Figure 1. TA505’s latest infection chain
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/shifting-tactics-breaking-down-ta505-groups-use-of-html-rats-and-other-techniques-in-latest-campaigns/
2019年6月30日 星期日
[USN-4018-1] Samba vulnerabilities
---------- Forwarded message ---------
From: Marc Deslauriers
Date: Jun 19, 2019 8:52PM
It was discovered that Samba incorrectly handled certain RPC messages. A
remote attacker could possibly use this issue to cause Samba to crash,
resulting in a denial of service. (CVE-2019-12435)
It was discovered that Samba incorrectly handled LDAP pages searches. A
remote attacker could possibly use this issue to cause Samba to crash,
resulting in a denial of service. (CVE-2019-12436)
References:
https://usn.ubuntu.com/4018-1
CVE-2019-12435, CVE-2019-12436
From: Marc Deslauriers
Date: Jun 19, 2019 8:52PM
It was discovered that Samba incorrectly handled certain RPC messages. A
remote attacker could possibly use this issue to cause Samba to crash,
resulting in a denial of service. (CVE-2019-12435)
It was discovered that Samba incorrectly handled LDAP pages searches. A
remote attacker could possibly use this issue to cause Samba to crash,
resulting in a denial of service. (CVE-2019-12436)
References:
https://usn.ubuntu.com/4018-1
CVE-2019-12435, CVE-2019-12436
2019年6月28日 星期五
Your Plex wants to talk to you
Ever since its inception, your Plex Media Server has been sitting there mute, dying to share its life story with you. Finally, its wish has been granted! Notifications from PMS are now available on iOS and Android as a Plex Pass Preview—just opt-in to set them up.
TrendLabs: Advanced Targeted Attack Tools Found Being Used to Distribute Cryptocurrency Miners
Figure 1. The files located inside the zip archive
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/advanced-targeted-attack-tools-used-to-distribute-cryptocurrency-miners/
2019年6月26日 星期三
[USN-4027-1] PostgreSQL vulnerability
---------- Forwarded message ---------
From: Marc Deslauriers
Date: Jun 21, 2019 12:05AM
PostgreSQL could be made to crash or run programs if it received specially
crafted network traffic.
Software Description:
- postgresql-11: Object-relational SQL database
- postgresql-10: Object-relational SQL database
Details:
Alexander Lakhin discovered that PostgreSQL incorrectly handled
authentication. An authenticated attacker or a rogue server could use this
issue to cause PostgreSQL to crash, resulting in a denial of service, or
possibly execute arbitrary code. The default compiler options for affected
releases should reduce the vulnerability to a denial of service.
References:
https://usn.ubuntu.com/4027-1
CVE-2019-10164
From: Marc Deslauriers
Date: Jun 21, 2019 12:05AM
PostgreSQL could be made to crash or run programs if it received specially
crafted network traffic.
Software Description:
- postgresql-11: Object-relational SQL database
- postgresql-10: Object-relational SQL database
Details:
Alexander Lakhin discovered that PostgreSQL incorrectly handled
authentication. An authenticated attacker or a rogue server could use this
issue to cause PostgreSQL to crash, resulting in a denial of service, or
possibly execute arbitrary code. The default compiler options for affected
releases should reduce the vulnerability to a denial of service.
References:
https://usn.ubuntu.com/4027-1
CVE-2019-10164
2019年6月25日 星期二
2019年6月24日 星期一
[LSN-0052-1] Linux kernel vulnerability (SACKs)
---------- Forwarded message ---------
From:
Date: Jun 19, 2019 6:33AM
Jonathan Looney discovered that an integer overflow existed in the Linux
kernel when handling TCP Selective Acknowledgments (SACKs). A remote
attacker could use this to cause a denial of service (system crash).
(CVE-2019-11477)
Jonathan Looney discovered that the TCP retransmission queue implementation
in the Linux kernel could be fragmented when handling certain TCP Selective
Acknowledgment (SACK) sequences. A remote attacker could use this to cause
a denial of service. (CVE-2019-11478)
References:
CVE-2019-11477, CVE-2019-11478
From:
Date: Jun 19, 2019 6:33AM
Jonathan Looney discovered that an integer overflow existed in the Linux
kernel when handling TCP Selective Acknowledgments (SACKs). A remote
attacker could use this to cause a denial of service (system crash).
(CVE-2019-11477)
Jonathan Looney discovered that the TCP retransmission queue implementation
in the Linux kernel could be fragmented when handling certain TCP Selective
Acknowledgment (SACK) sequences. A remote attacker could use this to cause
a denial of service. (CVE-2019-11478)
References:
CVE-2019-11477, CVE-2019-11478
TrendLabs: AESDDoS Botnet Malware Infiltrates Containers via Exposed Docker APIs
Figure 1. HFS panel with listing of hosted malware and tools
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/aesddos-botnet-malware-infiltrates-containers-via-exposed-docker-apis/
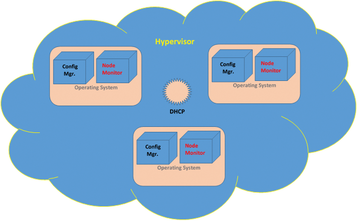
ADMIN: A self-healing VM system
TrendLabs: Mobile Cyberespionage Campaign ‘Bouncing Golf’ Affects Middle East
ADMIN: Scanning servers with Nikto
The Nikto scanner performs multiple comprehensive tests against web servers.
An abundance of security tools tout their wares on the Internet these days, making it difficult to sift the wheat from the chaff. Many such tools are proprietary, some are unquestionably good value for the money, and some tools are overpriced but marketed well. When surrounded by all these options, however, remember that a sizeable number of highly sophisticated open source tools are available as well.
REF: http://www.admin-magazine.com/Archive/2019/51/Scanning-servers-with-Nikto
An abundance of security tools tout their wares on the Internet these days, making it difficult to sift the wheat from the chaff. Many such tools are proprietary, some are unquestionably good value for the money, and some tools are overpriced but marketed well. When surrounded by all these options, however, remember that a sizeable number of highly sophisticated open source tools are available as well.
REF: http://www.admin-magazine.com/Archive/2019/51/Scanning-servers-with-Nikto
TrendLabs: Cryptocurrency-Mining Botnet Malware Arrives Through ADB and Spreads Through SSH
[Checkmk Announce] New Checkmk stable release 1.5.0p18
---------- Forwarded message ---------
From: Checkmk Announcements
Date: Fri, Jun 14, 2019 at 3:49 PM
This maintenance release ships with 13 changes affecing all editions of Checkmk,
1 Enterprise Edition specific changes and 0 Managed Services Edition specific changes.
User interface:
* 7260 FIX: Virtual Host Tree: Fixed sorting by topic
Checks & agents:
* 7793 FIX: watchdog_sensors: Do not proceed parsing sensor data if no version information is available
* 7790 FIX: statgrab_cpu: Fixed parsing CPU values; Some values may be missing
* 7789 FIX: rds_licenses: Skip check plugin if no data available
* 7786 FIX: printer_pages: Fixed parsing total amount of pages if not available
* 7794 FIX: oracle_sessions: Fixed parsing invalid lines containg 'FAILURE' instead of amount of current sessions
* 7785 FIX: oracle_crs_res: Fixed parsing old agent output where node name as first column is missing
* 7792 FIX: mssql_instance: Fixed parsing invalid lines containing DB connection errors
* 7791 FIX: msexch_autodiscovery: Fixed WMI time handling if frequency is empty which caused a ValueError
* 7787 FIX: informix_status: Display server version or port if available - avoid crash if not
* 7784 FIX: hp_proliant_da_phydrv: Fixed missing smart status translation and made states readable
* 7788 FIX: emcvnx_mirrorview: Skip invalid data: 'Error occurred during HTTP request/response from the target'
* 7783 FIX: db2_bp_hitratios: Fixed parsing instances in DPF mode: 'KeyError: None'; only gather real instances
You can download Checkmk from our download page:
* https://checkmk.com/download.php
Please mail bug reports and qualified feedback to feedback@check-mk.org.
We greatly thank you for using Checkmk and wish you a successful monitoring,
From: Checkmk Announcements
Date: Fri, Jun 14, 2019 at 3:49 PM
This maintenance release ships with 13 changes affecing all editions of Checkmk,
1 Enterprise Edition specific changes and 0 Managed Services Edition specific changes.
User interface:
* 7260 FIX: Virtual Host Tree: Fixed sorting by topic
Checks & agents:
* 7793 FIX: watchdog_sensors: Do not proceed parsing sensor data if no version information is available
* 7790 FIX: statgrab_cpu: Fixed parsing CPU values; Some values may be missing
* 7789 FIX: rds_licenses: Skip check plugin if no data available
* 7786 FIX: printer_pages: Fixed parsing total amount of pages if not available
* 7794 FIX: oracle_sessions: Fixed parsing invalid lines containg 'FAILURE' instead of amount of current sessions
* 7785 FIX: oracle_crs_res: Fixed parsing old agent output where node name as first column is missing
* 7792 FIX: mssql_instance: Fixed parsing invalid lines containing DB connection errors
* 7791 FIX: msexch_autodiscovery: Fixed WMI time handling if frequency is empty which caused a ValueError
* 7787 FIX: informix_status: Display server version or port if available - avoid crash if not
* 7784 FIX: hp_proliant_da_phydrv: Fixed missing smart status translation and made states readable
* 7788 FIX: emcvnx_mirrorview: Skip invalid data: 'Error occurred during HTTP request/response from the target'
* 7783 FIX: db2_bp_hitratios: Fixed parsing instances in DPF mode: 'KeyError: None'; only gather real instances
You can download Checkmk from our download page:
* https://checkmk.com/download.php
Please mail bug reports and qualified feedback to feedback@check-mk.org.
We greatly thank you for using Checkmk and wish you a successful monitoring,
TrendLabs: CVE-2019-8635: Double Free Vulnerability in Apple macOS Lets Attackers Escalate System Privileges and Execute Arbitrary Code
Figure 2. The pseudo code snippet of IOAccelContext2::processSidebandBuffer
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/cve-2019-8635-double-free-vulnerability-in-apple-macos-lets-attackers-escalate-system-privileges-and-execute-arbitrary-code/
2018 Market Guide for AIOps Platforms
Gartner describes how AIOps has expanded, lays out the key steps for IT departments looking to gain the benefits of AIOps and provides crucial information for selecting tools and vendors.
- The difference betweens AIOps features and AIOps platforms
- The most important data categories for AIOps
- Gartner’s recommendations for how to get started in AIOps
TrendLabs: MuddyWater Resurfaces, Uses Multi-Stage Backdoor POWERSTATS V3 and New Post-Exploitation Tools
Figure 2. Email headers showing the origin of the spear-phishing email
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/muddywater-resurfaces-uses-multi-stage-backdoor-powerstats-v3-and-new-post-exploitation-tools/
Roku's Special Father’s Day offers
Knock Dad’s socks off with the stunning picture quality of 4K Roku TV™, and Roku® Streaming Stick®+ gives Dad 4K picture quality with 4x the wireless range and a voice remote.ott
訂閱:
意見 (Atom)