REF: http://www.admin-magazine.com/News/VMware-Brings-Its-Cloud-to-AWS
At the VMware World Conference, VMware announced the arrival of VMware cloud to AWS. VMware will be selling and supporting the service as an on-demand, elastically scalable cloud service. This announcement is the culmination of the strategic partnership that the two companies forged last October.
2017年8月31日 星期四
TrendLabs: USB Malware Implicated in Fileless Attacks

Figure 1. Infection chain
REF: http://blog.trendmicro.com/trendlabs-security-intelligence/usb-malware-implicated-fileless-attacks/
Fully IP Turnkey Vizrt Playout System

The NVG1 NewTek-Vizrt IP Graphics Server comes complete with:
• Real-time animated 3D graphics
• NDI® IP connectivity
• 4K UHD resolution
• TriCaster® TC1 and NewTek IP Series integration
• Ready-made templates & more
With NVG1, high-end graphics playout is now within reach.
REF: https://newtek.com/nvg1/
2017年8月27日 星期日
Google CLoud Free Tier
Always Free Usage Limits
As part of the Google Cloud Platform Free Tier, Compute Engine offers an amount of usage that is free to use, up to a specific limit. These free usage limits are always available even during and after the free trial period. If you go over these usage limits and are no longer in the free trial period, you will be charged according to the price sheet.
- 1 f1-micro VM instance per month (US regions, excluding Northern Virginia).
- 30 GB of Standard persistent disk storage per month.
- 5 GB of snapshot storage per month.
- 1 GB egress from North America to other destinations per month (excluding Australia and China).
2017年8月26日 星期六
Check_MK: Backup and Restore
What happens at Backup & Restore
The following files and directories go into your backup - and will be replaced completely by a restore:
- the main configuration file (main.mk)
- the final configuration file final.mk, if present
- all files in your configuration subdirectory conf.d, if present
- automatically inventorized checks (usually /var/lib/check_mk/autochecks)
- current performance counters (usually /var/lib/check_mk/counters)
- stored logfiles of logwatch (usually /var/lib/check_mk/logwatch)
- cached files from the agents (usually /var/lib/check_mk/cache)
REF: https://mathias-kettner.de/checkmk_backup.html
Google Cloud Platform is the PaaS leader
According to the report, an insight PaaS makes it easier to:
- Manage and access large, complex data sets
- Update and evolve applications that deliver insight at the moment of action
- Update and upgrade technology
- Integrate and coordinate team member activities
REF: https://cloudplatform.googleblog.com/2017/08/independent-research-firm-names-Google-Cloud-the-Insight-Platform-as-PaaS-Leader.html
2017年8月24日 星期四
Live News Production Simplified
In 2014, NewsMaker Systems recognized the NewTek TriCaster’s integrated production system potential to be the single device it could control in an MOS-based newsroom system. The company began working with the development and technical teams at NewTek to integrate Tricaster with a suite of NewsMaker Systems solutions to be used in live newscast environments.

1970’s IBM computer used by Dean Kolkey and Tony Chick.
REF: http://blog.newtek.com/blog/2017/08/02/live-news-production-simplified/
REF: http://blog.newtek.com/blog/2017/08/02/live-news-production-simplified/
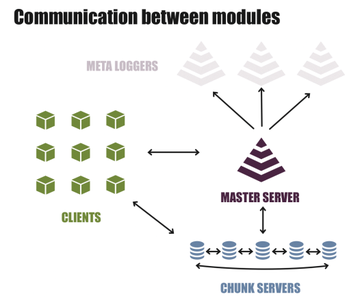
Software-defined storage with LizardFS
2017年8月22日 星期二
BET Betting Big on IP Workflows

In 1980, BET (Black Entertainment Television) became the first television network in the United States primarily devoted to African-American viewers.
In 1991, the network’s then-parent company became the first black-owned company to be traded on the New York Stock Exchange.
And recently, the network scored another first, this time in technology adoption – enabling it to stake its claim among the pioneers of IP-based production workflows.
REF: http://blog.newtek.com/blog/2017/08/11/bet-betting-big-on-ip-workflows/
ISO 27001 compliance for DAM vendor

Unless you're involved in the technical side of your organisation, you may not have heard of ISO 27001. However, this is a very important term to be aware of when it comes to protecting sensitive company data and files.
REF: http://www.resourcespace.com/feed?49
2017年8月20日 星期日
Connected Car Vulnerabilities
Figure 1. A typical CAN network diagram (*1)
REF: http://blog.trendmicro.com/trendlabs-security-intelligence/connected-car-hack/
OSSEC HIDS system
OSSEC is an Open Source Host-based Intrusion Detection System. It performs log analysis, integrity checking, Windows registry monitoring, rootkit detection, real-time alerting and active response. It runs on most operating systems, including Linux, OpenBSD, FreeBSD, Mac OS X, Solaris and Windows. A list with all supported platforms is available at: Supported Systems
REF: https://ossec.github.io/docs/
REF: https://ossec.github.io/docs/
2017年8月18日 星期五
SIEM or Log Management
...there is confusion about “what is a SIEM?” vs “what is a log manager?” It is entirely possible that your IT and security requirements call for log aggregation and rapid log search – and for nothing else (so you only need log management). It is just as possible that they call for a robust real-time monitoring based on correlation and analytics, lots of security dashboards, etc (so you need both SIEM and log management, as we say here, and also perhaps a UEBA).
REF: http://blogs.gartner.com/anton-chuvakin/2017/07/26/siem-or-log-management/
REF: http://blogs.gartner.com/anton-chuvakin/2017/07/26/siem-or-log-management/
2017年8月17日 星期四
New Malware Abuses PowerPoint Slide Show
Figure 1: Infection flow for TROJ_CVE20170199.JVU
REF: http://blog.trendmicro.com/trendlabs-security-intelligence/cve-2017-0199-new-malware-abuses-powerpoint-slide-show/
Backdoor-carrying Emails to Russian-speaking Businesses
OpenBSD on modern laptop
REF: http://bsdly.blogspot.tw/2017/07/openbsd-and-modern-laptop.html
Here are the two machines, the old (2014-vintage) and the new side by side:
The OpenBSD installer is a wonder of straightforward, no-nonsense simplicity that simply gets the job done. Even so, if you are not yet familiar with OpenBSD, it is worth spending some time reading the OpenBSD FAQ's installation guidelines and the INSTALL.$platformfile (in our case, INSTALL.amd64) to familiarize yourself with the procedure. If you're following this article to the letter and will be installing a snapshot, it is worth reading the notes on following -current too.
2017年8月14日 星期一
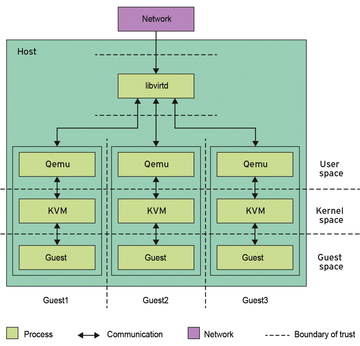
Avoiding KVM configuration errors
2017年8月13日 星期日
Sys Admins Will Love Red Hat Enterprise Linux 7.4
One of the main areas of focus this release is security. Those sys admins who are experimenting with containers can now take advantage of SELinux for their container workloads. In addition to SELinux support for OverlayFS, RHEL now has full support for the overlay2 storage driver.
What sys admin doesn’t love automation? RHEL 7.4 comes with the technology preview of RHEL System Roles, which brings together the capabilities of Red Hat Satellite and automation via Ansible Tower.
http://www.admin-magazine.com/News/Sys-Admins-Will-Love-Red-Hat-Enterprise-Linux-7.4
What sys admin doesn’t love automation? RHEL 7.4 comes with the technology preview of RHEL System Roles, which brings together the capabilities of Red Hat Satellite and automation via Ansible Tower.
http://www.admin-magazine.com/News/Sys-Admins-Will-Love-Red-Hat-Enterprise-Linux-7.4
Unprivileged container mapping
REF: https://pve.proxmox.com/wiki/Unprivileged_LXC_containers
Let's see an example, we want to make uid 1005 accessible in an unprivileged container.
First, we have to change the container UID mapping in the file
/etc/pve/lxc/1234.conf:
# uid map: from uid 0 map 1005 uids (in the ct) to the range starting 100000 (on the host), so 0..1004 (ct) → 100000..101004 (host) lxc.id_map = u 0 100000 1005 lxc.id_map = g 0 100000 1005 # we map 1 uid starting from uid 1005 onto 1005, so 1005 → 1005 lxc.id_map = u 1005 1005 1 lxc.id_map = g 1005 1005 1 # we map the rest of 65535 from 1006 upto 101006, so 1006..65535 → 101006..165535 lxc.id_map = u 1006 101006 64530 lxc.id_map = g 1006 101006 64530
Then we have to allow lxc to actually do the mapping on the host. Since lxc creates the CT using root, we have to allow root to use these uids in the container.
First the file
/etc/subuid (we allow 1 piece of uid starting from 1005):
root:1005:1
then
/etc/subgid:
root:1005:1
You can start or restart the container here, it should start and see
/shared mapped from the host directory /mnt/bindmounts/shared, all uids will be mapped to 65534:65534 except 1005, which would be seen (and written) as 1005:1005.2017年8月11日 星期五
Ransomware Now Steals From Bitcoin Wallets

Figure 1. Cerber arrival
The JavaScript attachment is dedicated as JS_NEMUCOD.SMGF2B, which leads to the download of the Cerber variant (detected as RANSOM_HPCERBER.SMALY5A). In most respects, this Cerber variant is identical to the versions we spotted in May, but with a new nuance to its behavior: it now targets Bitcoin wallets for theft as well.
REF: http://blog.trendmicro.com/trendlabs-security-intelligence/cerber-ransomware-evolves-now-steals-bitcoin-wallets/
2017年8月10日 星期四
AI already changing how CIOs lead healthcare IT
The healthcare industry is being rapidly transformed by technology in a multitude of ways – from how doctors engage with patients to how cures are discovered. Boston-based Partners HealthCare is getting ahead of these shifts by collaborating with GE Healthcare and Nvidia to strategically integrate artificial intelligence and machine learning technology into every aspect of patient care over the next 10 years.
REF: https://enterprisersproject.com/article/2017/8/ai-already-changing-how-cios-lead-healthcare-it
Querying ZFS Storage Pool Status
REF: https://docs.oracle.com/cd/E19253-01/819-5461/gaynp/index.html
The zpool list command provides several ways to request information regarding pool status. The information available generally falls into three categories: basic usage information, I/O statistics, and health status. All three types of storage pool information are covered in this section.
The zpool list command provides several ways to request information regarding pool status. The information available generally falls into three categories: basic usage information, I/O statistics, and health status. All three types of storage pool information are covered in this section.
2017年8月8日 星期二
Linux Tools on Windows 10
WSL allows you to run your choice of Linux distribution in Windows 10. Major distributions like openSUSE Leap are now available from the store and can be installed with one click.
REF: http://www.admin-magazine.com/News/Now-Everyone-Can-Run-Linux-Tools-on-Windows-10
REF: http://www.admin-magazine.com/News/Now-Everyone-Can-Run-Linux-Tools-on-Windows-10
2017年8月7日 星期一
Linux Container Security
LXC containers can be of two kinds:
- Privileged containers
- Unprivileged containers
The former can be thought as old-style containers, they're not safe at all and should only be used
in environments where unprivileged containers aren't available and where you would trust
your container's user with root access to the host.
in environments where unprivileged containers aren't available and where you would trust
your container's user with root access to the host.
The latter has been introduced back in LXC 1.0 (February 2014) and requires a reasonably recent
kernel (3.13 or higher). The upside being that we do consider those containers to be root-safe and so,
as long as you keep on top of kernel security issues, those containers are safe.
kernel (3.13 or higher). The upside being that we do consider those containers to be root-safe and so,
as long as you keep on top of kernel security issues, those containers are safe.
As privileged containers are considered unsafe, we typically will not consider new container escape
exploits to be security issues worthy of a CVE and quick fix. We will however try to mitigate those
issues so that accidental damage to the host is prevented.
REF: https://linuxcontainers.org/lxc/security/
exploits to be security issues worthy of a CVE and quick fix. We will however try to mitigate those
issues so that accidental damage to the host is prevented.
2017年8月6日 星期日
Check_MK: netstat
Established TCP Connections or TCP/UDP Listeners
| Distribution: | official part of Check_MK |
| License: | GPL |
| Supported Agents: | Linux, AIX |
This check evaluates the output of the netstat command on Linux and AIX and checks if there are established connections or listeners matching a given criteria.
The check returns OK state if the specified connection/listener is present, and CRIT if not.
This check needs the agent plugin netstat_an.bat to be installed.
REF: https://mathias-kettner.com/checkmk_check_netstat.html
2017年8月5日 星期六
Proxmox: limiting I/O
- Disk IO limits are fully implemented with KVM - you can even configure them on the GUI ('Disk throttle' buttom).
- For lxc: lsblk to get device:
└─sda3 8:3 0 3.7T 0 part
├─pve-root 251:0 0 10G 0 lvm /
├─pve-swap 251:1 0 2G 0 lvm [SWAP]
├─pve-data_tmeta 251:2 0 116M 0 lvm
│ └─pve-data-tpool 251:4 0 3.6T 0 lvm
│ ├─pve-data 251:5 0 3.6T 0 lvm
│ ├─pve-dir 251:6 0 50G 0 lvm
│ ├─pve-vm--60200--disk--1 251:7 0 600G 0 lvm
then
limit read to 10KB/s for container 60200
echo "251:7 10000" > /sys/fs/cgroup/blkio/lxc/60200/blkio.throttle.read_bps_device
for iops use blkio.throttle.read_iops_device
REF: https://forum.proxmox.com/threads/i-o-disk-limit.28591/
OpenBSD Console Freezes Proxmox 5.0
Proxmox5.0 running on AMD Opteron G2 2435 Based systems are NOT affected by the bug...So the Bug seems to only affect Intel systems (well) IvyBridge Xeon e5 2660-v2 or Xeon X5650 based systems
REF: https://www.mail-archive.com/misc@openbsd.org/msg154985.html
Small Log Monitoring Tools
A system's logfiles not only record failed login attempts by users, but they also log program errors and information about attacks. Admins therefore should keep a continuous eye on them. Tools such as LOGalyze [1], Logcheck [2], Logwatch [3], MultiTail [4], and SwatchDog [5] can help you here.
REF: http://www.linux-magazine.com/Issues/2017/200/Five-lean-tools-for-monitoring-logfiles
Microsoft SQL Server 2017 RC Comes with Full Support for Linux
REF: http://www.admin-magazine.com/News/Microsoft-SQL-Server-2017-RC-Comes-with-Full-Support-for-Linux
“SQL Server 2017 will bring with it support for the Linux OS and containers running on Windows, Linux, and macOS. Our goal is to enable SQL Server to run in modern IT infrastructure in any public or private cloud,” Tony Petrossian, Partner Group Program Manager, Database Systems Group at Microsoft, wrote in a blog post.
“SQL Server 2017 will bring with it support for the Linux OS and containers running on Windows, Linux, and macOS. Our goal is to enable SQL Server to run in modern IT infrastructure in any public or private cloud,” Tony Petrossian, Partner Group Program Manager, Database Systems Group at Microsoft, wrote in a blog post.
How Linux containers have evolved
REF: https://opensource.com/article/17/7/how-linux-containers-evolved?sc_cid=70160000000h0P5AAI

Containers have come a long way in the past few years. We walk through the timeline.

Image credits :
Downside of Free Software
REF: http://www.linux-magazine.com/Issues/2017/202/Downside-of-Free-Software
Some software, even the essential plumbing of the Internet on which we all depend, becomes an externality, and that makes it a problem.
What's an externality? It's a cost that you bear, or an advantage that you enjoy, that you haven't paid for. If a factory pollutes a river and the fishermen downstream find that their catch declines, that's an example of a negative externality affecting the fishermen.
Googler: Command-line search engine
It provides a headless search engine that can be called within a script. When combined with a text-based browser, it gives you access to the Internet. Most important of all, Googler offers the same search options and presentation of results as the Google home page, but with the use of a few aliases, in fewer keystrokes.
REF: http://www.linux-magazine.com/Issues/2017/202/Command-Line-Googler
How can better Digital Asset Management help charities
REF: http://www.resourcespace.com/feed?48

26TH JULY 2017

Canonical's next steps
REF: http://www.linux-magazine.com/Issues/2017/202/Interview-Canonical-s-Mark-Shuttleworth
Eventually, Shuttleworth and other Canonical leaders realized the company was trying to bite off more than it could chew, as it fought on simultaneous fronts with heavyweights such as Microsoft, Apple, Google, and Samsung. Canonical is now restructuring and is getting out of the consumer space to focus on the enterprise market.
Eventually, Shuttleworth and other Canonical leaders realized the company was trying to bite off more than it could chew, as it fought on simultaneous fronts with heavyweights such as Microsoft, Apple, Google, and Samsung. Canonical is now restructuring and is getting out of the consumer space to focus on the enterprise market.
訂閱:
意見 (Atom)