace.com/feed?27
2016年9月7日 星期三
Amazon Workspaces
Performance of Amazon Workspaces is critically dependent on network speed to their Infra. Otherwise this VDI solution will become so slow for any use case. Besides, it has only English Windows desktop now.
Practical SDN
Cumulus products can contact ovsdb server and set as vtep gateway. If you do not have cloud infra, for example, RedHat OpenStack, SDN or NFV won't be very useful.
REF:
https://www.redhat.com/en/technologies/industries/telecommunications/nfv-platform
REF:
https://www.redhat.com/en/technologies/industries/telecommunications/nfv-platform
spamd for greylisting
Spamd is a very simple yet powerful greylisting mechanism for fighting spam. It forces any newly seen record to re-send emails in certain time period (default: 25 mins), timeout it after some time (default: 4hrs), then accept it as whitelist before timeout. Spammers won't have the patience to wait for the re-send time, and mail servers will re-send emails again and again according to RFC regulations. Indeed, spammers are almost kept out under such restrictions.
However, governments or smaller businesses will also utilize these spam-like tools to send their info, which will be easily blocked or delayed by such mechanism, especially when the mail server doesn't have enough traffic to sample records for whitelist. You will need at least several days or over a week to collect these senders to group, otherwise user experience will be deeply affected by these restriction. GREY list observation is the key!
2016年9月4日 星期日
vxlan as simple SDN
we can utilize vxlan as simple SDN solution, as the man page described below.
DESCRIPTION
The vxlan interface is a tunnelling pseudo-device for overlaying virtualized layer 2 networks over layer 3 networks.
A vxlan interface can be created using the ifconfig vxlanN create command. Once configured, the interface encapsulates and decapsulates Ethernet frames in UDP datagrams that are exchanged with tunnel endpoints. The default UDP port for VXLAN traffic is 4789.
Each vxlan interface uses a 24-bit vnetid (virtual networks identifier) that distinguishes multiple virtualized layer 2 networks and their tunnels between identical tunnel endpoints.
REF: http://man.openbsd.org/vxlan.4
DESCRIPTION
The vxlan interface is a tunnelling pseudo-device for overlaying virtualized layer 2 networks over layer 3 networks.
A vxlan interface can be created using the ifconfig vxlanN create command. Once configured, the interface encapsulates and decapsulates Ethernet frames in UDP datagrams that are exchanged with tunnel endpoints. The default UDP port for VXLAN traffic is 4789.
Each vxlan interface uses a 24-bit vnetid (virtual networks identifier) that distinguishes multiple virtualized layer 2 networks and their tunnels between identical tunnel endpoints.
REF: http://man.openbsd.org/vxlan.4
Check_MK: Active checks
Daemon checks such as SMTP, HTTP services, can be done by active checks setup in Check_MK. Goto WATO -> Rule-Based Configuration of Host & Service Parameters -> Active checks, then configure the checks you need.
REF: https://mathias-kettner.de/checkmk_check_check_smtp.html
REF: https://mathias-kettner.de/checkmk_check_check_smtp.html
AWS IAM
it is a good practice to create several admin accounts via AWS IAM, instead of using ROOT account for everything. Just like that we shouldn't use root on Unix-like systems for daily usage often. Policies for IAM accounts can be attached to grant specific permissions, as below.
2016年9月1日 星期四
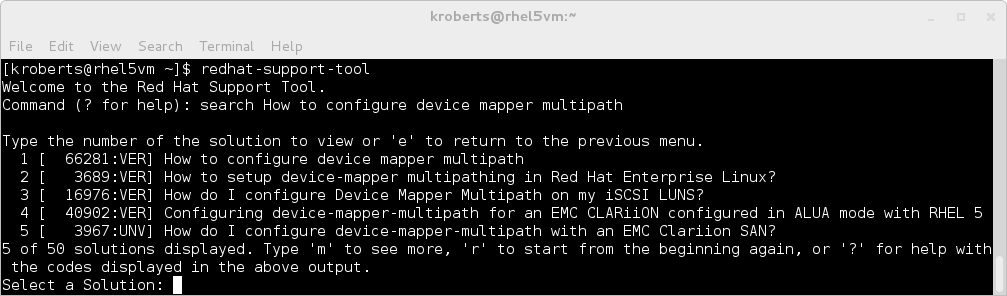
redhat-support-tool
The Red Hat Support Tool,
redhat-support-tool, is both a shell and a single-execution program. The Red Hat Support Tool does not require a graphical interface as it is entirely text based. It can be run over SSH or from any terminal.
The program, by default, will launch into the shell mode where the commands (e.g.,
opencase, btextract, search, etc.) can be called. All commands that are available in the shell mode are also available in single-execution mode (e.g.,redhat-support-tool btextract /path/to/vmcore).
There are some useful convenience features available in the shell mode such as tab command completion and using the '!' to call programs in the parent shell.
Red Hat Support Tool in Shell Mode
Red Hat Support Tool in Non-Interactive Mode
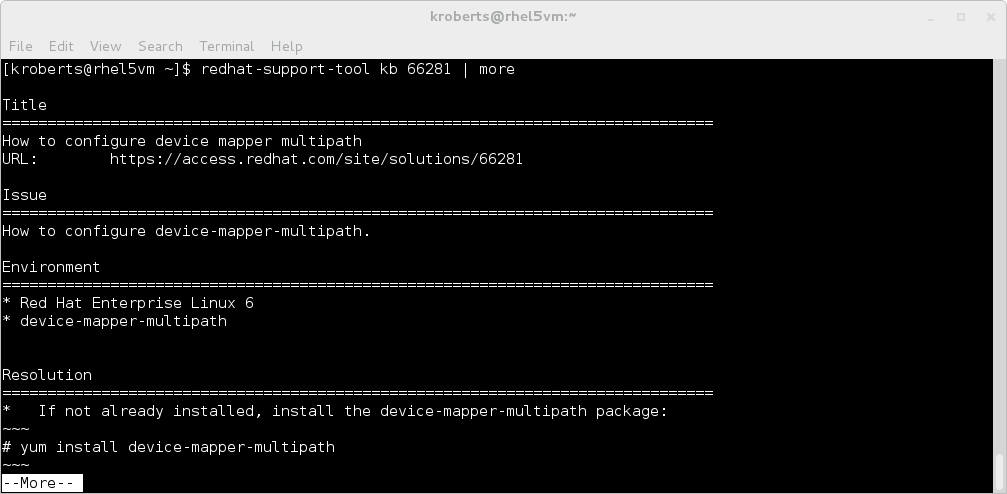
REF: https://access.redhat.com/articles/445443#Installation
訂閱:
文章 (Atom)
