| ||
| ||
| ||
| ||
---------- Forwarded message ---------
From: Marc Deslauriers <marc.deslauriers@canonical.com>
Date: Aug 25, 2020 9:05PM
Noah Misch discovered that PostgreSQL incorrectly handled the search_path
setting when used with logical replication. A remote attacker could
possibly use this issue to execute arbitrary SQL code. This issue only
affected Ubuntu 18.04 LTS and Ubuntu 20.04 LTS. (CVE-2020-14349)
Andres Freund discovered that PostgreSQL incorrectly handled search path
elements in CREATE EXTENSION. A remote attacker could possibly use this
issue to execute arbitrary SQL code. (CVE-2020-14350)
References:
https://usn.ubuntu.com/4472-1
CVE-2020-14349, CVE-2020-14350
Watch the RNC free on The Roku Channel
See all of the speeches, analysis, and reactions surrounding the historic 2020 Republican convention, the party’s first virtual convention. Nightly through Thursday. Coverage starts at 7pm ET | 4pm PT
---------- Forwarded message ---------
From: Marc Deslauriers <marc.deslauriers@canonical.com>
Date: Aug 21, 2020 9:58PM
Emanuel Almeida discovered that Bind incorrectly handled certain TCP
payloads. A remote attacker could possibly use this issue to cause Bind to
crash, resulting in a denial of service. This issue only affected Ubuntu
20.04 LTS. (CVE-2020-8620)
Joseph Gullo discovered that Bind incorrectly handled QNAME minimization
when used in certain configurations. A remote attacker could possibly use
this issue to cause Bind to crash, resulting in a denial of service. This
issue only affected Ubuntu 20.04 LTS. (CVE-2020-8621)
Dave Feldman, Jeff Warren, and Joel Cunningham discovered that Bind
incorrectly handled certain truncated responses to a TSIG-signed request. A
remote attacker could possibly use this issue to cause Bind to crash,
resulting in a denial of service. (CVE-2020-8622)
Lyu Chiy discovered that Bind incorrectly handled certain queries. A remote
attacker could possibly use this issue to cause Bind to crash, resulting in
a denial of service. (CVE-2020-8623)
Joop Boonen discovered that Bind incorrectly handled certain subdomain
update-policy rules. A remote attacker granted privileges to change certain
parts of a zone could use this issue to change other contents of the zone,
contrary to expectations. This issue only affected Ubuntu 18.04 LTS and
Ubuntu 20.04 LTS. (CVE-2020-8624)
References:
https://usn.ubuntu.com/4468-1
CVE-2020-8620, CVE-2020-8621, CVE-2020-8622, CVE-2020-8623,
CVE-2020-8624
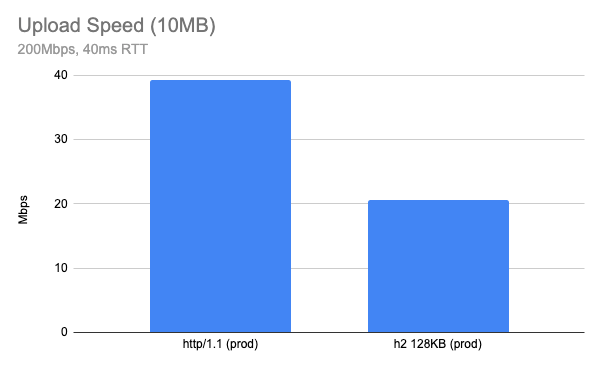
REF: https://blog.cloudflare.com/delivering-http-2-upload-speed-improvements/
---------- Forwarded message ---------
From: Marc Deslauriers <marc.deslauriers@canonical.com>
Date: Aug 19, 2020 9:06PM
Marc Aldorasi discovered that curl incorrectly handled the libcurl
CURLOPT_CONNECT_ONLY option. This could result in data being sent to the
wrong destination, possibly exposing sensitive information.
References:
https://usn.ubuntu.com/4466-1
CVE-2020-8231
Smooth streaming for any room
Powerful and portable, Roku® Streaming Stick®+ is super-charged with a long-range wireless receiver for up to 4x the range. Save $10 today and enjoy free shipping.
---------- Forwarded message ---------
From: Steve Beattie <steve.beattie@canonical.com>
Date: Aug 18, 2020 1:39PM
It was discovered that the bcache subsystem in the Linux kernel did not
properly release a lock in some error conditions. A local attacker could
possibly use this to cause a denial of service.
References:
https://usn.ubuntu.com/4462-1
CVE-2020-12771

The first major compatibility improvement is that LibreOffice includes support for ODF 1.3. Along with this update comes digital signatures for documents and OpenPGP-based encryption of XML documents.
MS Office compatibility has been greatly improved with LibreOffice’s handling of DOCX, XLSX, and PPTX files. With this new release, DOCX files now save in native 2013/2016/2019 mode (instead of the outdated 2007 compatibility mode). Along those same lines, XLSX sheet names longer than 31 characters are now supported, as well as the exporting of checkboxes in XLSX.
Tool-specific improvements include semi-transparent text support and better handling of quotes and apostrophes in Writer; new functions for non-volatile random number generation, keyboard shortcuts for autosum in Calc; semi-transparent text, subscripts return to default 8%, and PDFs larger than 500 cm can be generated in Draw.
New features across the suite include:
REF: https://www.linux-magazine.com/Online/News/LibreOffice-7-Now-Available
---------- Forwarded message ---------
From: Checkmk Announcements <checkmk-announce@lists.mathias-kettner.de>
Date: Fri, Aug 21, 2020 at 3:54 AM
Dear friends of Checkmk,
the new stable release 1.6.0p16 of Checkmk is ready for download.
This maintenance release ships with 11 changes affecing all editions of Checkmk,
0 Enterprise Edition specific changes and 0 Managed Services Edition specific changes.
Changes in all Checkmk Editions:
Checks & agents:
* 11234 Check_MK service: State if "Unexpected allowed IP ranges" is configurable
* 11302 FIX: Azure Storage: egress data levels wrongly labelled on user interface
* 11239 FIX: Check_MK Discovery: Revert werks 10534, 11229 and 11238
* 11238 FIX: Check_MK Discovery: Was unable to discover new SNMP check types
* 11144 FIX: Display graph for SAP HANA License
* 11303 FIX: mem.linux: false CRIT status when VmallocChunk is set to 0 kB
Core & setup:
* 11263 SEC: Fix piggyback path traversal
NOTE: Please refer to the migration notes!
Event console:
* 11261 FIX: Fix performance regression caused by too many live status queries between EC and core
Notifications:
* 11051 FIX: crash in notifications if "Exclude Service Groups (regex)" is used
Site management:
* 11341 FIX: Make omd restore work with hardlinks in local dir
User interface:
* 10544 FIX: Quicksearch: Fixed incorrect result page when querying host tags
You can download Checkmk from our download page:
* https://checkmk.com/download.php
Figure 1. A visualization of how HTTP/1.0 differs from HTTP/2 when it comes to requests and replies
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/unsecure-grpc-implementations-compromise-apis-applications/
---------- Forwarded message ---------
From: Marc Deslauriers <marc.deslauriers@canonical.com>
Date: Aug 20, 2020 1:14AM
Ziming Zhang and VictorV discovered that the QEMU SLiRP networking
implementation incorrectly handled replying to certain ICMP echo requests.
An attacker inside a guest could possibly use this issue to leak host
memory to obtain sensitive information. This issue only affected Ubuntu
18.04 LTS. (CVE-2020-10756)
Eric Blake and Xueqiang Wei discovered that the QEMU NDB implementation
incorrectly handled certain requests. A remote attacker could possibly use
this issue to cause QEMU to crash, resulting in a denial of service. This
issue only affected Ubuntu 20.04 LTS. (CVE-2020-10761)
Ziming Zhang discovered that the QEMU SM501 graphics driver incorrectly
handled certain operations. An attacker inside a guest could use this issue
to cause QEMU to crash, resulting in a denial of service, or possibly
execute arbitrary code. (CVE-2020-12829)
It was discovered that the QEMU SD memory card implementation incorrectly
handled certain memory operations. An attacker inside a guest could
possibly use this issue to cause QEMU to crash, resulting in a denial of
service. (CVE-2020-13253)
Ren Ding and Hanqing Zhao discovered that the QEMU ES1370 audio driver
incorrectly handled certain invalid frame counts. An attacker inside a
guest could possibly use this issue to cause QEMU to crash, resulting in a
denial of service. (CVE-2020-13361)
Ren Ding and Hanqing Zhao discovered that the QEMU MegaRAID SAS SCSI driver
incorrectly handled certain memory operations. An attacker inside a guest
could possibly use this issue to cause QEMU to crash, resulting in a denial
of service. (CVE-2020-13362)
Alexander Bulekov discovered that QEMU MegaRAID SAS SCSI driver incorrectly
handled certain memory space operations. An attacker inside a guest could
possibly use this issue to cause QEMU to crash, resulting in a denial of
service. (CVE-2020-13659)
Ren Ding, Hanqing Zhao, Alexander Bulekov, and Anatoly Trosinenko
discovered that the QEMU incorrectly handled certain msi-x mmio operations.
An attacker inside a guest could possibly use this issue to cause QEMU to
crash, resulting in a denial of service. (CVE-2020-13754)
It was discovered that QEMU incorrectly handled certain memory copy
operations when loading ROM contents. If a user were tricked into running
an untrusted kernel image, a remote attacker could possibly use this issue
to run arbitrary code. This issue only affected Ubuntu 16.04 LTS and Ubuntu
18.04 LTS. (CVE-2020-13765)
Ren Ding, Hanqing Zhao, and Yi Ren discovered that the QEMU ATI video
driver incorrectly handled certain index values. An attacker inside a guest
could possibly use this issue to cause QEMU to crash, resulting in a denial
of service. This issue only affected Ubuntu 20.04 LTS. (CVE-2020-13800)
Ziming Zhang discovered that the QEMU OSS audio driver incorrectly handled
certain operations. An attacker inside a guest could possibly use this
issue to cause QEMU to crash, resulting in a denial of service. This issue
only affected Ubuntu 20.04 LTS. (CVE-2020-14415)
Ziming Zhang discovered that the QEMU XGMAC Ethernet controller incorrectly
handled packet transmission. An attacker inside a guest could use this
issue to cause QEMU to crash, resulting in a denial of service, or possibly
execute arbitrary code. (CVE-2020-15863)
Ziming Zhang discovered that the QEMU e1000e Ethernet controller
incorrectly handled packet processing. An attacker inside a guest could
possibly use this issue to cause QEMU to crash, resulting in a denial of
service. This issue only affected Ubuntu 18.04 LTS and Ubuntu 20.04 LTS.
(CVE-2020-16092)
References:
https://usn.ubuntu.com/4467-1
CVE-2020-10756, CVE-2020-10761, CVE-2020-12829, CVE-2020-13253,
CVE-2020-13361, CVE-2020-13362, CVE-2020-13659, CVE-2020-13754,
CVE-2020-13765, CVE-2020-13800, CVE-2020-14415, CVE-2020-15863,
CVE-2020-16092
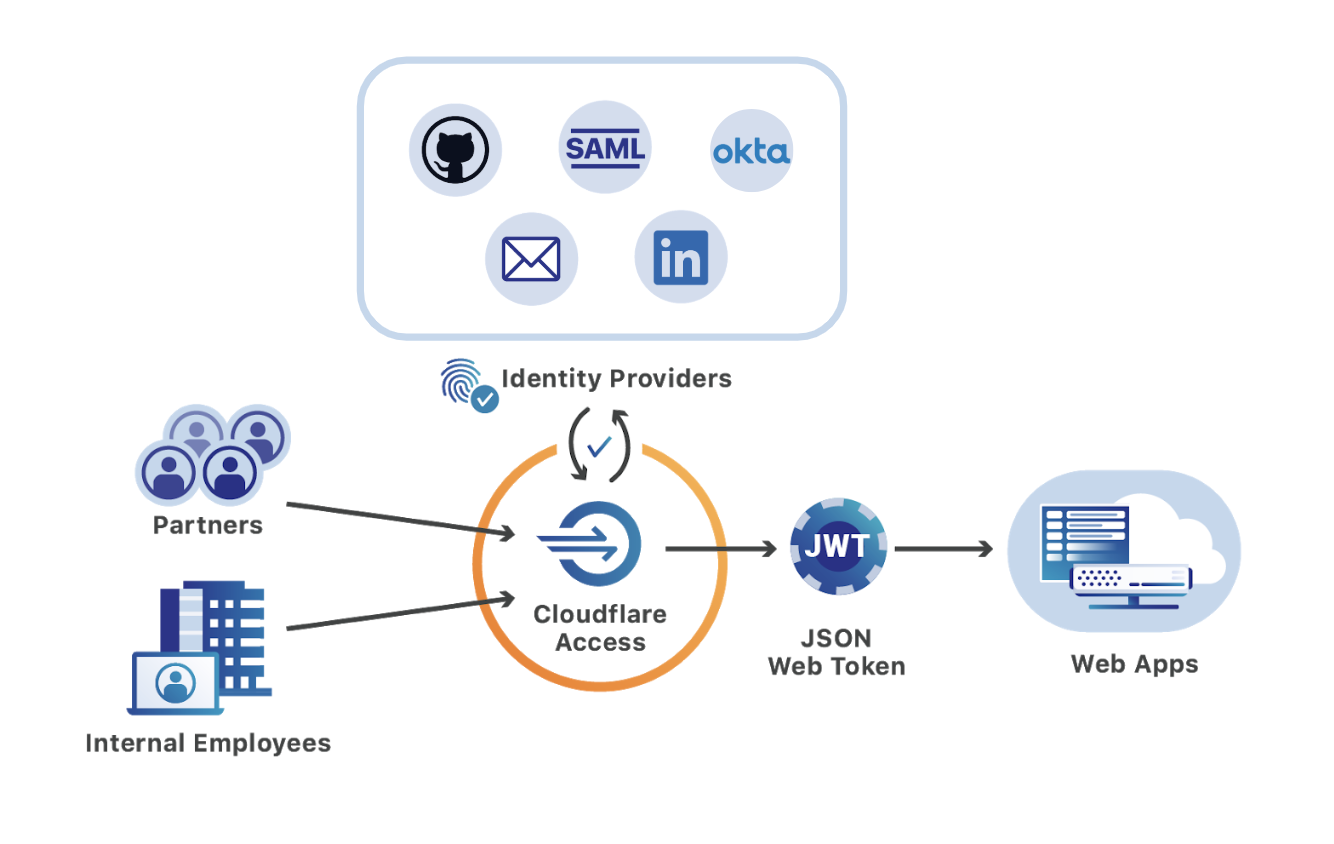
REF: https://blog.cloudflare.com/require-hard-key-auth-with-cloudflare-access/
---------- Forwarded message ---------
From: Brent Cook <busterb@gmail.com>
Date: Tue, Aug 18, 2020 at 1:55 AM
We have released LibreSSL 3.1.4, which will be arriving in the LibreSSL directory of your local OpenBSD mirror soon. It includes interoperability and bug fixes for the TLSv1.3 client.
The LibreSSL project continues improvement of the codebase to reflect modern, safe programming practices. We welcome feedback and improvements from the broader community. Thanks to all of the contributors who helped make this release possible.
| Puppet Enterprise 2019.8 LTS |
| This release gives teams access to more powerful orchestration capabilities with shared content from the Puppet Forge, out-of-the-box workflows for patch management, and greater flexibility to manage infrastructure using both imperative (work-flow based) and declarative (model-based) automation types. |
---------- Forwarded message ---------
From: Marc Deslauriers <marc.deslauriers@canonical.com>
Date: Jul 28, 2020 11:39PM
Multiple security issues were discovered in MySQL and this update includes
new upstream MySQL versions to fix these issues.
MySQL has been updated to 8.0.21 in Ubuntu 20.04 LTS. Ubuntu 16.04 LTS and
Ubuntu 18.04 LTS have been updated to MySQL 5.7.31.
In addition to security fixes, the updated packages contain bug fixes, new
features, and possibly incompatible changes.
References:
https://usn.ubuntu.com/4441-1
CVE-2020-14539, CVE-2020-14540, CVE-2020-14547, CVE-2020-14550,
CVE-2020-14553, CVE-2020-14559, CVE-2020-14568, CVE-2020-14575,
CVE-2020-14576, CVE-2020-14586, CVE-2020-14591, CVE-2020-14597,
CVE-2020-14619, CVE-2020-14620, CVE-2020-14623, CVE-2020-14624,
CVE-2020-14631, CVE-2020-14632, CVE-2020-14633, CVE-2020-14634,
CVE-2020-14641, CVE-2020-14643, CVE-2020-14651, CVE-2020-14654,
CVE-2020-14656, CVE-2020-14663, CVE-2020-14678, CVE-2020-14680,
CVE-2020-14697, CVE-2020-14702
---------- Forwarded message ---------
From: Chris Coulson <chris.coulson@canonical.com>
Date: Jul 30, 2020 3:36AM
Multiple security issues were discovered in Firefox. If a user were
tricked in to opening a specially crafted website, an attacker could
potentially exploit these to cause a denial of service, obtain sensitive
information, bypass iframe sandbox restrictions, confuse the user, or
execute arbitrary code. (CVE-2020-6463, CVE-2020-6514, CVE-2020-15652,
CVE-2020-15653, CVE-2020-15654, CVE-2020-15656, CVE-2020-15658,
CVE-2020-15659)
It was discovered that redirected HTTP requests which are observed or
modified through a web extension could bypass existing CORS checks. If a
user were tricked in to installing a specially crafted extension, an
attacker could potentially exploit this to obtain sensitive information
across origins. (CVE-2020-15655)
References:
https://usn.ubuntu.com/4443-1
CVE-2020-15652, CVE-2020-15653, CVE-2020-15654, CVE-2020-15655,
CVE-2020-15656, CVE-2020-15658, CVE-2020-15659, CVE-2020-6463,
CVE-2020-6514
 |
| Since launching a couple months ago we’ve continued work on our Watch Together feature and now you can invite someone to or join a session while it’s in progress, without interrupting the playback. So, if you’re running late to the movie, no worries—the show can and will go on when you are ready. |
The UXSS attack is theoretically capable of modifying almost every part of the user’s browser experience as arbitrary JavaScript-injected code. These modifications include:
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/xcsset-mac-malware-infects-xcode-projects-performs-uxss-attack-on-safari-other-browsers-leverages-zero-day-exploits/
---------- Forwarded message ---------
From: Marc Deslauriers <marc.deslauriers@canonical.com>
Date: Aug 5, 2020 2:48AM
Trent Shea discovered that the libvirt package set incorrect permissions on
the UNIX domain socket. A local attacker could use this issue to access
libvirt and escalate privileges.
References:
https://usn.ubuntu.com/4452-1
CVE-2020-15708
 |
| We are excited to unveil a preview of our new Smart TV app, now the default experience for LG smart TVs running webOS 3+. This new app has been built from the ground up with the Lightning framework, bringing support for features like the Live TV guide and Skip Intro AND bringing you a faster, smoother experience than the old version of the app. In addition, Samsung, Vizio and Xbox One users can opt in for now. |
---------- Forwarded message ---------
From: Leonidas S. Barbosa <leo.barbosa@canonical.com>
Date: Aug 6, 2020 11:48PM
Thomas Chauchefoin discovered that ppp incorrectly handled module loading.
A local attacker could use this issue to load arbitrary kernel modules and
possibly execute arbitrary code.
References:
https://usn.ubuntu.com/4451-2
https://usn.ubuntu.com/4451-1
CVE-2020-15704
Figure 1. Water Nue attack scenario
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/water-nue-campaign-targets-c-suites-office-365-accounts/
---------- Forwarded message ---------
From: Samuli Seppänen <samuli@openvpn.net>
Date: Sat, Aug 15, 2020 at 3:39 AM
The OpenVPN community project team is proud to release OpenVPN
2.5-beta1. Source code and Windows installers can be downloaded from https://openvpn.net/community-downloads/
More details on these new features as well as a list of deprecated
features and user-visible changes are available in Changes.rst: https://github.com/OpenVPN/openvpn/blob/release/2.5/Changes.rst
For generic help use these support channels:
 |
|
---------- Forwarded message ---------
From: Marc Deslauriers <marc.deslauriers@canonical.com>
Date: Aug 13, 2020 11:20PM
Fabrice Perez discovered that the Apache mod_rewrite module incorrectly
handled certain redirects. A remote attacker could possibly use this issue
to perform redirects to an unexpected URL. (CVE-2020-1927)
Chamal De Silva discovered that the Apache mod_proxy_ftp module incorrectly
handled memory when proxying to a malicious FTP server. A remote attacker
could possibly use this issue to obtain sensitive information.
(CVE-2020-1934)
Felix Wilhelm discovered that the HTTP/2 implementation in Apache did not
properly handle certain Cache-Digest headers. A remote attacker could
possibly use this issue to cause Apache to crash, resulting in a denial of
service. This issue only affected Ubuntu 18.04 LTS and Ubuntu 20.04 LTS.
(CVE-2020-9490)
Felix Wilhelm discovered that the Apache mod_proxy_uwsgi module incorrectly
handled large headers. A remote attacker could use this issue to obtain
sensitive information or possibly execute arbitrary code. This issue only
affected Ubuntu 20.04 LTS. (CVE-2020-11984)
Felix Wilhelm discovered that the HTTP/2 implementation in Apache did not
properly handle certain logging statements. A remote attacker could
possibly use this issue to cause Apache to crash, resulting in a denial of
service. This issue only affected Ubuntu 18.04 LTS and Ubuntu 20.04 LTS.
(CVE-2020-11993)
References:
https://usn.ubuntu.com/4458-1
CVE-2020-11984, CVE-2020-11993, CVE-2020-1927, CVE-2020-1934,
CVE-2020-9490
---------- Forwarded message ---------
From: Marc Deslauriers <marc.deslauriers@canonical.com>
Date: Aug 10, 2020 11:01PM
Martin von Wittich and Wilko Meyer discovered that Samba incorrectly
handled certain empty UDP packets when being used as a AD DC NBT server. A
remote attacker could possibly use this issue to cause Samba to crash,
resulting in a denial of service.
References:
https://usn.ubuntu.com/4454-1
CVE-2020-14303
 |
| Have you watched free Live TV on Plex? With 80+ channels and counting, there’s something for everyone. Whether you want some help entertaining the kids so you can get some work done or just want to learn about the history of beer, our lineup is available to you instantly, 24/7. |
---------- Forwarded message ---------
From: Eduardo Barretto <eduardo.barretto@canonical.com>
Date: Aug 6, 2020 2:36AM
Johannes Kuhn discovered that OpenJDK 8 incorrectly handled access control
contexts. An attacker could possibly use this issue to execute arbitrary
code. (CVE-2020-14556)
Philippe Arteau discovered that OpenJDK 8 incorrectly verified names in
TLS server's X.509 certificates. An attacker could possibly use this
issue to obtain sensitive information. (CVE-2020-14577)
It was discovered that OpenJDK 8 incorrectly handled exceptions in
DerInputStream class and in the DerValue.equals() method. An attacker
could possibly use this issue to cause a denial of service.
(CVE-2020-14578, CVE-2020-14579)
It was discovered that OpenJDK 8 incorrectly handled image files. An
attacker could possibly use this issue to obtain sensitive information.
(CVE-2020-14581)
Markus Loewe discovered that OpenJDK 8 incorrectly handled concurrent
access in java.nio.Buffer class. An attacker could use this issue to
bypass sandbox restrictions.
(CVE-2020-14583)
It was discovered that OpenJDK 8 incorrectly handled transformation of
images. An attacker could possibly use this issue to bypass sandbox
restrictions and insert, edit or obtain sensitive information.
(CVE-2020-14593)
Roman Shemyakin discovered that OpenJDK 8 incorrectly handled XML files.
An attacker could possibly use this issue to insert, edit or obtain
sensitive information. (CVE-2020-14621)
References:
https://usn.ubuntu.com/4453-1
CVE-2020-14556, CVE-2020-14577, CVE-2020-14578, CVE-2020-14579,
CVE-2020-14581, CVE-2020-14583, CVE-2020-14593, CVE-2020-14621
Figure 1. Credit card skimming attack chain
---------- Forwarded message ---------
From: Michael Mraka <michael.mraka@redhat.com>
Date: Thu, Jul 23, 2020 at 11:44 PM
To: <spacewalk-announce-list@redhat.com>, <spacewalk-list@redhat.com>
Dear Spacewalkers,
You may have noticed that the number of Red Hat contributions decreased in the
last couple of months. This is aligned with our plan and communication. Now we
reached a state when no further contributions are planned from the Red Hat
side.
Let me clarify what it means for the community:
- Spacewalk 2.10 is the very last release
- Spacewalk github repositories have been archived (are read-only now)
- Red Hat won't commit any new code, provide any bug fixes (not even critical
security ones), enhancement or accept any pull requests (it isn't possible to
submit a PR to an archived repository)
- The spacewalk-announce-list@redhat.com and spacewalk-devel@redhat.com mailing
lists will be archived
- Spacewalk contributors from Red Hat left #spacewalk-devel IRC channel on freenode
- All remaining Spacewalk bugreports have been closed and it is not possible to
create new ones
- There's no one to track future security exposures, CVEs
- Due to the lack of further updates we strongly recommend not to expose
running servers on a public network and keeping them within your private
network
What will still be available:
- spacewalkproject.org pages (as they are, with no further changes)
- COPR repositories with Spacewalk packages, so it's possible:
- to install new and upgrade existing Spacewalk servers (but with no further updates)
- to fork them to make your own customizations
- #spacewalk IRC channel on freenode and
- spacewalk-list@redhat.com mailing list for the community to discuss Spacewalk
related questions or issues
- read-only github repositories - anyone can clone and use them according to
the General Public License (GPLv2) license
If you choose to, you may still run your existing or install new servers, use
already synced content, create or sync new one, manage existing or register new
clients. We know there will still be plenty of users that will keep operating
Spacewalk for some time.
Up to the current date, we're aware of only one public Spacewalk fork - Uyuni
project. We're encouraging everyone who'd like to stay with the codebase and
active community to check out this project.
We'd also like to take this opportunity and thank all developers and
contributors who helped us to create this project, to our long time users, to
people opening bug reports, debugging and fixing issues and to Red Hat to
sponsoring the project for all these years. It's been a pleasure and fun
working on Spacewalk, we've enjoyed it. Thank you!
See you in communities of other management projects!
Spacewalk team
--
Michael Mráka
Smart Management Engineering, Red Hat
_______________________________________________
Spacewalk-announce-list mailing list
Spacewalk-announce-list@redhat.com
https://www.redhat.com/mailman/listinfo/spacewalk-announce-list
Your weekend pick is free on The Roku Channel
This award-winning animated hit is fun for everyone in the home. Featuring the voices of Jay Baruchel, Gerard Butler, America Ferrera, Jonah Hill, and Kristen Wiig, this comic adventure tracks the son of a Viking chief on his quest to capture a dragon and prove his worthiness.
|
|
Figure 1. Code snippet showing XORDDoS creating multiple copies of itself
16 must-stream TV premieres in August
Keep your summer streaming fresh with new TV premieres this month, including the Netflix reality hit Selling Sunset, Jason Sudeikis in the world premiere of Ted Lasso, and the return of Shark Week.
---------- Forwarded message ---------
From: Donald Norwood <donald@debian.org>
Date: Aug 1, 2020 11:34PM
The Debian project is pleased to announce the fifth update of its stable
distribution Debian 10 (codename "buster"). This point release mainly
adds corrections for security issues, along with a few adjustments for
serious problems. Security advisories have already been published
separately and are referenced where available.
This point release also addresses Debian Security Advisory: DSA-4735-1
grub2 -- security update [1] which covers multiple CVE issues regarding
the GRUB2 UEFI SecureBoot 'BootHole' vulnerability [2].
1: https://www.debian.org/security/2020/dsa-4735
2: https://www.debian.org/security/2020-GRUB-UEFI-SecureBoot/
Please note that the point release does not constitute a new version of
Debian 10 but only updates some of the packages included. There is no
need to throw away old "buster" media. After installation, packages can
be upgraded to the current versions using an up-to-date Debian mirror.
Those who frequently install updates from security.debian.org won't have
to update many packages, and most such updates are included in the point
release.
New installation images will be available soon at the regular locations.
Upgrading an existing installation to this revision can be achieved by
pointing the package management system at one of Debian's many HTTP
mirrors. A comprehensive list of mirrors is available at:
https://www.debian.org/mirror/list
Whether you're a sports fanatic or just miss cheering for the home team, here's our guide on how to stream the MLB, NBA, and MLS action without cable.