Figure 1. Screen capture that shows that user namespaces are not used by default
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/why-running-a-privileged-container-in-docker-is-a-bad-idea/
2019年12月29日 星期日
Plex: Nifty new navigation
 |
Nifty new navigation
|
| Our universal navigation interface has been rolled out across all our devices, bringing a consistent navigation approach to all of our officially-supported apps. |
TrendLabs: Waterbear is Back, Uses API Hooking to Evade Security Product Detection
Figure 1. A typical Waterbear infection chain
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/waterbear-is-back-uses-api-hooking-to-evade-security-product-detection/
Cloudflare: Announcing deeper insights and new monitoring capabilities from Cloudflare Analytics

This week we’re excited to announce a number of new products and features that provide deeper security and reliability insights, “proactive” analytics when there’s a problem, and more powerful ways to explore your data.
REF: https://blog.cloudflare.com/announcing-deeper-insights-and-new-monitoring-capabilities/?utm_medium=email&utm_source=product-announcement&utm_campaign=analytics-week-2019
Plex: It’s the most moviest time of the year.
 |
| Pear trees, partridges, and calling birds don’t compare to unlimited FREE holiday movies on Plex. Get cozy and warm up with the “Holiday Yule Log”, then get in the spirit with A Belle for Christmas, Christmas All Over Again, Jingle Bells, A Christmas Carol, The Dog who Saved the Holidays and more. |
TrendLabs: (Almost) Hollow and Innocent: Monero Miner Remains Undetected via Process Hollowing
Figure 2. Arithmetic operations performed on the alphanumeric characters
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/almost-hollow-and-innocent-monero-miner-remains-undetected-via-process-hollowing/
Plex: Magical music
 |
| You now have the ability to add TIDAL content to your library so it shows up alongside your own personal music |
CodeWeavers: Announcing CrossOver 19.0.0
The capstone of CrossOver 19 is our new ability to run 32 bit Windows applications within a 64 bit process. This enables us to support 32 bit Windows applications on the new macOS release, Catalina, which removed all support for 32 bit applications in October.
...
In addition to that change, CrossOver’s core technology Wine has been updated to bring much of the developments of the past year to all of our users on both Mac and Linux. These changes include over 5,000 individual improvements, all of which will act together to improve the end user experience with CrossOver.
REF: https://www.codeweavers.com/support/forums/announce/?t=24;mhl=222780;msg=222780#msg222780
...
In addition to that change, CrossOver’s core technology Wine has been updated to bring much of the developments of the past year to all of our users on both Mac and Linux. These changes include over 5,000 individual improvements, all of which will act together to improve the end user experience with CrossOver.
REF: https://www.codeweavers.com/support/forums/announce/?t=24;mhl=222780;msg=222780#msg222780
TrendLabs: Obfuscation Tools Found in the Capesand Exploit Kit Possibly Used in “KurdishCoder” Campaign
Figure 9. Cassandra Crypter’s subscription plans
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/obfuscation-tools-found-in-the-capesand-exploit-kit-possibly-used-in-kurdishcoder-campaign/
ADMIN: Ubuntu Server 19.10 (Live)
- Support for nine months until July 2020
- Linux 5.3 kernel
- Updates to Qemu (v4.0), libvirt (v5.4), MySQL (v8.0), PostgreSQL (v11), and more
- A fresh set of fixes and refreshes to the installer
- A new Ubuntu Advantage service experience
Plex: Silky smooth content playback
 |
Silky smooth content playback
|
| For the last several months, we’ve been hard at work to enhance our playback engines, making sure your content looks as good and streams as smoothly as possible. |
MagicSoft Playout ver 7.4.10
MagicSoft Playout ver 7.4.10 was released and it adds :
REF: https://www.magicsoft.tv/news.html
- improved algorithm for assigning and calculating the duration of Live input entries
- support for importing playlists made on other databases (with different GUID identifier)
REF: https://www.magicsoft.tv/news.html
FSF: Replicant needs your help to liberate Android in 2020
The Free Software Foundation (FSF) supports the work of several important free software projects through fiscal sponsorship in a program we call Working Together for Free Software.
Donations to any of the Working Together for Free Software projects directly benefit the work that can be done. Too often, these projects are underfunded and developers are putting in a lot of personal time and effort to keep the project moving forward. Because of the FSF fiscal sponsorship, they can receive donations and apply for funding.
REF: https://www.fsf.org/blogs/community/replicant-needs-your-help-to-liberate-android-in-2020
Plex: Give the gift of Plex Pass
 |
Give the gift of Plex Pass
|
| Looking for a last minute holiday gift? Look no further than Plex! Give the gift that keeps on giving to someone you love. |
Proxmox VE 6.1 released
- Based on Debian Buster (10.2)
- Ceph Nautilus (14.2.4.1)
- Corosync 3.0
- Kernel 5.3
- LXC 3.2
- Qemu 4.1.1
- ZFS 0.8.2
REF: https://pve.proxmox.com/wiki/Roadmap#Proxmox_VE_6.1
TrendLabs: Mac Backdoor Linked to Lazarus Targets Korean Users
Figure 1. The spreadsheet displays a fairly known psychological test (similar to one found here); clicking on the smiley image on the top left shows a different response depending on the user’s answer.
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/mac-backdoor-linked-to-lazarus-targets-korean-users/
MagicSoft Recorder ver 2.3.0
MagicSoft Recorder ver 2.3.0 was released and it adds improved segmentation algorithm for better handling continuous recording ( 24/7/365 ).
REF: https://www.magicsoft.tv/news.html
REF: https://www.magicsoft.tv/news.html
How Cloudflare Stood up to a Patent Troll – and Won!

REF: https://blog.cloudflare.com/the-project-jengo-saga-how-cloudflare-stood-up-to-a-patent-troll-and-won/
[USN-4194-1] postgresql-common vulnerability
---------- Forwarded message ---------
Rich Mirch discovered that the postgresql-common pg_ctlcluster script
incorrectly handled directory creation. A local attacker could possibly use
this issue to escalate privileges.
References:
https://usn.ubuntu.com/4194-1
CVE-2019-3466
From: Marc Deslauriers
Date: Nov 15, 2019 3:42AM
Date: Nov 15, 2019 3:42AM
Rich Mirch discovered that the postgresql-common pg_ctlcluster script
incorrectly handled directory creation. A local attacker could possibly use
this issue to escalate privileges.
References:
https://usn.ubuntu.com/4194-1
CVE-2019-3466
TrendLabs: Operation ENDTRADE: Finding Multi-Stage Backdoors that TICK
Figure 1. Operation ENDTRADE’s timeline
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/operation-endtrade-finding-multi-stage-backdoors-that-tick/
TrendLabs: Microsoft November 2019 Patch Tuesday Reveals 74 Patches Before Major Windows Update
Following the relatively light list from last month, November proved to be a much more eventful month for Microsoft users. The November Patch Tuesday holds more fixes with a total of 74 patches, 13 of which were classified as Critical patches for remote code execution (RCE) vulnerabilities. The remaining majority were rated as Important and included patches for Windows graphics components and Microsoft SharePoint, among others. This Patch Tuesday also coincides with the start of the rollout of the Windows 10 November 2019 Update, which is now available to users as an opt-in version via Windows Update.
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/microsoft-november-2019-patch-tuesday-reveals-74-patches-before-major-windows-update/
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/microsoft-november-2019-patch-tuesday-reveals-74-patches-before-major-windows-update/
[USN-4191-2] QEMU vulnerabilities
---------- Forwarded message ---------
It was discovered that the LSI SCSI adapter emulator implementation in QEMU
did not properly validate executed scripts. A local attacker could use this
to cause a denial of service. (CVE-2019-12068)
Sergej Schumilo, Cornelius Aschermann and Simon Wörner discovered that the
qxl paravirtual graphics driver implementation in QEMU contained a null
pointer dereference. A local attacker in a guest could use this to cause a
denial of service. (CVE-2019-12155)
Riccardo Schirone discovered that the QEMU bridge helper did not properly
validate network interface names. A local attacker could possibly use this
to bypass ACL restrictions. (CVE-2019-13164)
It was discovered that a heap-based buffer overflow existed in the SLiRP
networking implementation of QEMU. A local attacker in a guest could use
this to cause a denial of service or possibly execute arbitrary code in the
host. (CVE-2019-14378)
It was discovered that a use-after-free vulnerability existed in the SLiRP
networking implementation of QEMU. A local attacker in a guest could use
this to cause a denial of service. (CVE-2019-15890)
References:
https://usn.ubuntu.com/4191-2
https://usn.ubuntu.com/4191-1
CVE-2019-12068, CVE-2019-12155, CVE-2019-13164, CVE-2019-14378,
CVE-2019-15890
From: Steve Beattie
Date: Nov 14, 2019 9:04AM
Date: Nov 14, 2019 9:04AM
It was discovered that the LSI SCSI adapter emulator implementation in QEMU
did not properly validate executed scripts. A local attacker could use this
to cause a denial of service. (CVE-2019-12068)
Sergej Schumilo, Cornelius Aschermann and Simon Wörner discovered that the
qxl paravirtual graphics driver implementation in QEMU contained a null
pointer dereference. A local attacker in a guest could use this to cause a
denial of service. (CVE-2019-12155)
Riccardo Schirone discovered that the QEMU bridge helper did not properly
validate network interface names. A local attacker could possibly use this
to bypass ACL restrictions. (CVE-2019-13164)
It was discovered that a heap-based buffer overflow existed in the SLiRP
networking implementation of QEMU. A local attacker in a guest could use
this to cause a denial of service or possibly execute arbitrary code in the
host. (CVE-2019-14378)
It was discovered that a use-after-free vulnerability existed in the SLiRP
networking implementation of QEMU. A local attacker in a guest could use
this to cause a denial of service. (CVE-2019-15890)
References:
https://usn.ubuntu.com/4191-2
https://usn.ubuntu.com/4191-1
CVE-2019-12068, CVE-2019-12155, CVE-2019-13164, CVE-2019-14378,
CVE-2019-15890
Plex: Name that Tunefind!
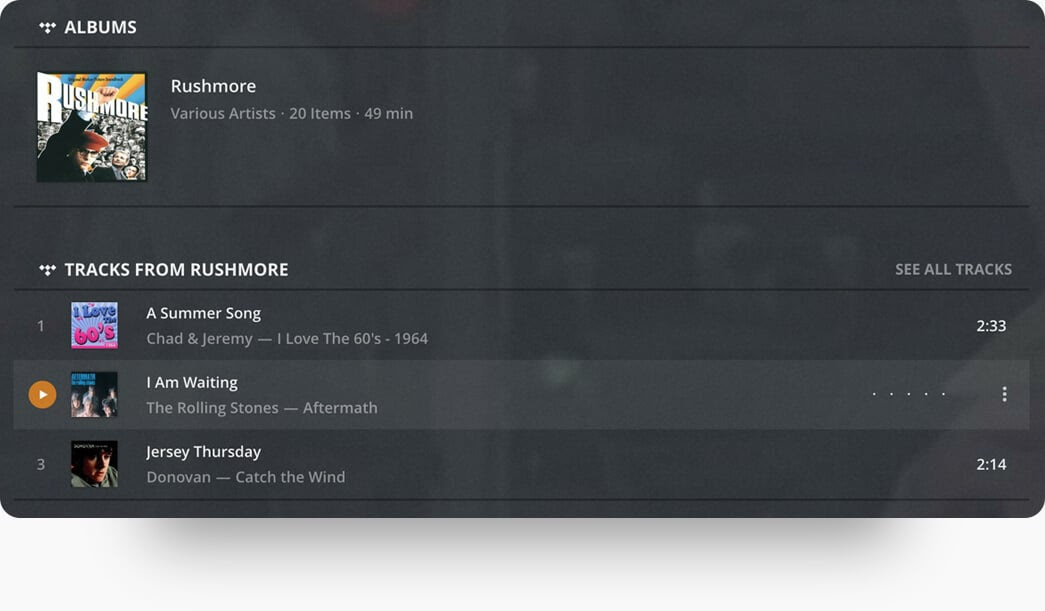 |
| Name that Tunefind! |
| Not sure about you, but sometimes when we hear a song on a show or movie, we gotta know what it is, particularly those hidden gems that don’t show up on the soundtrack. |
| Worry no more— we have integrated an awesome service from a company called Tunefind into Plex to do the work for you. Go to the preplay screen for movies or TV episodes on your server and see all the tracks that are found in the episode or film, playable right in Plex, using TIDAL’s massive library! |
[USN-4223-1] OpenJDK vulnerabilities
---------- Forwarded message ---------
From: Steve Beattie
Date: Dec 18, 2019 7:53AM
Several security issues were fixed in OpenJDK.
Software Description:
- openjdk-lts: Open Source Java implementation
- openjdk-8: Open Source Java implementation
References:
https://usn.ubuntu.com/4223-1
CVE-2019-2894, CVE-2019-2945, CVE-2019-2949, CVE-2019-2962,
CVE-2019-2964, CVE-2019-2973, CVE-2019-2975, CVE-2019-2977,
CVE-2019-2978, CVE-2019-2981, CVE-2019-2983, CVE-2019-2987,
CVE-2019-2988, CVE-2019-2989, CVE-2019-2992, CVE-2019-2999
From: Steve Beattie
Date: Dec 18, 2019 7:53AM
Several security issues were fixed in OpenJDK.
Software Description:
- openjdk-lts: Open Source Java implementation
- openjdk-8: Open Source Java implementation
References:
https://usn.ubuntu.com/4223-1
CVE-2019-2894, CVE-2019-2945, CVE-2019-2949, CVE-2019-2962,
CVE-2019-2964, CVE-2019-2973, CVE-2019-2975, CVE-2019-2977,
CVE-2019-2978, CVE-2019-2981, CVE-2019-2983, CVE-2019-2987,
CVE-2019-2988, CVE-2019-2989, CVE-2019-2992, CVE-2019-2999
TrendLabs: Patched GIF Processing Vulnerability CVE-2019-11932 Still Afflicts Multiple Mobile Apps
2019年12月4日 星期三
[USN-4195-1] MySQL vulnerabilities
---------- Forwarded message ---------
MySQL has been updated to 8.0.18 in Ubuntu 19.10. Ubuntu 16.04 LTS, Ubuntu
18.04 LTS, and Ubuntu 19.04 have been updated to MySQL 5.7.28.
In addition to security fixes, the updated packages contain bug fixes, new
features, and possibly incompatible changes.
Please see the following for more information:
https://dev.mysql.com/doc/reln
https://dev.mysql.com/doc/reln
https://www.oracle.com/securit
References:
https://usn.ubuntu.com/4195-1
CVE-2019-2910, CVE-2019-2911, CVE-2019-2914, CVE-2019-2920,
CVE-2019-2922, CVE-2019-2923, CVE-2019-2924, CVE-2019-2938,
CVE-2019-2946, CVE-2019-2948, CVE-2019-2950, CVE-2019-2957,
CVE-2019-2960, CVE-2019-2963, CVE-2019-2966, CVE-2019-2967,
CVE-2019-2968, CVE-2019-2969, CVE-2019-2974, CVE-2019-2982,
CVE-2019-2991, CVE-2019-2993, CVE-2019-2997, CVE-2019-2998,
CVE-2019-3003, CVE-2019-3004, CVE-2019-3009, CVE-2019-3011,
CVE-2019-3018
From: Marc Deslauriers
Date: Nov 18, 2019 10:22PM
Date: Nov 18, 2019 10:22PM
18.04 LTS, and Ubuntu 19.04 have been updated to MySQL 5.7.28.
In addition to security fixes, the updated packages contain bug fixes, new
features, and possibly incompatible changes.
Please see the following for more information:
https://dev.mysql.com/doc/reln
https://dev.mysql.com/doc/reln
https://www.oracle.com/securit
References:
https://usn.ubuntu.com/4195-1
CVE-2019-2910, CVE-2019-2911, CVE-2019-2914, CVE-2019-2920,
CVE-2019-2922, CVE-2019-2923, CVE-2019-2924, CVE-2019-2938,
CVE-2019-2946, CVE-2019-2948, CVE-2019-2950, CVE-2019-2957,
CVE-2019-2960, CVE-2019-2963, CVE-2019-2966, CVE-2019-2967,
CVE-2019-2968, CVE-2019-2969, CVE-2019-2974, CVE-2019-2982,
CVE-2019-2991, CVE-2019-2993, CVE-2019-2997, CVE-2019-2998,
CVE-2019-3003, CVE-2019-3004, CVE-2019-3009, CVE-2019-3011,
CVE-2019-3018
TrendLabs: Mobile Cyberespionage Campaign Distributed Through CallerSpy Mounts Initial Phase of a Targeted Attack
Figure 1. Screenshots of Chatrious (left) and Apex App (right)
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/mobile-cyberespionage-campaign-distributed-through-callerspy-mounts-initial-phase-of-a-targeted-attack/
[Checkmk Announce] New Checkmk stable release 1.6.0p6
---------- Forwarded message ---------
From: Checkmk Announcements
Date: Tue, Nov 12, 2019 at 4:34 AM
Checks & agents:
* 10194 Windows Agent: logwatch section size is limited now
* 10157 FIX: Now using /dev/null instead of closing stdin in all POSIX agents
* 10196 FIX: All text file of the Windows Agent now have Windows style line endings
* 10405 FIX: Allow filesystems in /var/lib/docker/ to be monitored
* 10156 FIX: Crash upon unexpected resource ID
* 10406 FIX: Fix Domino task check pluging to use newer PS check functions
* 10446 FIX: Output bits/s with the appropriate SI magnitude
* 10308 FIX: Recover performance data output for averaged bandwidth use in IF checks
* 10310 FIX: Remove duplicated check-output in IF checks on average data
* 10487 FIX: Warn if host has tag "Always use and expect piggback data" and no piggyback data is available
* 10192 FIX: Windows Agent User Config file is no more reset after service restart
* 10193 FIX: Windows Agent: Invalid entries have been removed from logwatch
* 10360 FIX: agent_aws: Fetch live data from AWS if special agent configuration has changed
* 8799 FIX: agent_kubernetes: accept millibytes as unit
* 8798 FIX: agent_kubernetes: allow the option 'No IP' for the Kubernetes master
* 10329 FIX: agent_splunk: Prevent InsecureRequestWarning
* 10358 FIX: check_mail_loop: Fixed exception: Failed to fetch mail NR ('NoneType' object has no attribute '__getitem__')
* 10448 FIX: emc_datadomain_mtree: add missing metric definition
* 10155 FIX: emcvnx_storage_pools: Crash upon missing auto-tiering info
* 10494 FIX: lnx_if: Fixed confusion of interface state UNKNOWN, DOWN if ethtool output is missing
* 10507 FIX: mk_oracle: Fixed missing option to set the TNS_ADMIN in the bakery
* 10508 FIX: mk_oracle: Fixed missing sysdg as role choice
* 10348 FIX: mssql_databases: Do not alert if instance is not running
* 10509 FIX: oracle_rman: Fixed wrong incremental Level 1 Backup
* 10449 FIX: ps: cleanup counters of processes which do not exist anymore
* 10300 FIX: sym_brightmail_queues: bug fix where WATO configuration did not alter behaviour
* 10408 FIX: Don't discover lparstat service on host without util info
NOTE: Please refer to the migration notes!
* 10447 FIX: agent_kubernetes: use new API versions
NOTE: Please refer to the migration notes!
* 10356 FIX: bluenet2_powerrail.{temp,humidity}: Fixed discovery of ALL temperature and humidity sensors
NOTE: Please refer to the migration notes!
* 8806 FIX: mk_oracle: Fixed discovery of XE instances on Oracle 18c
NOTE: Please refer to the migration notes!
* 8805 FIX: mk_oracle: Fixed jobs with auto_drop
NOTE: Please refer to the migration notes!
* 10359 FIX: mk_oracle: better support for mounted databases
NOTE: Please refer to the migration notes!
Core & setup:
* 10377 FIX: Fix terminating "cmk --update-dns-cache" with CTRL+C
* 10378 FIX: Improve "Update DNS cache" / cmk --update-dns-cache performance
* 7281 FIX: legacy local plugins: added missing register_hook call
Event console:
* 8797 FIX: Show the Contact Person in the Event Details view
HW/SW inventory:
* 10342 FIX: HW/SW Inventory: Do not overwrite inventory tree if ALL data sources of a host fail
* 10351 FIX: HW/SW Inventory: Do not pollute inventory archive if two numerations have different order but same entries
* 10347 FIX: if: Moved last change field to status data tree; otherwise the inventory history may be polluted
* 10346 FIX: lnx_if winperf_if if solaris_addresses: Fixed sorting interfaces; otherwise the inventory history may be polluted
* 10344 FIX: lnx_if: Do not inventorize dynamic IPv6 addresses which may pollute inventory history
* 10493 FIX: lnx_if: Use MAC address from command 'ip' if the command 'ethtool' is not available
* 10270 FIX: solaris_mem: Fix value and unit
NOTE: Please refer to the migration notes!
Other components:
* 10374 NagVis: Updated to 1.9.16
* 10372 FIX: stunnel: Improve logging of the daemon
Site management:
* 10371 FIX: omd restore: Fix possible version issues when default version is not the site version
* 10376 FIX: omd: Fix possible stopped system apache after removing a site
User interface:
* 10510 Added more link views for Host Groups (Summary)
* 10382 FIX: Dashboard: Add missing link for creating a new view as dashlet
* 10455 FIX: Don't display classical checkboxes in mobile GUI
* 10454 FIX: Don't show an error in Commands of mobile GUI
* 10373 FIX: Fix distributed update issue related to missing theme directory
* 10381 FIX: Fix editing dashlet views
* 10456 FIX: Fix redirection from login page in mobile GUI
* 10380 FIX: Fix view action menu in dashlets
* 10350 FIX: Fixed #rows on rulesets pages
* 10384 FIX: IE11 incompatibility: Fix reordering view painters
* 10489 FIX: Move ruleset "Piggybacked Host Files" to group "Access to Agents"
* 7285 FIX: Network Topology: fixed exception in exception when the maximal allowed node limit has been reached
* 10265 FIX: Password policy: Do not apply expiration time for LDAP users
* 10490 FIX: Rename ruleset "Piggybacked Host Files" to "Processing of Piggybacked Host Data"
* 10228 FIX: Several minor GUI fixes
* 10453 FIX: Show graphs in the mobile GUI
* 10452 FIX: Use mobile GUI for mobile devices
WATO:
* 10407 FIX: Consistent naming for levels in Check SQL Database active check
* 10264 FIX: Discovery page: Fix missing "toggle all" checkboxes (1.6.0p2 regression)
* 10379 FIX: Hostname search: Host bulk actions affected all hosts (1.6.0p4 regression)
* 10383 FIX: Make more background job results deletable
* 10375 FIX: NagVis backends now work with encrypted Livestatus
* 10287 FIX: Service Discovery: fix re-enabling services which were disabled in 1.4.0
* 10546 FIX: WATO changes: Improve table rendering with many affected sites
You can download Checkmk from our download page:
* https://checkmk.com/download.php
From: Checkmk Announcements
Date: Tue, Nov 12, 2019 at 4:34 AM
Checks & agents:
* 10194 Windows Agent: logwatch section size is limited now
* 10157 FIX: Now using /dev/null instead of closing stdin in all POSIX agents
* 10196 FIX: All text file of the Windows Agent now have Windows style line endings
* 10405 FIX: Allow filesystems in /var/lib/docker/ to be monitored
* 10156 FIX: Crash upon unexpected resource ID
* 10406 FIX: Fix Domino task check pluging to use newer PS check functions
* 10446 FIX: Output bits/s with the appropriate SI magnitude
* 10308 FIX: Recover performance data output for averaged bandwidth use in IF checks
* 10310 FIX: Remove duplicated check-output in IF checks on average data
* 10487 FIX: Warn if host has tag "Always use and expect piggback data" and no piggyback data is available
* 10192 FIX: Windows Agent User Config file is no more reset after service restart
* 10193 FIX: Windows Agent: Invalid entries have been removed from logwatch
* 10360 FIX: agent_aws: Fetch live data from AWS if special agent configuration has changed
* 8799 FIX: agent_kubernetes: accept millibytes as unit
* 8798 FIX: agent_kubernetes: allow the option 'No IP' for the Kubernetes master
* 10329 FIX: agent_splunk: Prevent InsecureRequestWarning
* 10358 FIX: check_mail_loop: Fixed exception: Failed to fetch mail NR ('NoneType' object has no attribute '__getitem__')
* 10448 FIX: emc_datadomain_mtree: add missing metric definition
* 10155 FIX: emcvnx_storage_pools: Crash upon missing auto-tiering info
* 10494 FIX: lnx_if: Fixed confusion of interface state UNKNOWN, DOWN if ethtool output is missing
* 10507 FIX: mk_oracle: Fixed missing option to set the TNS_ADMIN in the bakery
* 10508 FIX: mk_oracle: Fixed missing sysdg as role choice
* 10348 FIX: mssql_databases: Do not alert if instance is not running
* 10509 FIX: oracle_rman: Fixed wrong incremental Level 1 Backup
* 10449 FIX: ps: cleanup counters of processes which do not exist anymore
* 10300 FIX: sym_brightmail_queues: bug fix where WATO configuration did not alter behaviour
* 10408 FIX: Don't discover lparstat service on host without util info
NOTE: Please refer to the migration notes!
* 10447 FIX: agent_kubernetes: use new API versions
NOTE: Please refer to the migration notes!
* 10356 FIX: bluenet2_powerrail.{temp,humidity}: Fixed discovery of ALL temperature and humidity sensors
NOTE: Please refer to the migration notes!
* 8806 FIX: mk_oracle: Fixed discovery of XE instances on Oracle 18c
NOTE: Please refer to the migration notes!
* 8805 FIX: mk_oracle: Fixed jobs with auto_drop
NOTE: Please refer to the migration notes!
* 10359 FIX: mk_oracle: better support for mounted databases
NOTE: Please refer to the migration notes!
Core & setup:
* 10377 FIX: Fix terminating "cmk --update-dns-cache" with CTRL+C
* 10378 FIX: Improve "Update DNS cache" / cmk --update-dns-cache performance
* 7281 FIX: legacy local plugins: added missing register_hook call
Event console:
* 8797 FIX: Show the Contact Person in the Event Details view
HW/SW inventory:
* 10342 FIX: HW/SW Inventory: Do not overwrite inventory tree if ALL data sources of a host fail
* 10351 FIX: HW/SW Inventory: Do not pollute inventory archive if two numerations have different order but same entries
* 10347 FIX: if: Moved last change field to status data tree; otherwise the inventory history may be polluted
* 10346 FIX: lnx_if winperf_if if solaris_addresses: Fixed sorting interfaces; otherwise the inventory history may be polluted
* 10344 FIX: lnx_if: Do not inventorize dynamic IPv6 addresses which may pollute inventory history
* 10493 FIX: lnx_if: Use MAC address from command 'ip' if the command 'ethtool' is not available
* 10270 FIX: solaris_mem: Fix value and unit
NOTE: Please refer to the migration notes!
Other components:
* 10374 NagVis: Updated to 1.9.16
* 10372 FIX: stunnel: Improve logging of the daemon
Site management:
* 10371 FIX: omd restore: Fix possible version issues when default version is not the site version
* 10376 FIX: omd: Fix possible stopped system apache after removing a site
User interface:
* 10510 Added more link views for Host Groups (Summary)
* 10382 FIX: Dashboard: Add missing link for creating a new view as dashlet
* 10455 FIX: Don't display classical checkboxes in mobile GUI
* 10454 FIX: Don't show an error in Commands of mobile GUI
* 10373 FIX: Fix distributed update issue related to missing theme directory
* 10381 FIX: Fix editing dashlet views
* 10456 FIX: Fix redirection from login page in mobile GUI
* 10380 FIX: Fix view action menu in dashlets
* 10350 FIX: Fixed #rows on rulesets pages
* 10384 FIX: IE11 incompatibility: Fix reordering view painters
* 10489 FIX: Move ruleset "Piggybacked Host Files" to group "Access to Agents"
* 7285 FIX: Network Topology: fixed exception in exception when the maximal allowed node limit has been reached
* 10265 FIX: Password policy: Do not apply expiration time for LDAP users
* 10490 FIX: Rename ruleset "Piggybacked Host Files" to "Processing of Piggybacked Host Data"
* 10228 FIX: Several minor GUI fixes
* 10453 FIX: Show graphs in the mobile GUI
* 10452 FIX: Use mobile GUI for mobile devices
WATO:
* 10407 FIX: Consistent naming for levels in Check SQL Database active check
* 10264 FIX: Discovery page: Fix missing "toggle all" checkboxes (1.6.0p2 regression)
* 10379 FIX: Hostname search: Host bulk actions affected all hosts (1.6.0p4 regression)
* 10383 FIX: Make more background job results deletable
* 10375 FIX: NagVis backends now work with encrypted Livestatus
* 10287 FIX: Service Discovery: fix re-enabling services which were disabled in 1.4.0
* 10546 FIX: WATO changes: Improve table rendering with many affected sites
You can download Checkmk from our download page:
* https://checkmk.com/download.php
[LSN-0059-1] Linux kernel vulnerability
---------- Forwarded message ---------
Date: Nov 13, 2019 7:43AM
CVE-2018-12207
On an Ubuntu KVM host configured to use huge pages, a malicious KVM guest
can cause a host machine check exception (MCE) capable of bringing down
the host OS.
CVE-2019-0154
On Intel processors containing an i915 graphics processing unit, it is
possible from userspace to cause a GPU hang in certain low-power states by
reading a specific memory-mapped IO register.
CVE-2019-0155
On Intel processors containing an i915 graphics processing unit, it is
possible to use the GPU's blitter command streamer to write to
memory-mapped IO locations, which could be used for privilege escalation
or to leak kernel memory.
CVE-2019-11135
On Intel processors with support for Transactional Synchronization
Extensions (TSX), it is possible to exploit a transactional asynchronous
abort (TAA) to perform a side-channel attack and leak kernel memory.
References:
CVE-2018-12207, CVE-2019-0154, CVE-2019-0155, CVE-2019-11135
Date: Nov 13, 2019 7:43AM
CVE-2018-12207
On an Ubuntu KVM host configured to use huge pages, a malicious KVM guest
can cause a host machine check exception (MCE) capable of bringing down
the host OS.
CVE-2019-0154
On Intel processors containing an i915 graphics processing unit, it is
possible from userspace to cause a GPU hang in certain low-power states by
reading a specific memory-mapped IO register.
CVE-2019-0155
On Intel processors containing an i915 graphics processing unit, it is
possible to use the GPU's blitter command streamer to write to
memory-mapped IO locations, which could be used for privilege escalation
or to leak kernel memory.
CVE-2019-11135
On Intel processors with support for Transactional Synchronization
Extensions (TSX), it is possible to exploit a transactional asynchronous
abort (TAA) to perform a side-channel attack and leak kernel memory.
References:
CVE-2018-12207, CVE-2019-0154, CVE-2019-0155, CVE-2019-11135
TrendLabs: 49 Disguised Adware Apps With Optimized Evasion Features Found on Google Play
Figure 2. Screen captures of codes showing how the malicious app’s icon is hidden or removed
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/49-disguised-adware-apps-with-optimized-evasion-features-found-on-google-play/
[Openvpn-announce] OpenVPN 2.4.8 released
---------- Forwarded message ---------
From: Samuli Seppänen
Date: Thu, Oct 31, 2019 at 6:37 PM
This is primarily a maintenance release with bugfixes and improvements.
The Windows installers (I601) have several improvements compared to the
previous release:
* New tap-windows6 driver (9.24.2) which fixes some suspend and resume
issues
* Latest OpenVPN-GUI
* Considerable performance boost due to new compiler optimization flags
Please note that LibreSSL is not a supported crypto backend. We accept
patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if
newer versions of LibreSSL break API compatibility we do not take
responsibility to fix that.
From: Samuli Seppänen
Date: Thu, Oct 31, 2019 at 6:37 PM
This is primarily a maintenance release with bugfixes and improvements.
The Windows installers (I601) have several improvements compared to the
previous release:
* New tap-windows6 driver (9.24.2) which fixes some suspend and resume
issues
* Latest OpenVPN-GUI
* Considerable performance boost due to new compiler optimization flags
Please note that LibreSSL is not a supported crypto backend. We accept
patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if
newer versions of LibreSSL break API compatibility we do not take
responsibility to fix that.
TrendLabs: More than a Dozen Obfuscated APT33 Botnets Used for Extreme Narrow Targeting
Figure 1. Schema showing the multiple obfuscation layers that APT33 uses
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/more-than-a-dozen-obfuscated-apt33-botnets-used-for-extreme-narrow-targeting/
[USN-4167-1] Samba vulnerabilities
---------- Forwarded message ---------
From: Marc Deslauriers
Date: Oct 29, 2019 9:20PM
Michael Hanselmann discovered that the Samba client code incorrectly
handled path separators. If a user were tricked into connecting to a
malicious server, a remote attacker could use this issue to cause the
client to access local pathnames instead of network pathnames.
(CVE-2019-10218)
Simon Fonteneau and Björn Baumbach discovered that Samba incorrectly
handled the check password script. This issue could possibly bypass custom
password complexity checks, contrary to expectations. This issue only
affected Ubuntu 18.04 LTS, Ubuntu 19.04, and Ubuntu 19.10. (CVE-2019-14833)
Adam Xu discovered that Samba incorrectly handled the dirsync LDAP control.
A remote attacker with "get changes" permissions could possibly use this
issue to cause Samba to crash, resulting in a denial of service.
(CVE-2019-14847)
References:
https://usn.ubuntu.com/4167-1
CVE-2019-10218, CVE-2019-14833, CVE-2019-14847
From: Marc Deslauriers
Date: Oct 29, 2019 9:20PM
Michael Hanselmann discovered that the Samba client code incorrectly
handled path separators. If a user were tricked into connecting to a
malicious server, a remote attacker could use this issue to cause the
client to access local pathnames instead of network pathnames.
(CVE-2019-10218)
Simon Fonteneau and Björn Baumbach discovered that Samba incorrectly
handled the check password script. This issue could possibly bypass custom
password complexity checks, contrary to expectations. This issue only
affected Ubuntu 18.04 LTS, Ubuntu 19.04, and Ubuntu 19.10. (CVE-2019-14833)
Adam Xu discovered that Samba incorrectly handled the dirsync LDAP control.
A remote attacker with "get changes" permissions could possibly use this
issue to cause Samba to crash, resulting in a denial of service.
(CVE-2019-14847)
References:
https://usn.ubuntu.com/4167-1
CVE-2019-10218, CVE-2019-14833, CVE-2019-14847
TrendLabs: New Exploit Kit Capesand Reuses Old and New Public Exploits and Tools, Blockchain Ruse
MagicSoft CG ver 8.2.3
MagicSoft CG ver 8.2.3 adds :
- NDI input and output for all video modes
- improved performance in 4K video modes for "picture in picture" when using Decklink or NDI as input
- improved management of the projects in CG server
REF: https://www.magicsoft.tv/news.html
- NDI input and output for all video modes
- improved performance in 4K video modes for "picture in picture" when using Decklink or NDI as input
- improved management of the projects in CG server
TrendLabs: Current and Future Hacks and Attacks that Threaten Esports

Figure 1. Page offering custom hardware hacks, with prices starting at US$500
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/current-and-future-hacks-and-attacks-that-threaten-esports/
LM: Red Hat Announces CentOS Stream
CentOS Stream will sit somewhere between Fedora and RHEL to provide a place for developers who want to get their packages in RHEL. So far Fedora was used as a fast moving upstream project for RHEL. Red Hat forks code from Fedora to build the next version of RHEL. However, most enterprise-centric users were on CentOS and not Fedora, and there was not a direct path for those users to target RHEL, as CentOS was downstream of RHEL. With CentOS stream, developers can start playing with what to expect next in RHEL, and they can also submit patches.
REF: http://www.linux-magazine.com/Online/News/Red-Hat-Announces-CentOS-Stream
REF: http://www.linux-magazine.com/Online/News/Red-Hat-Announces-CentOS-Stream
Plex: Multitask Live TV and DVR on Apple
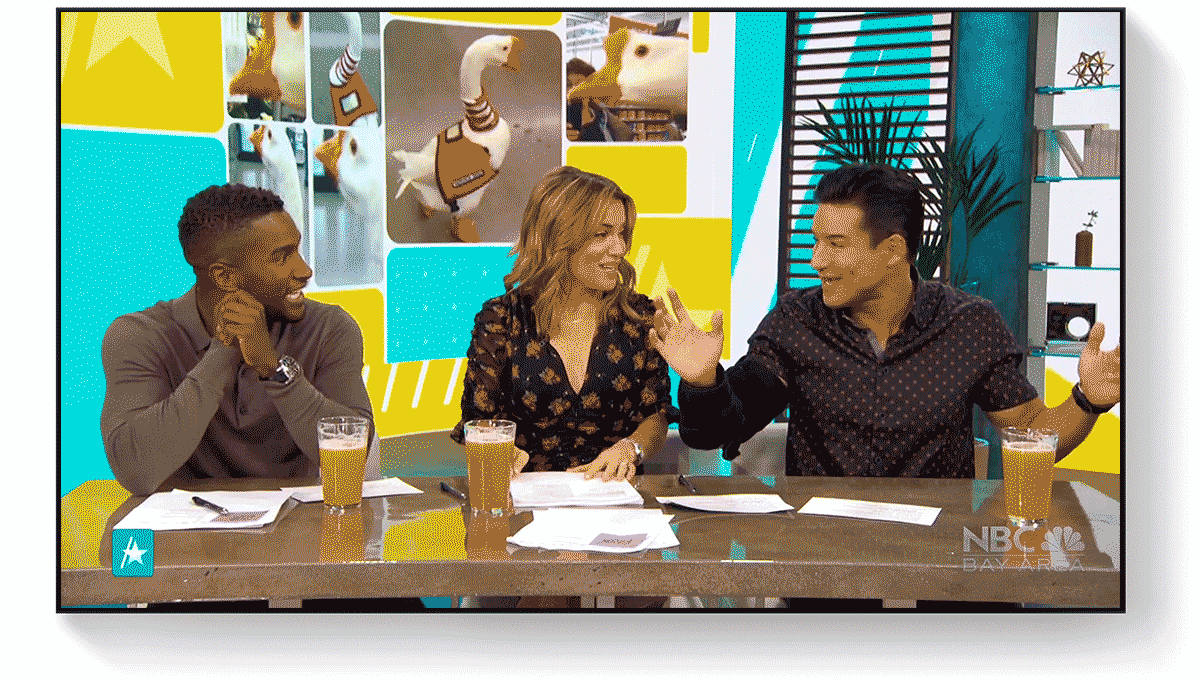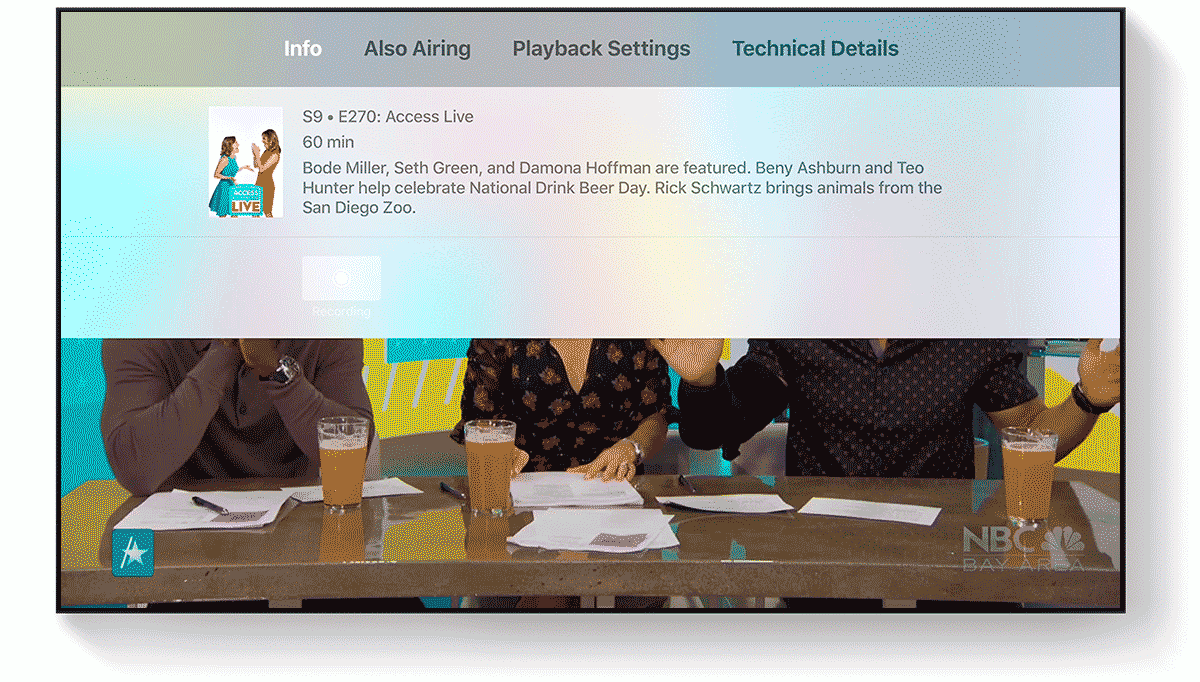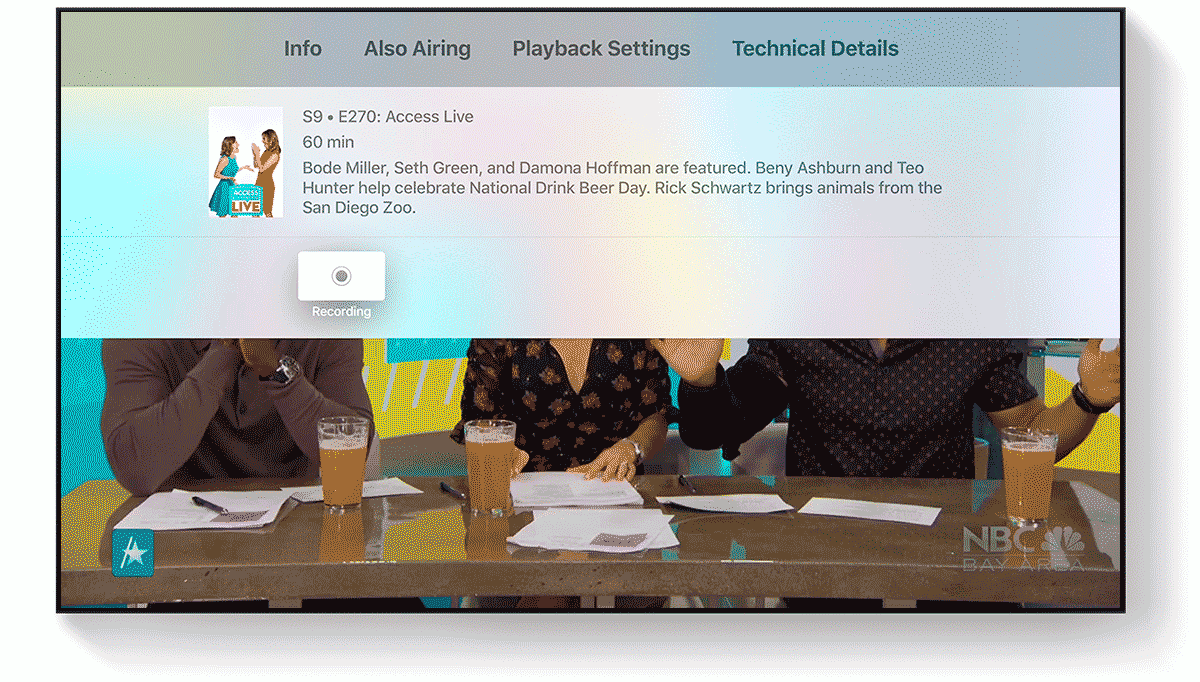 |
Multitask Live TV and DVR on Apple
|
| Professional binge watchers rejoice! Now for iOS and Apple TV users, you can simultaneously watch Live TV while scheduling your next recording without missing a beat. |
2019年11月20日 星期三
[USN-4166-2] PHP vulnerability
---------- Forwarded message ---------
From: Leonidas S. Barbosa
Date: Oct 29, 2019 8:32PM
It was discovered that PHP incorrectly handled certain paths when being
used in FastCGI configurations. A remote attacker could possibly use this
issue to execute arbitrary code.
References:
https://usn.ubuntu.com/4166-2
https://usn.ubuntu.com/4166-1
CVE-2019-11043
From: Leonidas S. Barbosa
Date: Oct 29, 2019 8:32PM
It was discovered that PHP incorrectly handled certain paths when being
used in FastCGI configurations. A remote attacker could possibly use this
issue to execute arbitrary code.
References:
https://usn.ubuntu.com/4166-2
https://usn.ubuntu.com/4166-1
CVE-2019-11043
TrendLabs: AutoIT-compiled Negasteal/Agent Tesla, Ave Maria Delivered via Malspam
Figure 1. A fake shipment advisory spam email that has a .RAR attachment containing Negasteal
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/autoit-compiled-negasteal-agent-tesla-ave-maria-delivered-via-malspam/
[USN-4161-1] Linux kernel vulnerability
---------- Forwarded message ---------
It was discovered that the IPv6 routing implementation in the Linux kernel
contained a reference counting error leading to a use-after-free
vulnerability. A local attacker could use this to cause a denial of service
(system crash) or possibly execute arbitrary code.
References:
https://usn.ubuntu.com/4161-1
CVE-2019-18198
From: Seth Arnold
Date: Oct 22, 2019 5:04AM
Date: Oct 22, 2019 5:04AM
It was discovered that the IPv6 routing implementation in the Linux kernel
contained a reference counting error leading to a use-after-free
vulnerability. A local attacker could use this to cause a denial of service
(system crash) or possibly execute arbitrary code.
References:
https://usn.ubuntu.com/4161-1
CVE-2019-18198
TrendLabs: Fake Photo Beautification Apps on Google Play can Read SMS Verification Code to Trigger Wireless Application Protocol (WAP)/Carrier Billing

Figure 1. Screenshot showing reviews about the app; one user noted how she lost mobile credits after installing the app
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/fake-photo-beautification-apps-on-google-play-can-read-sms-verification-code-to-trigger-wireless-application-protocol-wap-carrier-billing/
[Checkmk Announce] New Checkmk stable release 1.5.0p23
---------- Forwarded message ---------
From: Checkmk Announcements
Date: Tue, Oct 29, 2019 at 5:12 AM
WATO:
* 10106 FIX: GUI: Fix mismatched unit on PING packet-loss graph
* 10120 FIX: Fixed error handling in automation calls
* 10261 FIX: API: The edit_users call can now be used to edit LDAP users
User interface:
* 10265 FIX: Password policy: Do not apply expiration time for LDAP users
* 10350 FIX: Fixed #rows on rulesets pages
Site management:
* 10371 FIX: omd restore: Fix possible version issues when default version is not the site version
* 10256 FIX: Debian Buster: Fix missing check_snmp active check plugin
Notifications:
* 8793 FIX: notifications crash if non ASCII characters are present in the plugin output
* 8794 FIX: mail: SSL/TLS and STARTTLS options were not used
HW/SW inventory:
* 10346 FIX: lnx_if winperf_if if solaris_addresses: Fixed sorting interfaces; otherwise the inventory history may be polluted
* 10347 FIX: if: Moved last change field to status data tree; otherwise the inventory history may be polluted
* 10219 FIX: HW/SW Inventory: Fixed filtering inventory tree if permitted paths are configured in contact groups
* 10223 FIX: HW/SW Inventory: Do not save inventory tree if Checkmk service calculates status data inventory
* 10351 FIX: HW/SW Inventory: Do not pollute inventory archive if two numerations have different order but same entries
* 10207 FIX: HW/SW Inventory History: Skip delta trees if no changes
Event console:
* 8797 FIX: Show the Contact Person in the Event Details view
* 10307 FIX: Resolve conflict event console archive event
* 10040 FIX: Fix wrong core host name in events when using host name rewriting
Core & setup:
* 10361 FIX: MKTimeout exceptions no longer fails with no argument
Checks & agents:
* 10059 RAM Leak Protection for Windows Agent 1.5
* 8999 FIX: tcp_conn_stats: display of all tcp metrics in one single graph
* 10300 FIX: sym_brightmail_queues: bug fix where WATO configuration did not alter behaviour
* 10105 FIX: oracle_rman: don't crash on intermittent connection loss
* 7720 FIX: oracle_logswitches: Handle db error maybe provided via the agent output
* 10211 FIX: netapp_api_volumes: Fixed scaling of latency values for ALL protocols
* 10348 FIX: mssql_databases: Do not alert if instance is not running
* 10151 FIX: mssql: Sanitize mssql ini file name
NOTE: Please refer to the migration notes!
* 10006 FIX: mk_logwatch: Do not crash upon non-matching optional subgroups and rewrites
* 10154 FIX: mgmt_ipmi_sensors: Missing service details for IPMI sensors services
NOTE: Please refer to the migration notes!
* 10267 FIX: dell_compellent_disks would not see more than 9 disks
* 10102 FIX: cifsmounts: Now displays performance data as check plugin nfsmounts does
* 10358 FIX: check_mail_loop: Fixed exception: Failed to fetch mail NR ('NoneType' object has no attribute '__getitem__')
* 10101 FIX: aws_rds.{bin_log_usage,transaction_logs_usage,replication_slot_usage}: Fixed discovering services
* 10103 FIX: agent_aws: Skip S3 buckets for which the location cannot be retrieved (AccessDenied)
* 10210 FIX: agent_aws: Fixed FilterLimitExceeded while collecting EC2 instance attributes
* 10189 FIX: Windows Agent reports allowed IP addresses correctly
* 10085 FIX: Service discovery page: Do not show long output of services
* 10308 FIX: Recover performance data output for averaged bandwidth use in IF checks
* 8914 FIX: Fix calculation of latency for netapp_api_vs_traffic 2
* 10108 FIX: Fix apt check when switched to "dist-upgrade" and encountering auto removals
* 10094 FIX: Checkmk Discovery: Fixed crash if a host has no data sources configured
* 10091 FIX: Agent AWS: Let EC2 services become stale if the instance was terminated
From: Checkmk Announcements
Date: Tue, Oct 29, 2019 at 5:12 AM
WATO:
* 10106 FIX: GUI: Fix mismatched unit on PING packet-loss graph
* 10120 FIX: Fixed error handling in automation calls
* 10261 FIX: API: The edit_users call can now be used to edit LDAP users
User interface:
* 10265 FIX: Password policy: Do not apply expiration time for LDAP users
* 10350 FIX: Fixed #rows on rulesets pages
Site management:
* 10371 FIX: omd restore: Fix possible version issues when default version is not the site version
* 10256 FIX: Debian Buster: Fix missing check_snmp active check plugin
Notifications:
* 8793 FIX: notifications crash if non ASCII characters are present in the plugin output
* 8794 FIX: mail: SSL/TLS and STARTTLS options were not used
HW/SW inventory:
* 10346 FIX: lnx_if winperf_if if solaris_addresses: Fixed sorting interfaces; otherwise the inventory history may be polluted
* 10347 FIX: if: Moved last change field to status data tree; otherwise the inventory history may be polluted
* 10219 FIX: HW/SW Inventory: Fixed filtering inventory tree if permitted paths are configured in contact groups
* 10223 FIX: HW/SW Inventory: Do not save inventory tree if Checkmk service calculates status data inventory
* 10351 FIX: HW/SW Inventory: Do not pollute inventory archive if two numerations have different order but same entries
* 10207 FIX: HW/SW Inventory History: Skip delta trees if no changes
Event console:
* 8797 FIX: Show the Contact Person in the Event Details view
* 10307 FIX: Resolve conflict event console archive event
* 10040 FIX: Fix wrong core host name in events when using host name rewriting
Core & setup:
* 10361 FIX: MKTimeout exceptions no longer fails with no argument
Checks & agents:
* 10059 RAM Leak Protection for Windows Agent 1.5
* 8999 FIX: tcp_conn_stats: display of all tcp metrics in one single graph
* 10300 FIX: sym_brightmail_queues: bug fix where WATO configuration did not alter behaviour
* 10105 FIX: oracle_rman: don't crash on intermittent connection loss
* 7720 FIX: oracle_logswitches: Handle db error maybe provided via the agent output
* 10211 FIX: netapp_api_volumes: Fixed scaling of latency values for ALL protocols
* 10348 FIX: mssql_databases: Do not alert if instance is not running
* 10151 FIX: mssql: Sanitize mssql ini file name
NOTE: Please refer to the migration notes!
* 10006 FIX: mk_logwatch: Do not crash upon non-matching optional subgroups and rewrites
* 10154 FIX: mgmt_ipmi_sensors: Missing service details for IPMI sensors services
NOTE: Please refer to the migration notes!
* 10267 FIX: dell_compellent_disks would not see more than 9 disks
* 10102 FIX: cifsmounts: Now displays performance data as check plugin nfsmounts does
* 10358 FIX: check_mail_loop: Fixed exception: Failed to fetch mail NR ('NoneType' object has no attribute '__getitem__')
* 10101 FIX: aws_rds.{bin_log_usage,transaction_logs_usage,replication_slot_usage}: Fixed discovering services
* 10103 FIX: agent_aws: Skip S3 buckets for which the location cannot be retrieved (AccessDenied)
* 10210 FIX: agent_aws: Fixed FilterLimitExceeded while collecting EC2 instance attributes
* 10189 FIX: Windows Agent reports allowed IP addresses correctly
* 10085 FIX: Service discovery page: Do not show long output of services
* 10308 FIX: Recover performance data output for averaged bandwidth use in IF checks
* 8914 FIX: Fix calculation of latency for netapp_api_vs_traffic 2
* 10108 FIX: Fix apt check when switched to "dist-upgrade" and encountering auto removals
* 10094 FIX: Checkmk Discovery: Fixed crash if a host has no data sources configured
* 10091 FIX: Agent AWS: Let EC2 services become stale if the instance was terminated
Plex: Livelier TV grid on Android TV
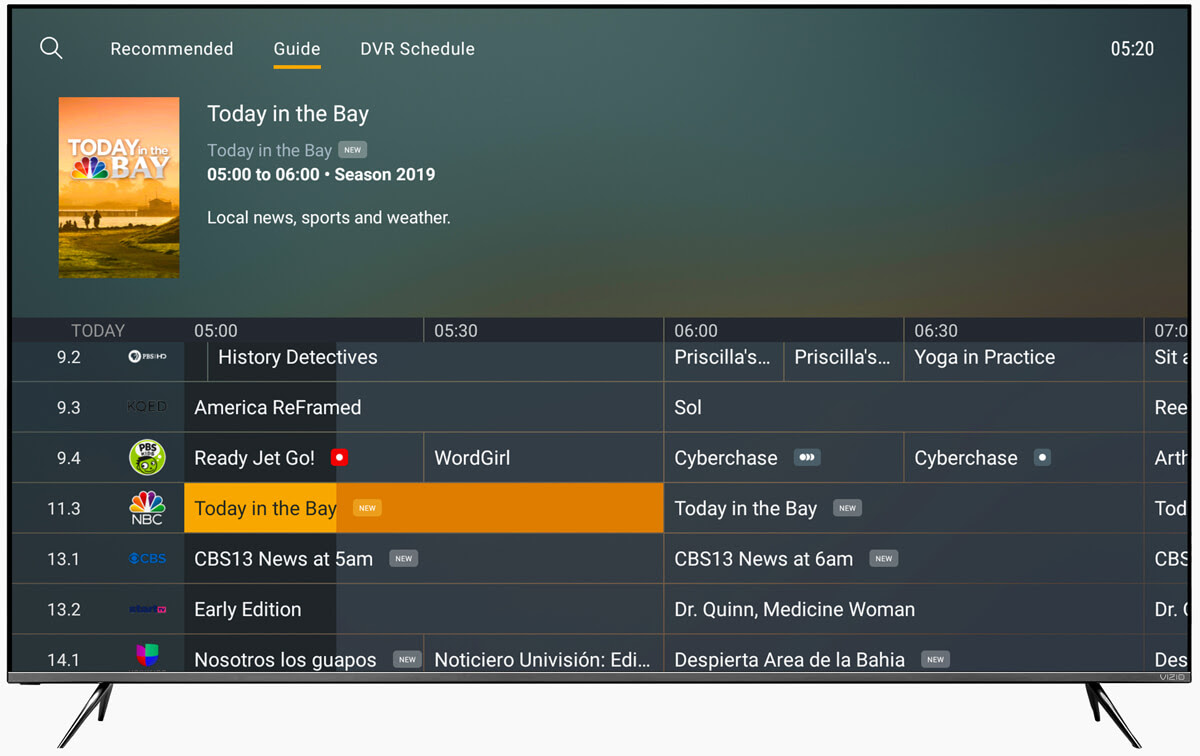 |
Livelier TV grid on Android TV
|
| We’ve leveled up our gridview channel guide on Android TV with a huge performance boost, making it faster and easier than ever to navigate to the programming you want, with even more guide updates in the coming weeks. |
ADMIN: GitLab 12.3 Brings More Security to DevOps Engineers
With the release of version 12.3, GitLab has added a new security focused feature called Web Application Firewall for Kubernetes Ingress.
“In GitLab 12.3 we are shipping our first iteration of a Web Application Firewall built into the GitLab SDLC platform. Its focus is on monitoring and reporting of security concerns related to your Kubernetes clusters,” said GitLab in a press announcement.
REF: http://www.admin-magazine.com/News/GitLab-12.3-Brings-More-Security-to-DevOps-Engineers
Cloudflare WARP as VPN

We’ve made it easy to report issues that you discover. From the 1.1.1.1 App you can click on the little bug icon near the top of the screen, or just shake your phone with the app open, and quickly send us a report. We expect, over the weeks ahead, we’ll be squashing many of the bugs that you report.
REF: https://blog.cloudflare.com/announcing-warp-plus/
TrendLabs: CVE-2019-16928: Exploiting an Exim Vulnerability via EHLO Strings
Figure 1. Memory representation during heap buffer overflow
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/cve-2019-16928-exploiting-an-exim-vulnerability-via-ehlo-strings/
[USN-4147-1] Linux kernel vulnerabilities
---------- Forwarded message ---------
From: Steve Beattie
Date: Oct 5, 2019 1:37AM
It was discovered that the Intel Wi-Fi device driver in the Linux kernel
did not properly validate certain Tunneled Direct Link Setup (TDLS). A
physically proximate attacker could use this to cause a denial of service
(Wi-Fi disconnect). (CVE-2019-0136)
It was discovered that the Bluetooth UART implementation in the Linux
kernel did not properly check for missing tty operations. A local attacker
could use this to cause a denial of service. (CVE-2019-10207)
It was discovered that the GTCO tablet input driver in the Linux kernel did
not properly bounds check the initial HID report sent by the device. A
physically proximate attacker could use this to cause a denial of service
(system crash) or possibly execute arbitrary code. (CVE-2019-13631)
It was discovered that an out-of-bounds read existed in the QLogic QEDI
iSCSI Initiator Driver in the Linux kernel. A local attacker could possibly
use this to expose sensitive information (kernel memory). (CVE-2019-15090)
Hui Peng and Mathias Payer discovered that the USB audio driver for the
Linux kernel did not properly validate device meta data. A physically
proximate attacker could use this to cause a denial of service (system
crash). (CVE-2019-15117)
Hui Peng and Mathias Payer discovered that the USB audio driver for the
Linux kernel improperly performed recursion while handling device meta
data. A physically proximate attacker could use this to cause a denial of
service (system crash). (CVE-2019-15118)
It was discovered that the Raremono AM/FM/SW radio device driver in the
Linux kernel did not properly allocate memory, leading to a use-after-free.
A physically proximate attacker could use this to cause a denial of service
or possibly execute arbitrary code. (CVE-2019-15211)
It was discovered at a double-free error existed in the USB Rio 500 device
driver for the Linux kernel. A physically proximate attacker could use this
to cause a denial of service. (CVE-2019-15212)
It was discovered that a race condition existed in the CPiA2 video4linux
device driver for the Linux kernel, leading to a use-after-free. A
physically proximate attacker could use this to cause a denial of service
(system crash) or possibly execute arbitrary code. (CVE-2019-15215)
It was discovered that a race condition existed in the Softmac USB Prism54
device driver in the Linux kernel. A physically proximate attacker could
use this to cause a denial of service (system crash). (CVE-2019-15220)
Benjamin Moody discovered that the XFS file system in the Linux kernel did
not properly handle an error condition when out of disk quota. A local
attacker could possibly use this to cause a denial of service.
(CVE-2019-15538)
It was discovered that the Hisilicon HNS3 ethernet device driver in the
Linux kernel contained an out of bounds access vulnerability. A local
attacker could use this to possibly cause a denial of service (system
crash). (CVE-2019-15925)
It was discovered that the Atheros mobile chipset driver in the Linux
kernel did not properly validate data in some situations. An attacker could
use this to cause a denial of service (system crash). (CVE-2019-15926)
Daniele Antonioli, Nils Ole Tippenhauer, and Kasper B. Rasmussen discovered
that the Bluetooth protocol BR/EDR specification did not properly require
sufficiently strong encryption key lengths. A physically proximate attacker
could use this to expose sensitive information. (CVE-2019-9506)
It was discovered that ZR364XX Camera USB device driver for the Linux
kernel did not properly initialize memory. A physically proximate attacker
could use this to cause a denial of service (system crash).
(CVE-2019-15217)
It was discovered that the Siano USB MDTV receiver device driver in the
Linux kernel made improper assumptions about the device characteristics. A
physically proximate attacker could use this cause a denial of service
(system crash). (CVE-2019-15218)
It was discovered that the Line 6 POD USB device driver in the Linux kernel
did not properly validate data size information from the device. A
physically proximate attacker could use this to cause a denial of service
(system crash). (CVE-2019-15221)
It was discovered that the Line 6 USB driver for the Linux kernel contained
a race condition when the device was disconnected. A physically proximate
attacker could use this to cause a denial of service (system crash).
(CVE-2019-15223)
References:
https://usn.ubuntu.com/4147-1
CVE-2019-0136, CVE-2019-10207, CVE-2019-13631, CVE-2019-15090,
CVE-2019-15117, CVE-2019-15118, CVE-2019-15211, CVE-2019-15212,
CVE-2019-15215, CVE-2019-15217, CVE-2019-15218, CVE-2019-15220,
CVE-2019-15221, CVE-2019-15223, CVE-2019-15538, CVE-2019-15925,
CVE-2019-15926, CVE-2019-9506
From: Steve Beattie
Date: Oct 5, 2019 1:37AM
It was discovered that the Intel Wi-Fi device driver in the Linux kernel
did not properly validate certain Tunneled Direct Link Setup (TDLS). A
physically proximate attacker could use this to cause a denial of service
(Wi-Fi disconnect). (CVE-2019-0136)
It was discovered that the Bluetooth UART implementation in the Linux
kernel did not properly check for missing tty operations. A local attacker
could use this to cause a denial of service. (CVE-2019-10207)
It was discovered that the GTCO tablet input driver in the Linux kernel did
not properly bounds check the initial HID report sent by the device. A
physically proximate attacker could use this to cause a denial of service
(system crash) or possibly execute arbitrary code. (CVE-2019-13631)
It was discovered that an out-of-bounds read existed in the QLogic QEDI
iSCSI Initiator Driver in the Linux kernel. A local attacker could possibly
use this to expose sensitive information (kernel memory). (CVE-2019-15090)
Hui Peng and Mathias Payer discovered that the USB audio driver for the
Linux kernel did not properly validate device meta data. A physically
proximate attacker could use this to cause a denial of service (system
crash). (CVE-2019-15117)
Hui Peng and Mathias Payer discovered that the USB audio driver for the
Linux kernel improperly performed recursion while handling device meta
data. A physically proximate attacker could use this to cause a denial of
service (system crash). (CVE-2019-15118)
It was discovered that the Raremono AM/FM/SW radio device driver in the
Linux kernel did not properly allocate memory, leading to a use-after-free.
A physically proximate attacker could use this to cause a denial of service
or possibly execute arbitrary code. (CVE-2019-15211)
It was discovered at a double-free error existed in the USB Rio 500 device
driver for the Linux kernel. A physically proximate attacker could use this
to cause a denial of service. (CVE-2019-15212)
It was discovered that a race condition existed in the CPiA2 video4linux
device driver for the Linux kernel, leading to a use-after-free. A
physically proximate attacker could use this to cause a denial of service
(system crash) or possibly execute arbitrary code. (CVE-2019-15215)
It was discovered that a race condition existed in the Softmac USB Prism54
device driver in the Linux kernel. A physically proximate attacker could
use this to cause a denial of service (system crash). (CVE-2019-15220)
Benjamin Moody discovered that the XFS file system in the Linux kernel did
not properly handle an error condition when out of disk quota. A local
attacker could possibly use this to cause a denial of service.
(CVE-2019-15538)
It was discovered that the Hisilicon HNS3 ethernet device driver in the
Linux kernel contained an out of bounds access vulnerability. A local
attacker could use this to possibly cause a denial of service (system
crash). (CVE-2019-15925)
It was discovered that the Atheros mobile chipset driver in the Linux
kernel did not properly validate data in some situations. An attacker could
use this to cause a denial of service (system crash). (CVE-2019-15926)
Daniele Antonioli, Nils Ole Tippenhauer, and Kasper B. Rasmussen discovered
that the Bluetooth protocol BR/EDR specification did not properly require
sufficiently strong encryption key lengths. A physically proximate attacker
could use this to expose sensitive information. (CVE-2019-9506)
It was discovered that ZR364XX Camera USB device driver for the Linux
kernel did not properly initialize memory. A physically proximate attacker
could use this to cause a denial of service (system crash).
(CVE-2019-15217)
It was discovered that the Siano USB MDTV receiver device driver in the
Linux kernel made improper assumptions about the device characteristics. A
physically proximate attacker could use this cause a denial of service
(system crash). (CVE-2019-15218)
It was discovered that the Line 6 POD USB device driver in the Linux kernel
did not properly validate data size information from the device. A
physically proximate attacker could use this to cause a denial of service
(system crash). (CVE-2019-15221)
It was discovered that the Line 6 USB driver for the Linux kernel contained
a race condition when the device was disconnected. A physically proximate
attacker could use this to cause a denial of service (system crash).
(CVE-2019-15223)
References:
https://usn.ubuntu.com/4147-1
CVE-2019-0136, CVE-2019-10207, CVE-2019-13631, CVE-2019-15090,
CVE-2019-15117, CVE-2019-15118, CVE-2019-15211, CVE-2019-15212,
CVE-2019-15215, CVE-2019-15217, CVE-2019-15218, CVE-2019-15220,
CVE-2019-15221, CVE-2019-15223, CVE-2019-15538, CVE-2019-15925,
CVE-2019-15926, CVE-2019-9506
Plex: Next generation transcoding Yep, we just improved hardware transcoding again, giving your CPU a well-deserved break by offloading the work to that generous GPU. Depending on your setup, this means the potential to transcode more concurrent streams with even better performance.
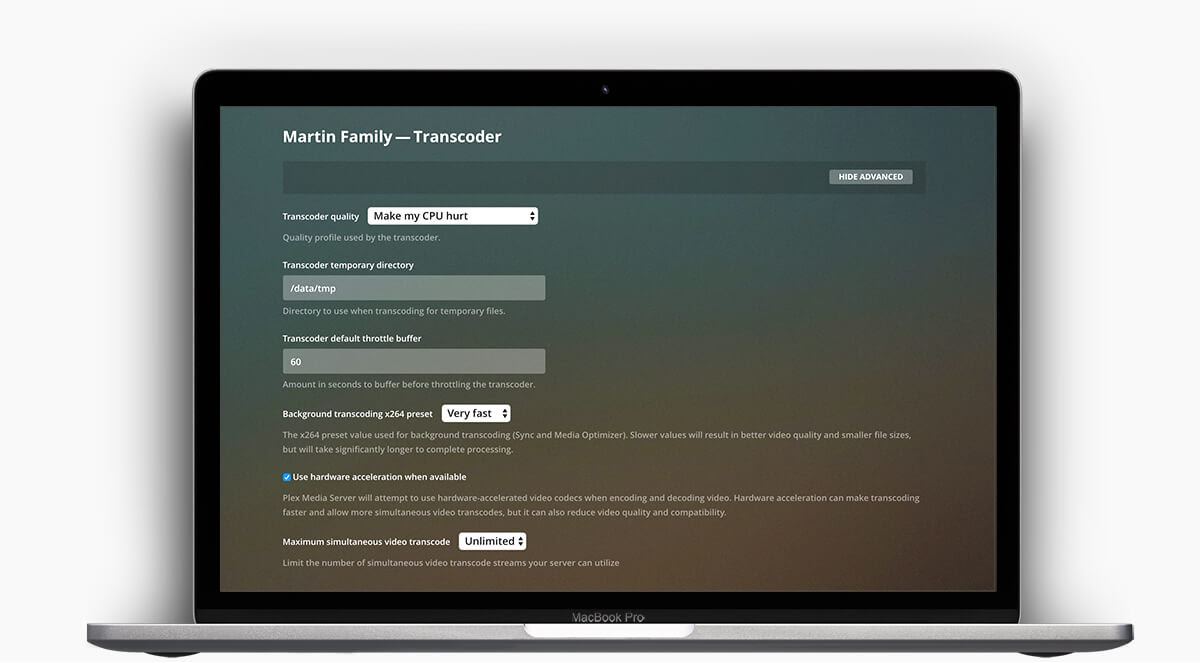 |
| Yep, we just improved hardware transcoding again, giving your CPU a well-deserved break by offloading the work to that generous GPU. Depending on your setup, this means the potential to transcode more concurrent streams with even better performance. |
TrendLabs: Short October Patch Tuesday Includes Remote Desktop Client, Browser, and Authentication Patches
October's Patch Tuesday is relatively modest, with Microsoft releasing a total of 59 patches. However, this shorter list still warrants attention. Nine of the 59 were still identified as Critical, while the remaining 50 were labeled Important. Most of the critical bulletins were for various Internet Explorer and Microsoft Edge vulnerabilities, with one covering a Remote Desktop Client vulnerability. The Important bulletins fixed several issues, including NTLM and Microsoft IIS server vulnerabilities.
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/short-october-patch-tuesday-includes-remote-desktop-client-browser-and-authentication-patches/
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/short-october-patch-tuesday-includes-remote-desktop-client-browser-and-authentication-patches/
2019年11月7日 星期四
MagicSoft Playout ver 7.4.7
MagicSoft Playout ver 7.4.7 adds :
- a new algorithm for calculating the elapsed time of a trimmed clip
- option to replace a playlist entry with a clip having the same name
( right-click on the clip and choose the corresponding entry from menu )
- option to insert clips that will be available at a later time (by inserting list containing the name of the clips)
- a new algorithm for prioritizing the analyze of the selected clip
- a new algorithm for checking the availability of the selected clip
- option to reset the grid columns settings (from program menu, Edit -> Reset Grid Layout)
- option to change the color text and background of the grid (from program menu, Configuration-> Settings -> Colors)
- a new algorithm for extending the functionality of the folder templates to Playlist Editor
REF: https://www.magicsoft.tv/news.html
- a new algorithm for calculating the elapsed time of a trimmed clip
- option to replace a playlist entry with a clip having the same name
( right-click on the clip and choose the corresponding entry from menu )
- option to insert clips that will be available at a later time (by inserting list containing the name of the clips)
- a new algorithm for prioritizing the analyze of the selected clip
- a new algorithm for checking the availability of the selected clip
- option to reset the grid columns settings (from program menu, Edit -> Reset Grid Layout)
- option to change the color text and background of the grid (from program menu, Configuration-> Settings -> Colors)
- a new algorithm for extending the functionality of the folder templates to Playlist Editor
TrendLabs: New Fileless Botnet Novter Distributed by KovCoreG Malvertising Campaign
Tailgate anywhere with Plex
 |
Tailgate anywhere with Plex
|
| The inexplicable glory that is American football is now upon us. Stream games live or record them with Plex Live TV and DVR to watch wherever and whenever you want. |
TrendLabs: Gambling Apps Sneak into Top 100: How Hundreds of Fake Apps Spread on iOS App Store and Google Play
Figure 2. Original webpage (left) and its English translation (right)
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/gambling-apps-sneak-top-100-hundreds-fake-apps-spread-app-store-google-play/
[USN-4146-1] ClamAV vulnerabilities
---------- Forwarded message ---------
From: Marc Deslauriers
Date: Oct 2, 2019 8:05PM
It was discovered that ClamAV incorrectly handled unpacking ZIP files. A
remote attacker could possibly use this issue to cause ClamAV to crash,
resulting in a denial of service. (CVE-2019-12625)
It was discovered that ClamAV incorrectly handled unpacking bzip2 files. A
remote attacker could use this issue to cause ClamAV to crash, resulting in
a denial of service, or possibly execute arbitrary code. (CVE-2019-12900)
References:
https://usn.ubuntu.com/4146-1
CVE-2019-12625, CVE-2019-12900
From: Marc Deslauriers
Date: Oct 2, 2019 8:05PM
It was discovered that ClamAV incorrectly handled unpacking ZIP files. A
remote attacker could possibly use this issue to cause ClamAV to crash,
resulting in a denial of service. (CVE-2019-12625)
It was discovered that ClamAV incorrectly handled unpacking bzip2 files. A
remote attacker could use this issue to cause ClamAV to crash, resulting in
a denial of service, or possibly execute arbitrary code. (CVE-2019-12900)
References:
https://usn.ubuntu.com/4146-1
CVE-2019-12625, CVE-2019-12900
Cloudflare Workers Sites:
Two years ago for Birthday Week, we announced Cloudflare Workers, a way for developers to write and run JavaScript and WebAssembly on our network in 194 cities around the world. A year later, we released Workers KV, our distributed key-value store that gave developers the ability to store state at the edge in those same cities.
REF:
TrendLabs: Mac Malware that Spoofs Trading App Steals User Information, Uploads it to Website
Figure 1. The suspicious shell script which was flagged by our system
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/mac-malware-that-spoofs-trading-app-steals-user-information-uploads-it-to-website/
2019年10月31日 星期四
[openssh-unix-announce] Announce: OpenSSH 8.1 released
---------- Forwarded message ---------
From: Damien Miller
Date: Oct 9, 2019 11:44AM
Security
========
* ssh(1), sshd(8), ssh-add(1), ssh-keygen(1): an exploitable integer
overflow bug was found in the private key parsing code for the XMSS
key type. This key type is still experimental and support for it is
not compiled by default. No user-facing autoconf option exists in
portable OpenSSH to enable it. This bug was found by Adam Zabrocki
and reported via SecuriTeam's SSD program.
* ssh(1), sshd(8), ssh-agent(1): add protection for private keys at
rest in RAM against speculation and memory side-channel attacks like
Spectre, Meltdown and Rambleed. This release encrypts private keys
when they are not in use with a symmetric key that is derived from a
relatively large "prekey" consisting of random data (currently 16KB).
Potentially-incompatible changes
================================
This release includes a number of changes that may affect existing
configurations:
* ssh-keygen(1): when acting as a CA and signing certificates with
an RSA key, default to using the rsa-sha2-512 signature algorithm.
Certificates signed by RSA keys will therefore be incompatible
with OpenSSH versions prior to 7.2 unless the default is
overridden (using "ssh-keygen -t ssh-rsa -s ...").
Changes since OpenSSH 8.0
=========================
This release is focused on bug-fixing.
From: Damien Miller
Date: Oct 9, 2019 11:44AM
Security
========
* ssh(1), sshd(8), ssh-add(1), ssh-keygen(1): an exploitable integer
overflow bug was found in the private key parsing code for the XMSS
key type. This key type is still experimental and support for it is
not compiled by default. No user-facing autoconf option exists in
portable OpenSSH to enable it. This bug was found by Adam Zabrocki
and reported via SecuriTeam's SSD program.
* ssh(1), sshd(8), ssh-agent(1): add protection for private keys at
rest in RAM against speculation and memory side-channel attacks like
Spectre, Meltdown and Rambleed. This release encrypts private keys
when they are not in use with a symmetric key that is derived from a
relatively large "prekey" consisting of random data (currently 16KB).
Potentially-incompatible changes
================================
This release includes a number of changes that may affect existing
configurations:
* ssh-keygen(1): when acting as a CA and signing certificates with
an RSA key, default to using the rsa-sha2-512 signature algorithm.
Certificates signed by RSA keys will therefore be incompatible
with OpenSSH versions prior to 7.2 unless the default is
overridden (using "ssh-keygen -t ssh-rsa -s ...").
Changes since OpenSSH 8.0
=========================
This release is focused on bug-fixing.
Linux on the mainframe: Then and now

LinuxONE Emperor III mainframe | Used with permission, Copyright IBM
Blackmagic: ATEM Mini for low cost multi camera live production
| |
The new ATEM Mini makes it easy to create professional multi camera productions for live streaming to YouTube or innovative business presentations using Skype.
|
[USN-4162-1] Linux kernel vulnerabilities
---------- Forwarded message ---------
It was discovered that the RSI 91x Wi-Fi driver in the Linux kernel did not
did not handle detach operations correctly, leading to a use-after-free
vulnerability. A physically proximate attacker could use this to cause a
denial of service (system crash) or possibly execute arbitrary code.
(CVE-2018-21008)
Wen Huang discovered that the Marvell Wi-Fi device driver in the Linux
kernel did not properly perform bounds checking, leading to a heap
overflow. A local attacker could use this to cause a denial of service
(system crash) or possibly execute arbitrary code. (CVE-2019-14814,
CVE-2019-14815, CVE-2019-14816)
Matt Delco discovered that the KVM hypervisor implementation in the Linux
kernel did not properly perform bounds checking when handling coalesced
MMIO write operations. A local attacker with write access to /dev/kvm could
use this to cause a denial of service (system crash). (CVE-2019-14821)
Hui Peng and Mathias Payer discovered that the USB audio driver for the
Linux kernel did not properly validate device meta data. A physically
proximate attacker could use this to cause a denial of service (system
crash). (CVE-2019-15117)
Hui Peng and Mathias Payer discovered that the USB audio driver for the
Linux kernel improperly performed recursion while handling device meta
data. A physically proximate attacker could use this to cause a denial of
service (system crash). (CVE-2019-15118)
It was discovered that the Technisat DVB-S/S2 USB device driver in the
Linux kernel contained a buffer overread. A physically proximate attacker
could use this to cause a denial of service (system crash) or possibly
expose sensitive information. (CVE-2019-15505)
Brad Spengler discovered that a Spectre mitigation was improperly
implemented in the ptrace susbsystem of the Linux kernel. A local attacker
could possibly use this to expose sensitive information. (CVE-2019-15902)
It was discovered that the SMB networking file system implementation in the
Linux kernel contained a buffer overread. An attacker could use this to
expose sensitive information (kernel memory). (CVE-2019-15918)
References:
https://usn.ubuntu.com/4162-1
CVE-2018-21008, CVE-2019-14814, CVE-2019-14815, CVE-2019-14816,
CVE-2019-14821, CVE-2019-15117, CVE-2019-15118, CVE-2019-15505,
CVE-2019-15902, CVE-2019-15918
From: Seth Arnold
Date: Oct 22, 2019 11:14AM
Date: Oct 22, 2019 11:14AM
It was discovered that the RSI 91x Wi-Fi driver in the Linux kernel did not
did not handle detach operations correctly, leading to a use-after-free
vulnerability. A physically proximate attacker could use this to cause a
denial of service (system crash) or possibly execute arbitrary code.
(CVE-2018-21008)
Wen Huang discovered that the Marvell Wi-Fi device driver in the Linux
kernel did not properly perform bounds checking, leading to a heap
overflow. A local attacker could use this to cause a denial of service
(system crash) or possibly execute arbitrary code. (CVE-2019-14814,
CVE-2019-14815, CVE-2019-14816)
Matt Delco discovered that the KVM hypervisor implementation in the Linux
kernel did not properly perform bounds checking when handling coalesced
MMIO write operations. A local attacker with write access to /dev/kvm could
use this to cause a denial of service (system crash). (CVE-2019-14821)
Hui Peng and Mathias Payer discovered that the USB audio driver for the
Linux kernel did not properly validate device meta data. A physically
proximate attacker could use this to cause a denial of service (system
crash). (CVE-2019-15117)
Hui Peng and Mathias Payer discovered that the USB audio driver for the
Linux kernel improperly performed recursion while handling device meta
data. A physically proximate attacker could use this to cause a denial of
service (system crash). (CVE-2019-15118)
It was discovered that the Technisat DVB-S/S2 USB device driver in the
Linux kernel contained a buffer overread. A physically proximate attacker
could use this to cause a denial of service (system crash) or possibly
expose sensitive information. (CVE-2019-15505)
Brad Spengler discovered that a Spectre mitigation was improperly
implemented in the ptrace susbsystem of the Linux kernel. A local attacker
could possibly use this to expose sensitive information. (CVE-2019-15902)
It was discovered that the SMB networking file system implementation in the
Linux kernel contained a buffer overread. An attacker could use this to
expose sensitive information (kernel memory). (CVE-2019-15918)
References:
https://usn.ubuntu.com/4162-1
CVE-2018-21008, CVE-2019-14814, CVE-2019-14815, CVE-2019-14816,
CVE-2019-14821, CVE-2019-15117, CVE-2019-15118, CVE-2019-15505,
CVE-2019-15902, CVE-2019-15918
LM: FOG imaging server to image and rollout several installations
TrendLabs: Fileless Cryptocurrency-Miner GhostMiner Weaponizes WMI Objects, Kills Other Cryptocurrency-Mining Payloads
Figure 1. List of service names that WMI_Killer terminates and deletes
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/fileless-cryptocurrency-miner-ghostminer-weaponizes-wmi-objects-kills-other-cryptocurrency-mining-payloads/
訂閱:
意見 (Atom)