Figure 3. Malicious site purported to be an order review
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/trickbot-watch-arrival-via-redirection-url-in-spam/
2019年5月27日 星期一
ADMIN: Stack Overflow Compromised
The company also admitted that the intruders may have managed to access information on users. “While our overall user database was not compromised, we have identified privileged web requests that the attacker made that could have returned IP address, names, or emails for a very small number of Stack Exchange users. Our team is currently reviewing these logs and will be providing appropriate notifications to any users who are impacted,” said Mary Ferguson, VP of Engineering at Stack Overflow.
REF: http://www.admin-magazine.com/News/Stack-Overflow-Compromised
REF: http://www.admin-magazine.com/News/Stack-Overflow-Compromised
2019年5月26日 星期日
TrendLabs: Dharma Ransomware Uses AV Tool to Distract from Malicious Activities

2019年5月25日 星期六
[USN-3973-1] DHCP vulnerability
---------- Forwarded message ---------
From: Marc Deslauriers
Date: May 13, 2019 11:21PM
It was discovered that DHCP, when built with a mismatched external BIND
library, incorrectly handled certain memory operations. A remote attacker
could possibly use this issue to cause DHCP to crash, resulting in a
denial of service.
References:
https://usn.ubuntu.com/usn/usn-3973-1
CVE-2019-6470
From: Marc Deslauriers
Date: May 13, 2019 11:21PM
It was discovered that DHCP, when built with a mismatched external BIND
library, incorrectly handled certain memory operations. A remote attacker
could possibly use this issue to cause DHCP to crash, resulting in a
denial of service.
References:
https://usn.ubuntu.com/usn/usn-3973-1
CVE-2019-6470
Trello: How To Hack The Anxiety Roadblock And Get More Done

It’s 3 pm on a Friday and you’re pushing towards a 5:00 pm deadline. Your palms are sweating, your heart is going a mile a minute, and you can’t seem to catch your breath.
REF: https://blog.trello.com/hack-anxiety-at-work
TrendLabs: CVE-2019-3396 Redux: Confluence Vulnerability Exploited to Deliver Cryptocurrency Miner With Rootkit

[USN-3975-1] OpenJDK vulnerabilities
---------- Forwarded message ---------
From: Steve Beattie
Date: May 14, 2019 3:57AM
It was discovered that the BigDecimal implementation in OpenJDK performed
excessive computation when given certain values. An attacker could use this
to cause a denial of service (excessive CPU usage). (CVE-2019-2602)
Corwin de Boor and Robert Xiao discovered that the RMI registry
implementation in OpenJDK did not properly select the correct skeleton
class in some situations. An attacker could use this to possibly escape
Java sandbox restrictions. (CVE-2019-2684)
Mateusz Jurczyk discovered a vulnerability in the 2D component of
OpenJDK. An attacker could use this to possibly escape Java sandbox
restrictions. This issue only affected OpenJDK 8 in Ubuntu 16.04
LTS. (CVE-2019-2697)
Mateusz Jurczyk discovered a vulnerability in the font layout engine
of OpenJDK's 2D component. An attacker could use this to possibly
escape Java sandbox restrictions. This issue only affected OpenJDK 8
in Ubuntu 16.04 LTS. (CVE-2019-2698)
References:
https://usn.ubuntu.com/usn/usn-3975-1
CVE-2019-2602, CVE-2019-2684, CVE-2019-2697, CVE-2019-2698
From: Steve Beattie
Date: May 14, 2019 3:57AM
It was discovered that the BigDecimal implementation in OpenJDK performed
excessive computation when given certain values. An attacker could use this
to cause a denial of service (excessive CPU usage). (CVE-2019-2602)
Corwin de Boor and Robert Xiao discovered that the RMI registry
implementation in OpenJDK did not properly select the correct skeleton
class in some situations. An attacker could use this to possibly escape
Java sandbox restrictions. (CVE-2019-2684)
Mateusz Jurczyk discovered a vulnerability in the 2D component of
OpenJDK. An attacker could use this to possibly escape Java sandbox
restrictions. This issue only affected OpenJDK 8 in Ubuntu 16.04
LTS. (CVE-2019-2697)
Mateusz Jurczyk discovered a vulnerability in the font layout engine
of OpenJDK's 2D component. An attacker could use this to possibly
escape Java sandbox restrictions. This issue only affected OpenJDK 8
in Ubuntu 16.04 LTS. (CVE-2019-2698)
References:
https://usn.ubuntu.com/usn/usn-3975-1
CVE-2019-2602, CVE-2019-2684, CVE-2019-2697, CVE-2019-2698
Trello: Here's Proof That Office Layout Doesn't Affect Productivity

There has long been a heated debate as to which type of workplace layout is the best for productivity: Cubicles? Open office? Anywhere in the world?
REF: https://blog.trello.com/office-layout-productivity
TrendLabs: Emotet Adds New Evasion Technique and Uses Connected Devices as Proxy C&C Servers
Figure 6. Login page of a compromised DVR
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/emotet-adds-new-evasion-technique-and-uses-connected-devices-as-proxy-cc-servers/
[USN-3976-1] Samba vulnerability
---------- Forwarded message ---------
From: Marc Deslauriers
Date: May 14, 2019 9:12PM
Isaac Boukris and Andrew Bartlett discovered that Samba incorrectly checked
S4U2Self packets. In certain environments, a remote attacker could possibly
use this issue to escalate privileges.
References:
https://usn.ubuntu.com/usn/usn-3976-1
CVE-2018-16860
From: Marc Deslauriers
Date: May 14, 2019 9:12PM
Isaac Boukris and Andrew Bartlett discovered that Samba incorrectly checked
S4U2Self packets. In certain environments, a remote attacker could possibly
use this issue to escalate privileges.
References:
https://usn.ubuntu.com/usn/usn-3976-1
CVE-2018-16860
Trello: How to Stay Productive With An Irregular (Even Unpredictable) Schedule

There’s a lot of content out there about productivity.
You can find tips like turning off alerts, tackling tasks in batches, and writing out a physical to-do list everywhere. The vast majority of that advice arises with the traditional workday in mind—it’s designed for knowledge workers who sit at a desk from 9 AM to 5 PM every Monday through Friday.
REF: https://blog.trello.com/manage-productivity-unpredictable-schedule
TrendLabs: AESDDoS Botnet Malware Exploits CVE-2019-3396 to Perform Remote Code Execution, DDoS Attacks, and Cryptocurrency Mining
Figure 4. Code snippet showing the AESDDoS variant stealing an affected system’s CPU information
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/aesddos-botnet-malware-exploits-cve-2019-3396-to-perform-remote-code-execution-ddos-attacks-and-cryptocurrency-mining/
[USN-3978-1] QEMU update
---------- Forwarded message ---------
From: Steve Beattie
Date: May 15, 2019 2:43AM
Ke Sun, Henrique Kawakami, Kekai Hu, Rodrigo Branco, Giorgi Maisuradze, Dan
Horea Lutas, Andrei Lutas, Volodymyr Pikhur, Stephan van Schaik, Alyssa
Milburn, Sebastian Österlund, Pietro Frigo, Kaveh Razavi, Herbert Bos,
Cristiano Giuffrida, Moritz Lipp, Michael Schwarz, and Daniel Gruss
discovered that memory previously stored in microarchitectural fill buffers
of an Intel CPU core may be exposed to a malicious process that is
executing on the same CPU core. A local attacker could use this to expose
sensitive information. (CVE-2018-12130)
Brandon Falk, Ke Sun, Henrique Kawakami, Kekai Hu, Rodrigo Branco, Stephan
van Schaik, Alyssa Milburn, Sebastian Österlund, Pietro Frigo, Kaveh
Razavi, Herbert Bos, and Cristiano Giuffrida discovered that memory
previously stored in microarchitectural load ports of an Intel CPU core may
be exposed to a malicious process that is executing on the same CPU core. A
local attacker could use this to expose sensitive information.
(CVE-2018-12127)
Ke Sun, Henrique Kawakami, Kekai Hu, Rodrigo Branco, Marina Minkin, Daniel
Moghimi, Moritz Lipp, Michael Schwarz, Jo Van Bulck, Daniel Genkin, Daniel
Gruss, Berk Sunar, Frank Piessens, and Yuval Yarom discovered that memory
previously stored in microarchitectural store buffers of an Intel CPU core
may be exposed to a malicious process that is executing on the same CPU
core. A local attacker could use this to expose sensitive information.
(CVE-2018-12126)
Kurtis Miller discovered that a buffer overflow existed in QEMU when
loading a device tree blob. A local attacker could use this to execute
arbitrary code. (CVE-2018-20815)
Ke Sun, Henrique Kawakami, Kekai Hu, Rodrigo Branco, Volodrmyr Pikhur,
Moritz Lipp, Michael Schwarz, Daniel Gruss, Stephan van Schaik, Alyssa
Milburn, Sebastian Österlund, Pietro Frigo, Kaveh Razavi, Herbert Bos, and
Cristiano Giuffrida discovered that uncacheable memory previously stored in
microarchitectural buffers of an Intel CPU core may be exposed to a
malicious process that is executing on the same CPU core. A local attacker
could use this to expose sensitive information. (CVE-2019-11091)
It was discovered that a NULL pointer dereference existed in the sun4u
power device implementation in QEMU. A local attacker could use this
to cause a denial of service. This issue only affected Ubuntu 18.10
and Ubuntu 19.04. (CVE-2019-5008)
William Bowling discovered that an information leak existed in the SLiRP
networking implementation of QEMU. An attacker could use this to expose
sensitive information. (CVE-2019-9824)
References:
https://usn.ubuntu.com/usn/usn-3978-1
CVE-2018-12126, CVE-2018-12127, CVE-2018-12130, CVE-2018-20815,
CVE-2019-11091, CVE-2019-5008, CVE-2019-9824,
https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/MDS
From: Steve Beattie
Date: May 15, 2019 2:43AM
Ke Sun, Henrique Kawakami, Kekai Hu, Rodrigo Branco, Giorgi Maisuradze, Dan
Horea Lutas, Andrei Lutas, Volodymyr Pikhur, Stephan van Schaik, Alyssa
Milburn, Sebastian Österlund, Pietro Frigo, Kaveh Razavi, Herbert Bos,
Cristiano Giuffrida, Moritz Lipp, Michael Schwarz, and Daniel Gruss
discovered that memory previously stored in microarchitectural fill buffers
of an Intel CPU core may be exposed to a malicious process that is
executing on the same CPU core. A local attacker could use this to expose
sensitive information. (CVE-2018-12130)
Brandon Falk, Ke Sun, Henrique Kawakami, Kekai Hu, Rodrigo Branco, Stephan
van Schaik, Alyssa Milburn, Sebastian Österlund, Pietro Frigo, Kaveh
Razavi, Herbert Bos, and Cristiano Giuffrida discovered that memory
previously stored in microarchitectural load ports of an Intel CPU core may
be exposed to a malicious process that is executing on the same CPU core. A
local attacker could use this to expose sensitive information.
(CVE-2018-12127)
Ke Sun, Henrique Kawakami, Kekai Hu, Rodrigo Branco, Marina Minkin, Daniel
Moghimi, Moritz Lipp, Michael Schwarz, Jo Van Bulck, Daniel Genkin, Daniel
Gruss, Berk Sunar, Frank Piessens, and Yuval Yarom discovered that memory
previously stored in microarchitectural store buffers of an Intel CPU core
may be exposed to a malicious process that is executing on the same CPU
core. A local attacker could use this to expose sensitive information.
(CVE-2018-12126)
Kurtis Miller discovered that a buffer overflow existed in QEMU when
loading a device tree blob. A local attacker could use this to execute
arbitrary code. (CVE-2018-20815)
Ke Sun, Henrique Kawakami, Kekai Hu, Rodrigo Branco, Volodrmyr Pikhur,
Moritz Lipp, Michael Schwarz, Daniel Gruss, Stephan van Schaik, Alyssa
Milburn, Sebastian Österlund, Pietro Frigo, Kaveh Razavi, Herbert Bos, and
Cristiano Giuffrida discovered that uncacheable memory previously stored in
microarchitectural buffers of an Intel CPU core may be exposed to a
malicious process that is executing on the same CPU core. A local attacker
could use this to expose sensitive information. (CVE-2019-11091)
It was discovered that a NULL pointer dereference existed in the sun4u
power device implementation in QEMU. A local attacker could use this
to cause a denial of service. This issue only affected Ubuntu 18.10
and Ubuntu 19.04. (CVE-2019-5008)
William Bowling discovered that an information leak existed in the SLiRP
networking implementation of QEMU. An attacker could use this to expose
sensitive information. (CVE-2019-9824)
References:
https://usn.ubuntu.com/usn/usn-3978-1
CVE-2018-12126, CVE-2018-12127, CVE-2018-12130, CVE-2018-20815,
CVE-2019-11091, CVE-2019-5008, CVE-2019-9824,
https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/MDS
Plex: With great power comes great responsibility
| Ever get home and your server’s fan sounds like a Harrier jet takeoff in a Category 4 hurricane? Are some of your viewers watching “Spider-Man” a few times too many? Well, we wanted to give you some further insight and figured out a way to give your admin console some delightful new powers (without the pain of a radioactive spider bite): |
|
| Simply open your dashboard in the web app to access these. |
TrendLabs: Tech Support Scam Employs New Trick by Using Iframe to Freeze Browsers
[LSN-0051-1] Linux kernel vulnerability
---------- Forwarded message ---------
From:
Date: May 15, 2019 2:43AM
On May 14, fixes for CVE-2018-12126, CVE-2018-12127, CVE-2018-12130,
and CVE-2019-11091 were released into the Ubuntu Xenial and Bionic
kernels. These CVEs are security vulnerabilities caused by flaws in the
design of speculative execution hardware in the computer's CPU.
Researchers discovered that memory contents previously stored in
microarchitectural buffers of an Intel CPU core may be visible to other
processes running on the same core.
Details on the vulnerability and our response can be found here:
https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/MDS
Due to the high complexity of the fixes and the need for a corresponding
CPU microcode update for a complete fix, we are unable to livepatch these
CVEs. Please plan to reboot into an updated kernel as soon as possible.
References:
CVE-2018-12126, CVE-2018-12127, CVE-2018-12130, and CVE-2019-11091
From:
Date: May 15, 2019 2:43AM
On May 14, fixes for CVE-2018-12126, CVE-2018-12127, CVE-2018-12130,
and CVE-2019-11091 were released into the Ubuntu Xenial and Bionic
kernels. These CVEs are security vulnerabilities caused by flaws in the
design of speculative execution hardware in the computer's CPU.
Researchers discovered that memory contents previously stored in
microarchitectural buffers of an Intel CPU core may be visible to other
processes running on the same core.
Details on the vulnerability and our response can be found here:
https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/MDS
Due to the high complexity of the fixes and the need for a corresponding
CPU microcode update for a complete fix, we are unable to livepatch these
CVEs. Please plan to reboot into an updated kernel as soon as possible.
References:
CVE-2018-12126, CVE-2018-12127, CVE-2018-12130, and CVE-2019-11091
Trello: What's Executive Presence? The Art And Science Of Getting Ahead At Work

Does this story sound familiar?
Rena has had a great pedigree and a successful career, first as an engineer, then as a product manager and later, a director at a fashionable tech company. She was gunning for a Vice President role but was told by her boss that she was missing executive presence and the promotion was then given to her male peer. A month later, Rena was hired by a competitor for the same type of role she was passed on. She was happy about the new gig but was also feeling very confused by the mixed messaging:
“[Executive presence] seems so nebulous, everyone seems to want it in their execs but no one can quite define what it is! I am trying to figure out whether I have it, and if not, what I can do to develop ‘it.’ But first, I need to wrap my head around what ‘it’ is.”
REF: https://blog.trello.com/executive-presence-leadership-at-work
TrendLabs: Uncovering CVE-2019-0232: A Remote Code Execution Vulnerability in Apache Tomcat
Figure 1. Command line string for Windows
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/uncovering-cve-2019-0232-a-remote-code-execution-vulnerability-in-apache-tomcat/
[USN-3977-1] Intel Microcode update
---------- Forwarded message ---------
From: Steve Beattie
Date: May 15, 2019 2:43AM
Ke Sun, Henrique Kawakami, Kekai Hu, Rodrigo Branco, Giorgi Maisuradze, Dan
Horea Lutas, Andrei Lutas, Volodymyr Pikhur, Stephan van Schaik, Alyssa
Milburn, Sebastian Österlund, Pietro Frigo, Kaveh Razavi, Herbert Bos,
Cristiano Giuffrida, Moritz Lipp, Michael Schwarz, and Daniel Gruss
discovered that memory previously stored in microarchitectural fill buffers
of an Intel CPU core may be exposed to a malicious process that is
executing on the same CPU core. A local attacker could use this to expose
sensitive information. (CVE-2018-12130)
Brandon Falk, Ke Sun, Henrique Kawakami, Kekai Hu, Rodrigo Branco, Stephan
van Schaik, Alyssa Milburn, Sebastian Österlund, Pietro Frigo, Kaveh
Razavi, Herbert Bos, and Cristiano Giuffrida discovered that memory
previously stored in microarchitectural load ports of an Intel CPU core may
be exposed to a malicious process that is executing on the same CPU core. A
local attacker could use this to expose sensitive information.
(CVE-2018-12127)
Ke Sun, Henrique Kawakami, Kekai Hu, Rodrigo Branco, Marina Minkin, Daniel
Moghimi, Moritz Lipp, Michael Schwarz, Jo Van Bulck, Daniel Genkin, Daniel
Gruss, Berk Sunar, Frank Piessens, and Yuval Yarom discovered that memory
previously stored in microarchitectural store buffers of an Intel CPU core
may be exposed to a malicious process that is executing on the same CPU
core. A local attacker could use this to expose sensitive information.
(CVE-2018-12126)
Ke Sun, Henrique Kawakami, Kekai Hu, Rodrigo Branco, Volodrmyr Pikhur,
Moritz Lipp, Michael Schwarz, Daniel Gruss, Stephan van Schaik, Alyssa
Milburn, Sebastian Österlund, Pietro Frigo, Kaveh Razavi, Herbert Bos, and
Cristiano Giuffrida discovered that uncacheable memory previously stored in
microarchitectural buffers of an Intel CPU core may be exposed to a
malicious process that is executing on the same CPU core. A local attacker
could use this to expose sensitive information. (CVE-2019-11091)
References:
https://usn.ubuntu.com/usn/usn-3977-1
CVE-2018-12126, CVE-2018-12127, CVE-2018-12130, CVE-2019-11091,
https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/MDS
From: Steve Beattie
Date: May 15, 2019 2:43AM
Ke Sun, Henrique Kawakami, Kekai Hu, Rodrigo Branco, Giorgi Maisuradze, Dan
Horea Lutas, Andrei Lutas, Volodymyr Pikhur, Stephan van Schaik, Alyssa
Milburn, Sebastian Österlund, Pietro Frigo, Kaveh Razavi, Herbert Bos,
Cristiano Giuffrida, Moritz Lipp, Michael Schwarz, and Daniel Gruss
discovered that memory previously stored in microarchitectural fill buffers
of an Intel CPU core may be exposed to a malicious process that is
executing on the same CPU core. A local attacker could use this to expose
sensitive information. (CVE-2018-12130)
Brandon Falk, Ke Sun, Henrique Kawakami, Kekai Hu, Rodrigo Branco, Stephan
van Schaik, Alyssa Milburn, Sebastian Österlund, Pietro Frigo, Kaveh
Razavi, Herbert Bos, and Cristiano Giuffrida discovered that memory
previously stored in microarchitectural load ports of an Intel CPU core may
be exposed to a malicious process that is executing on the same CPU core. A
local attacker could use this to expose sensitive information.
(CVE-2018-12127)
Ke Sun, Henrique Kawakami, Kekai Hu, Rodrigo Branco, Marina Minkin, Daniel
Moghimi, Moritz Lipp, Michael Schwarz, Jo Van Bulck, Daniel Genkin, Daniel
Gruss, Berk Sunar, Frank Piessens, and Yuval Yarom discovered that memory
previously stored in microarchitectural store buffers of an Intel CPU core
may be exposed to a malicious process that is executing on the same CPU
core. A local attacker could use this to expose sensitive information.
(CVE-2018-12126)
Ke Sun, Henrique Kawakami, Kekai Hu, Rodrigo Branco, Volodrmyr Pikhur,
Moritz Lipp, Michael Schwarz, Daniel Gruss, Stephan van Schaik, Alyssa
Milburn, Sebastian Österlund, Pietro Frigo, Kaveh Razavi, Herbert Bos, and
Cristiano Giuffrida discovered that uncacheable memory previously stored in
microarchitectural buffers of an Intel CPU core may be exposed to a
malicious process that is executing on the same CPU core. A local attacker
could use this to expose sensitive information. (CVE-2019-11091)
References:
https://usn.ubuntu.com/usn/usn-3977-1
CVE-2018-12126, CVE-2018-12127, CVE-2018-12130, CVE-2019-11091,
https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/MDS
2019年5月9日 星期四
New Spleen font for OpenBSD 6.5 console
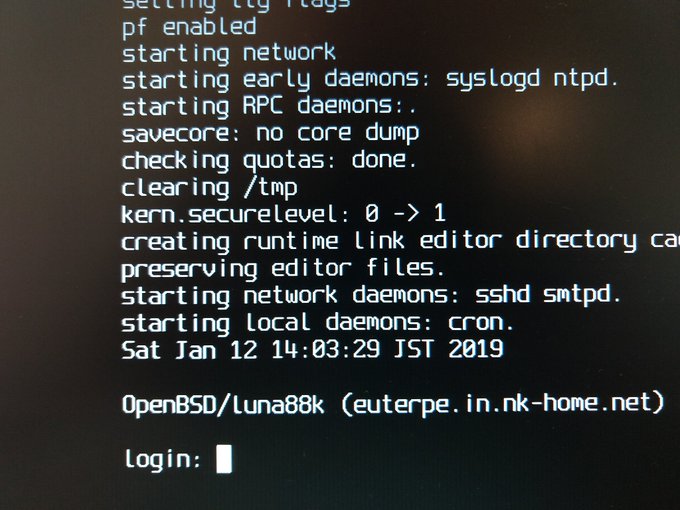
REF: https://mobile.twitter.com/ao_kenji/status/1083956639076560896
2019年5月8日 星期三
Updated Debian 9: 9.9 released
---------- Forwarded message ---------
From: Laura Arjona Reina
Date: Apr 27, 2019 9:52PM
Subject: Updated Debian 9: 9.9 released
------------------------------------------------------------------------
The Debian Project https://www.debian.org/
Updated Debian 9: 9.9 released press@debian.org
April 27th, 2019 https://www.debian.org/News/2019/20190427
------------------------------------------------------------------------
The Debian project is pleased to announce the ninth update of its stable
distribution Debian 9 (codename "stretch"). This point release mainly
adds corrections for security issues, along with a few adjustments for
serious problems. Security advisories have already been published
separately and are referenced where available.
Please note that the point release does not constitute a new version of
Debian 9 but only updates some of the packages included. There is no
need to throw away old "stretch" media. After installation, packages can
be upgraded to the current versions using an up-to-date Debian mirror.
Those who frequently install updates from security.debian.org won't have
to update many packages, and most such updates are included in the point
release.
New installation images will be available soon at the regular locations.
Upgrading an existing installation to this revision can be achieved by
pointing the package management system at one of Debian's many HTTP
mirrors. A comprehensive list of mirrors is available at:
https://www.debian.org/mirror/list
As a special case for this point release, those using the "apt-get" tool
to perform the upgrade will need to ensure that the "dist-upgrade"
command is used, in order to update to the latest kernel packages. Users
of other tools such as "apt" and "aptitude" should use the "upgrade"
command.
From: Laura Arjona Reina
Date: Apr 27, 2019 9:52PM
Subject: Updated Debian 9: 9.9 released
------------------------------------------------------------------------
The Debian Project https://www.debian.org/
Updated Debian 9: 9.9 released press@debian.org
April 27th, 2019 https://www.debian.org/News/2019/20190427
------------------------------------------------------------------------
The Debian project is pleased to announce the ninth update of its stable
distribution Debian 9 (codename "stretch"). This point release mainly
adds corrections for security issues, along with a few adjustments for
serious problems. Security advisories have already been published
separately and are referenced where available.
Please note that the point release does not constitute a new version of
Debian 9 but only updates some of the packages included. There is no
need to throw away old "stretch" media. After installation, packages can
be upgraded to the current versions using an up-to-date Debian mirror.
Those who frequently install updates from security.debian.org won't have
to update many packages, and most such updates are included in the point
release.
New installation images will be available soon at the regular locations.
Upgrading an existing installation to this revision can be achieved by
pointing the package management system at one of Debian's many HTTP
mirrors. A comprehensive list of mirrors is available at:
https://www.debian.org/mirror/list
As a special case for this point release, those using the "apt-get" tool
to perform the upgrade will need to ensure that the "dist-upgrade"
command is used, in order to update to the latest kernel packages. Users
of other tools such as "apt" and "aptitude" should use the "upgrade"
command.
TrendLabs: Zero-day XML External Entity (XXE) Injection Vulnerability in Internet Explorer Can Let Attackers Steal Files, System Info
[Openvpn-announce] New OpenVPN 2.4.7 Windows installers released
---------- Forwarded message ---------
From: Samuli Seppänen
Date: Wed, Apr 24, 2019 at 6:55 PM
New OpenVPN Windows installers have been released. The release
highlights are:
- Latest openvpn-gui
- Latest openvpnserv2 (OpenVPNService)
- Latest tap-windows6 driver
- ARM64 support
- NDIS 6.30 support
- other enhancements
- fix to local privilege exploit vulnerability
...
For further details see the download page:
https://openvpn.net/community-downloads/
From: Samuli Seppänen
Date: Wed, Apr 24, 2019 at 6:55 PM
New OpenVPN Windows installers have been released. The release
highlights are:
- Latest openvpn-gui
- Latest openvpnserv2 (OpenVPNService)
- Latest tap-windows6 driver
- ARM64 support
- NDIS 6.30 support
- other enhancements
- fix to local privilege exploit vulnerability
...
For further details see the download page:
https://openvpn.net/community-downloads/
Trello: Why Self-Care Is The Secret To Becoming A Productivity Powerhouse

When it comes to productivity, most people think the key to getting ahead is doing more. More work, more clients, more time… just more. And when you’re stuck in this mindset of “more, more, more,” it can feel impossible to step away and find time for yourself.
REF: https://blog.trello.com/self-care-for-productivity
TrendLabs: Potential Targeted Attack Uses AutoHotkey and Malicious Script Embedded in Excel File to Avoid Detection
[USN-3957-1] MySQL vulnerabilities
---------- Forwarded message ---------
From: Marc Deslauriers
Date: Apr 29, 2019 9:42PM
Multiple security issues were discovered in MySQL and this update includes
a new upstream MySQL version to fix these issues.
Please see the following for more information:
https://dev.mysql.com/doc/relnotes/mysql/5.7/en/news-5-7-26.html
https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html
References:
https://usn.ubuntu.com/usn/usn-3957-1
CVE-2019-2566, CVE-2019-2581, CVE-2019-2592, CVE-2019-2614,
CVE-2019-2627, CVE-2019-2628, CVE-2019-2632, CVE-2019-2683
From: Marc Deslauriers
Date: Apr 29, 2019 9:42PM
Multiple security issues were discovered in MySQL and this update includes
a new upstream MySQL version to fix these issues.
Please see the following for more information:
https://dev.mysql.com/doc/relnotes/mysql/5.7/en/news-5-7-26.html
https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html
References:
https://usn.ubuntu.com/usn/usn-3957-1
CVE-2019-2566, CVE-2019-2581, CVE-2019-2592, CVE-2019-2614,
CVE-2019-2627, CVE-2019-2628, CVE-2019-2632, CVE-2019-2683
Plexcerpts – a recurring newsletter of updates to Plex.
| Welcome to Plexcerpts – a recurring newsletter of updates to Plex. Now you might ask, “Why did you name the newsletter Plexcerpts?” Like an "excerpt,” we'll highlight some smaller pieces of info from various feature or app releases we've recently made. Basically, it’s a chance to let you in on some of the cool things we’ve been cooking up that you might have otherwise missed. |
TrendLabs: Analysis: Abuse of Custom Actions in Windows Installer MSI to Run Malicious JavaScript, VBScript, and PowerShell Scripts
Figure 2. From Orca MSI Editor: CustomAction that contains JavaScript
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/analysis-abuse-of-custom-actions-in-windows-installer-msi-to-run-malicious-javascript-vbscript-and-powershell-scripts/
訂閱:
意見 (Atom)







