- Managing Asset Information - Keeping up with your changing environment
- Finding Vulnerabilities - Continuous assessment of system weaknesses
- Detecting Threats - Catching and identifying attacks
- Monitoring for Suspicious Behavior - Spotting and investigating the unexpected
- Utilizing SIEM Event Correlation - Analyzing threats efficiently
2018年8月31日 星期五
AlienVault: 5 Security Controls for an Effective Security Operations Center (SOC)
2018年8月30日 星期四
TrendLabs: The Urpage Connection to Bahamut, Confucius and Patchwork
Figure 1. Original (top) and modified (bottom) website
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/the-urpage-connection-to-bahamut-confucius-and-patchwork/
2018年8月29日 星期三
[LSN-0042-1] Linux kernel vulnerability
---------- Forwarded message ----------
From:
Date: 2018-08-15 2:46 GMT+08:00
Summary:
On August 14, fixes for CVE-2018-3620 and CVE-2018-3646 were released into the
Ubuntu Xenial and Bionic kernels. These CVEs are security vulnerabilities
caused by flaws in the design of speculative execution hardware in the
computer's CPU. Researchers discovered that memory present in the L1 data
cache of an Intel CPU core may be visible to other processes running on the
same core.
Details on the vulnerability and our response can be found here:
https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/L1TF
Due to the high complexity of the fixes and the need for a corresponding
CPU microcode update for a complete fix, we are unable to livepatch these
CVEs. Please plan to reboot into an updated kernel as soon as possible.
References:
CVE-2018-3620, and CVE-2018-3646
From:
Date: 2018-08-15 2:46 GMT+08:00
Summary:
On August 14, fixes for CVE-2018-3620 and CVE-2018-3646 were released into the
Ubuntu Xenial and Bionic kernels. These CVEs are security vulnerabilities
caused by flaws in the design of speculative execution hardware in the
computer's CPU. Researchers discovered that memory present in the L1 data
cache of an Intel CPU core may be visible to other processes running on the
same core.
Details on the vulnerability and our response can be found here:
https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/L1TF
Due to the high complexity of the fixes and the need for a corresponding
CPU microcode update for a complete fix, we are unable to livepatch these
CVEs. Please plan to reboot into an updated kernel as soon as possible.
References:
CVE-2018-3620, and CVE-2018-3646
2018年8月28日 星期二
Plex: Hands-free music experience
| Get your music in Plex and enjoy a hands-free music experience with Alexa. Listen to your entire collection, play your own radio stations, and do it without lifting a finger. Whether you want to play a legendary album or a mix from an artist you just love, Plex makes it easy. And, with Amazon Music Storage shutting down in the near future, Plex is the easiest way to have access to your whole library of tunes. |
2018年8月27日 星期一
OpenSSH 7.8 released
---------- Forwarded message ---------
From: Damien Miller
Date: 2018年8月24日 週五 下午3:40
Potentially-incompatible changes
================================
This release includes a number of changes that may affect existing
configurations:
Changes since OpenSSH 7.7
=========================
This is primarily a bugfix release.
Reporting Bugs:
===============
- Please read http://www.openssh.com/report.html
From: Damien Miller
Date: 2018年8月24日 週五 下午3:40
Potentially-incompatible changes
================================
This release includes a number of changes that may affect existing
configurations:
Changes since OpenSSH 7.7
=========================
This is primarily a bugfix release.
Reporting Bugs:
===============
- Please read http://www.openssh.com/report.html
2018年8月26日 星期日
TrendLabs: IQY and PowerShell Abused by Spam Campaign to Infect Users in Japan with BEBLOH and URSNIF
Figure 1. Volume of spam mails detected from August 6-10, 2018
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/iqy-and-powershell-abused-by-spam-campaign-to-infect-users-in-japan-with-bebloh-and-ursnif/
2018年8月25日 星期六
Zero Trust Network / Model
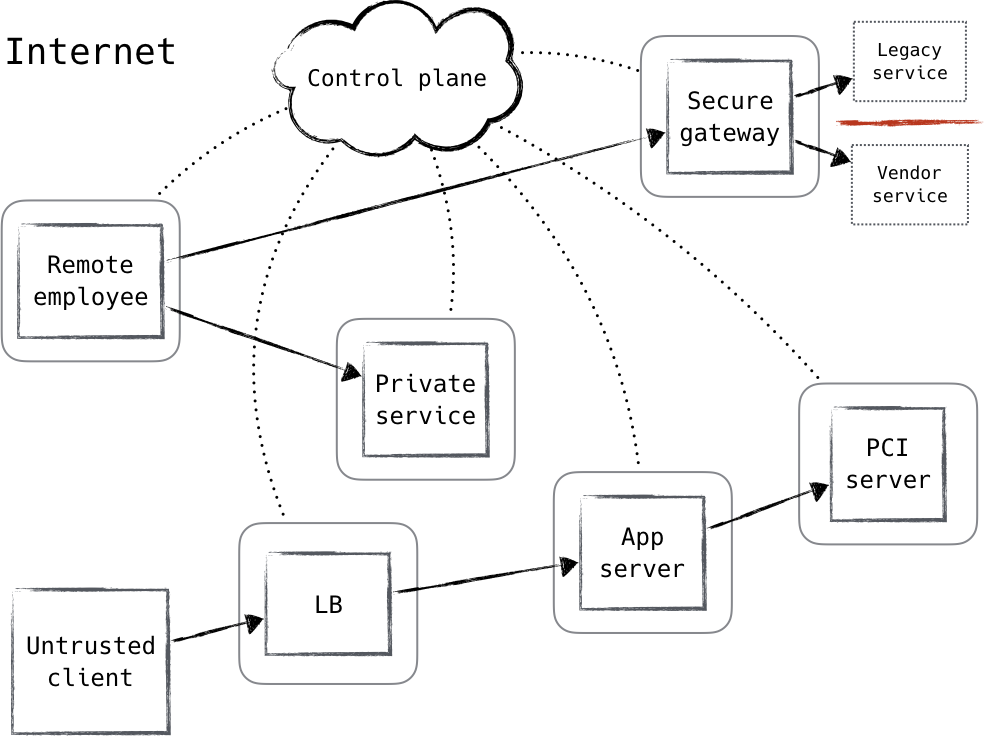
REF: https://www.safaribooksonline.com/library/view/zero-trust-networks/9781491962183/ch01.html
2018年8月23日 星期四
[LSN-0041-1] Linux kernel vulnerability
---------- Forwarded message ----------
From:
Date: 2018-08-10 19:32 GMT+08:00
Details:
The sr_do_ioctl function in drivers/scsi/sr_ioctl.c in the Linux kernel
through 4.16.12 allows local users to cause a denial of service
(stack-based buffer overflow) or possibly have unspecified other impact
because sense buffers have different sizes at the CDROM layer and the SCSI
layer, as demonstrated by a CDROMREADMODE2 ioctl call. (CVE-2018-11506)
Wen Xu discovered that the ext4 file system implementation in the Linux
kernel did not properly initialize the crc32c checksum driver. A local
attacker could use this to cause a denial of service (system crash).
(CVE-2018-1094)
The inode_init_owner function in fs/inode.c in the Linux kernel through
4.17.4 allows local users to create files with an unintended group ownership,
in a scenario where a directory is SGID to a certain group and is writable
by a user who is not a member of that group. Here, the non-member can trigger
creation of a plain file whose group ownership is that group. The intended
behavior was that the non-member can trigger creation of a directory
(but not a plain file) whose group ownership is that group. The non-member
can escalate privileges by making the plain file executable and SGID.
(CVE-2018-13405)
An issue was discovered in fs/xfs/libxfs/xfs_attr_leaf.c in the Linux kernel
through 4.17.3. An OOPS may occur for a corrupted xfs image after
xfs_da_shrink_inode() is called with a NULL bp. (CVE-2018-13094)
Juha-Matti Tilli discovered that the TCP implementation in the Linux kernel
performed algorithmically expensive operations in some situations when
handling incoming packets. A remote attacker could use this to cause a
denial of service. (CVE-2018-5390)
References:
CVE-2018-11506, CVE-2018-1094, CVE-2018-13405, CVE-2018-13094,
CVE-2018-5390
Date: 2018-08-10 19:32 GMT+08:00
Details:
The sr_do_ioctl function in drivers/scsi/sr_ioctl.c in the Linux kernel
through 4.16.12 allows local users to cause a denial of service
(stack-based buffer overflow) or possibly have unspecified other impact
because sense buffers have different sizes at the CDROM layer and the SCSI
layer, as demonstrated by a CDROMREADMODE2 ioctl call. (CVE-2018-11506)
Wen Xu discovered that the ext4 file system implementation in the Linux
kernel did not properly initialize the crc32c checksum driver. A local
attacker could use this to cause a denial of service (system crash).
(CVE-2018-1094)
The inode_init_owner function in fs/inode.c in the Linux kernel through
4.17.4 allows local users to create files with an unintended group ownership,
in a scenario where a directory is SGID to a certain group and is writable
by a user who is not a member of that group. Here, the non-member can trigger
creation of a plain file whose group ownership is that group. The intended
behavior was that the non-member can trigger creation of a directory
(but not a plain file) whose group ownership is that group. The non-member
can escalate privileges by making the plain file executable and SGID.
(CVE-2018-13405)
An issue was discovered in fs/xfs/libxfs/xfs_attr_leaf.c in the Linux kernel
through 4.17.3. An OOPS may occur for a corrupted xfs image after
xfs_da_shrink_inode() is called with a NULL bp. (CVE-2018-13094)
Juha-Matti Tilli discovered that the TCP implementation in the Linux kernel
performed algorithmically expensive operations in some situations when
handling incoming packets. A remote attacker could use this to cause a
denial of service. (CVE-2018-5390)
References:
CVE-2018-11506, CVE-2018-1094, CVE-2018-13405, CVE-2018-13094,
CVE-2018-5390
2018年8月22日 星期三
TrendLabs: Supply Chain Attack Operation Red Signature Targets South Korean Organizations
2018年8月21日 星期二
[USN-3738-1] Samba vulnerabilities
---------- Forwarded message ----------
From: Marc Deslauriers
Date: 2018-08-15 1:48 GMT+08:00
Svyatoslav Phirsov discovered that the Samba libsmbclient library
incorrectly handled extra long filenames. A malicious server could use this
issue to cause Samba to crash, resulting in a denial of service, or
possibly execute arbitrary code. (CVE-2018-10858)
Volker Mauel discovered that Samba incorrectly handled database output.
When used as an Active Directory Domain Controller, a remote authenticated
attacker could use this issue to cause Samba to crash, resulting in a
denial of service. This issue only affected Ubuntu 18.04 LTS.
(CVE-2018-10918)
Phillip Kuhrt discovered that the Samba LDAP server incorrectly handled
certain confidential attribute values. A remote authenticated attacker
could possibly use this issue to obtain certain sensitive information.
(CVE-2018-10919)
Vivek Das discovered that Samba incorrectly handled NTLMv1 being explicitly
disabled on the server. A remote user could possibly be authenticated using
NTLMv1, contrary to expectations. This issue only affected Ubuntu 18.04
LTS. (CVE-2018-1139)
References:
https://usn.ubuntu.com/usn/usn-3738-1
CVE-2018-10858, CVE-2018-10918, CVE-2018-10919, CVE-2018-1139
From: Marc Deslauriers
Date: 2018-08-15 1:48 GMT+08:00
Svyatoslav Phirsov discovered that the Samba libsmbclient library
incorrectly handled extra long filenames. A malicious server could use this
issue to cause Samba to crash, resulting in a denial of service, or
possibly execute arbitrary code. (CVE-2018-10858)
Volker Mauel discovered that Samba incorrectly handled database output.
When used as an Active Directory Domain Controller, a remote authenticated
attacker could use this issue to cause Samba to crash, resulting in a
denial of service. This issue only affected Ubuntu 18.04 LTS.
(CVE-2018-10918)
Phillip Kuhrt discovered that the Samba LDAP server incorrectly handled
certain confidential attribute values. A remote authenticated attacker
could possibly use this issue to obtain certain sensitive information.
(CVE-2018-10919)
Vivek Das discovered that Samba incorrectly handled NTLMv1 being explicitly
disabled on the server. A remote user could possibly be authenticated using
NTLMv1, contrary to expectations. This issue only affected Ubuntu 18.04
LTS. (CVE-2018-1139)
References:
https://usn.ubuntu.com/usn/usn-3738-1
CVE-2018-10858, CVE-2018-10918, CVE-2018-10919, CVE-2018-1139
2018年8月20日 星期一
2018年8月19日 星期日
[USN-3734-1] OpenJDK 8 vulnerability
---------- Forwarded message ----------
From: Steve Beattie
Date: 2018-08-10 10:12 GMT+08:00
Summary:
Java applications could be made to use excessive memory.
Details:
It was discovered that the PatternSyntaxException class in OpenJDK
did not properly validate arguments passed to it. An attacker could
use this to possibly construct a class that caused a denial of service
(excessive memory consumption).
References:
https://usn.ubuntu.com/usn/
CVE-2018-2952
Date: 2018-08-10 10:12 GMT+08:00
Summary:
Java applications could be made to use excessive memory.
Details:
It was discovered that the PatternSyntaxException class in OpenJDK
did not properly validate arguments passed to it. An attacker could
use this to possibly construct a class that caused a denial of service
(excessive memory consumption).
References:
https://usn.ubuntu.com/usn/
CVE-2018-2952
2018年8月18日 星期六
TrendLabs: New Underminer Exploit Kit Delivers Bootkit and Cryptocurrency-mining Malware with Encrypted TCP Tunnel
Figure 1. Country distribution of Underminer’s activities, from July 17 to July 23
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/new-underminer-exploit-kit-delivers-bootkit-and-cryptocurrency-mining-malware-with-encrypted-tcp-tunnel/
2018年8月17日 星期五
[USN-3730-1] LXC vulnerability
---------- Forwarded message ----------
From: Marc Deslauriers
Date: 2018-08-07 0:46 GMT+08:00
Summary:
LXC would allow unintended access to files.
Details:
Matthias Gerstner discovered that LXC incorrectly handled the lxc-user-nic
utility. A local attacker could possibly use this issue to open arbitrary
files.
References:
https://usn.ubuntu.com/usn/
CVE-2018-6556
Date: 2018-08-07 0:46 GMT+08:00
Summary:
LXC would allow unintended access to files.
Details:
Matthias Gerstner discovered that LXC incorrectly handled the lxc-user-nic
utility. A local attacker could possibly use this issue to open arbitrary
files.
References:
https://usn.ubuntu.com/usn/
CVE-2018-6556
2018年8月16日 星期四
TrendLabs: Use-after-free (UAF) Vulnerability CVE-2018-8373 in VBScript Engine Affects Internet Explorer to Run Shellcode
Figure 4. IE vulnerability PoC
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/use-after-free-uaf-vulnerability-cve-2018-8373-in-vbscript-engine-affects-internet-explorer-to-run-shellcode/
2018年8月15日 星期三
[Check_mk Announce] New Check_MK stable release 1.5.0p2
---------- Forwarded message ---------
From: Check_mk Announcements
Date: Wed, Aug 15, 2018 at 4:46 AM
WATO:
* 6450 FIX: Fixed handling of "SNMP" and "Dual Check_MK Agent + SNMP" tags when migrating from <1 .5="" p="">* 6446 FIX: Fixed changing agent type from "No agent" to agent in some cases
User interface:
* 6449 SEC: Fixed stored XSS using custom host / user attributes
* 6448 FIX: Fixed displaying tag aliases in rule lists for builtin tags
Core & setup:
* 6447 FIX: Agent type: Fixed not working "use all enabled datasource programs" option
Checks & agents:
* 6460 FIX: jolokia_generic: Do not crash when non-numeric data is supplied for number or rate type values
* 6313 FIX: esx_vsphere_hostsystem: Fixed discovery of multipaths
* 6211 FIX: cisco_secure: Handle unknown 'enabled' state
You can download Check_MK from our download page:
* http://mathias-kettner.de/check_mk_download.html
From: Check_mk Announcements
Date: Wed, Aug 15, 2018 at 4:46 AM
WATO:
* 6450 FIX: Fixed handling of "SNMP" and "Dual Check_MK Agent + SNMP" tags when migrating from <1 .5="" p="">* 6446 FIX: Fixed changing agent type from "No agent" to agent in some cases
User interface:
* 6449 SEC: Fixed stored XSS using custom host / user attributes
* 6448 FIX: Fixed displaying tag aliases in rule lists for builtin tags
Core & setup:
* 6447 FIX: Agent type: Fixed not working "use all enabled datasource programs" option
Checks & agents:
* 6460 FIX: jolokia_generic: Do not crash when non-numeric data is supplied for number or rate type values
* 6313 FIX: esx_vsphere_hostsystem: Fixed discovery of multipaths
* 6211 FIX: cisco_secure: Handle unknown 'enabled' state
You can download Check_MK from our download page:
* http://mathias-kettner.de/check_mk_download.html
2018年8月14日 星期二
Top 10 Networking Features in Windows Server 2019: #8 A Faster, Safer Internet
2018年8月13日 星期一
New Check_MK stable release 1.4.0p35
---------- Forwarded message ---------
From: Check_mk Announcements
Date: Wed, Aug 8, 2018 at 3:47 PM
WATO:
* 6346 FIX: Fixed failed host rename when host is configured as parent on folder level
User interface:
* 6235 FIX: check_mk-if.php: fixed errors arising with php7.1
* 6424 FIX: LDAP: Only set SSL/TLS specific options when SSL is enabled (Fix 1.4.0p34 regression)
* 6423 FIX: Fixed possible XSS in views with some filters
* 6421 FIX: Fixed interpretation of script tags when displaying werk texts
* 6363 FIX: Fixed "host_inventory" exception when using "Has inventory data" filter
* 6326 FIX: Fix "event_host_in_downtime" exception when connecting 1.5 master with 1.4 slave
Notifications:
* 6119 FIX: asciimail, mail: display the custom host and service notes URL correctly in notifications
Core & setup:
* 6340 FIX: Fixed debian agent package incompatibilities (1.4.0p34 regression)
* 6373 FIX: Fixed UnicodeEncodeError when piping "cmk -M" to stream or file
Checks & agents:
* 5739 mbg_lantime_ng_refclock.gps: support for more substates
* 6309 FIX: winperf: Set default levels to 90, 95 percent
* 6300 FIX: win_printers: Added line break to section header; otherwise the output format was broken in case of a Get-WMIObject failure
* 6126 FIX: use correct metric with a better visible colour for averaged CPU utilization
* 6127 FIX: ucd.include: Astaro and Synology are Linux but should use hr_mem
NOTE: Please refer to the migration notes!
* 6148 FIX: solaris_fmadm: Some 'fmadm' versions provide a different output format. This may lead to empty service details if the agent reports any problems
* 6142 FIX: qnap_disks: Fixed undetected error if SMART information is missing
* 6308 FIX: mssql_counters.locks: Fixed wrong state marker
* 4625 FIX: mk_oracle: Fixed configuration for remote instances in bakery
* 6299 FIX: mk_logwatch: logwatch.d files were only loaded if logwatch.cfg was in place
* 6124 FIX: juniper_bgp_state: avoid crash if peer state or peer status is missing in SNMP walk
* 6132 FIX: ipmi_sensors.include: Treat states 'S0G0' (System full operational, working) and 'System Restart' as 'OK'
* 6301 FIX: if_fortigate: Related graphs look like all other interface graphs
* 6307 FIX: hyperv_checkpoints: Parameters did not correctly apply
* 6312 FIX: filesystem: Fixed blemish in discovery dialog: Invalid check parameter: Undefined key 'patterns' in the dictionary
* 6317 FIX: fileinfo, fileinfo.groups: Prevent crash of all fileinfo services if one line fails
* 6383 FIX: db2_bp_hitratios: Fixed conversion to float if any value contains a comma instead of a dot
* 6120 FIX: cisco_nexus_cpu: use the ruleset "CPU utilization for simple devices"
NOTE: Please refer to the migration notes!
* 6306 FIX: check_mk_agent.aix: Prevent timeout of Check_MK service if LPARs of a PowerHA are hanging
You can download Check_MK from our download page:
* http://mathias-kettner.de/check_mk_download.html
From: Check_mk Announcements
Date: Wed, Aug 8, 2018 at 3:47 PM
WATO:
* 6346 FIX: Fixed failed host rename when host is configured as parent on folder level
User interface:
* 6235 FIX: check_mk-if.php: fixed errors arising with php7.1
* 6424 FIX: LDAP: Only set SSL/TLS specific options when SSL is enabled (Fix 1.4.0p34 regression)
* 6423 FIX: Fixed possible XSS in views with some filters
* 6421 FIX: Fixed interpretation of script tags when displaying werk texts
* 6363 FIX: Fixed "host_inventory" exception when using "Has inventory data" filter
* 6326 FIX: Fix "event_host_in_downtime" exception when connecting 1.5 master with 1.4 slave
Notifications:
* 6119 FIX: asciimail, mail: display the custom host and service notes URL correctly in notifications
Core & setup:
* 6340 FIX: Fixed debian agent package incompatibilities (1.4.0p34 regression)
* 6373 FIX: Fixed UnicodeEncodeError when piping "cmk -M" to stream or file
Checks & agents:
* 5739 mbg_lantime_ng_refclock.gps: support for more substates
* 6309 FIX: winperf: Set default levels to 90, 95 percent
* 6300 FIX: win_printers: Added line break to section header; otherwise the output format was broken in case of a Get-WMIObject failure
* 6126 FIX: use correct metric with a better visible colour for averaged CPU utilization
* 6127 FIX: ucd.include: Astaro and Synology are Linux but should use hr_mem
NOTE: Please refer to the migration notes!
* 6148 FIX: solaris_fmadm: Some 'fmadm' versions provide a different output format. This may lead to empty service details if the agent reports any problems
* 6142 FIX: qnap_disks: Fixed undetected error if SMART information is missing
* 6308 FIX: mssql_counters.locks: Fixed wrong state marker
* 4625 FIX: mk_oracle: Fixed configuration for remote instances in bakery
* 6299 FIX: mk_logwatch: logwatch.d files were only loaded if logwatch.cfg was in place
* 6124 FIX: juniper_bgp_state: avoid crash if peer state or peer status is missing in SNMP walk
* 6132 FIX: ipmi_sensors.include: Treat states 'S0G0' (System full operational, working) and 'System Restart' as 'OK'
* 6301 FIX: if_fortigate: Related graphs look like all other interface graphs
* 6307 FIX: hyperv_checkpoints: Parameters did not correctly apply
* 6312 FIX: filesystem: Fixed blemish in discovery dialog: Invalid check parameter: Undefined key 'patterns' in the dictionary
* 6317 FIX: fileinfo, fileinfo.groups: Prevent crash of all fileinfo services if one line fails
* 6383 FIX: db2_bp_hitratios: Fixed conversion to float if any value contains a comma instead of a dot
* 6120 FIX: cisco_nexus_cpu: use the ruleset "CPU utilization for simple devices"
NOTE: Please refer to the migration notes!
* 6306 FIX: check_mk_agent.aix: Prevent timeout of Check_MK service if LPARs of a PowerHA are hanging
You can download Check_MK from our download page:
* http://mathias-kettner.de/check_mk_download.html
2018年8月12日 星期日
TrendLabs:Ransomware as a Service Princess Evolution Looking for Affiliates
2018年8月11日 星期六
[Check_mk Announce] New Check_MK stable release 1.5.0p1
---------- Forwarded message ---------
Changes in all Check_MK Editions:
WATO:
* 6247 FIX: The WATO edit folder page is no longer broken, when the tag group criticality gets deleted
* 6422 FIX: Prevent non-admin users from managing custom host/user attributes
* 6425 FIX: Improved validation of timeperiods before deletion
* 6439 FIX: Fixed upload of some icon files
* 6431 FIX: Fixed bulk discovery (addition to #6377 in 1.5.0)
* 6440 FIX: Backup: Deleting a backup job now deletes the state file
User interface:
* 6433 FIX: Raw edition: Fixed interface graphs when no warn/crit/bandwidth is reported
* 6432 FIX: Raw Edition: Fixed possible broken graphs related to lower/upper parameters
* 6436 FIX: Prevent metrics with "," in their names from breaking graphs
* 5918 FIX: New Theme: Fixed several bugs
* 6424 FIX: LDAP: Only set SSL/TLS specific options when SSL is enabled
* 6423 FIX: Fixed possible XSS in views with some filters
* 6421 FIX: Fixed interpretation of script tags when displaying werk texts
* 6441 FIX: Fixed broken bulk host import with discovery (Regression in 1.5.0)
* 6434 FIX: Background jobs: Not stoppable jobs ignore SIGTERM now
Site management:
* 6435 FIX: omd stop on all processes of a site terminates remaining site processes
* 6443 FIX: Fixed possible "omd backup" error when files vanish during backup
* 6396 FIX: Fixed 'Unhandled exception 452' in master control snapin if EC Daemon was disabled via 'omd config'
Notifications:
* 6399 FIX: Avoid failed notifications in case of crash dumps
Event console:
* 6427 FIX: Raw Edition: Fixed broken Event Console rule editing (1.5 regression)
* 6438 FIX: Fixed canceling of events when positive and cancel messages both match
* 6428 FIX: Fixed broken positive matching on syslog priority
* 6429 FIX: Fixed broken cancel event based on priority
Core & setup:
* 6372 FIX: Check_MK service: Piggyback data source reports the source hosts now
Checks & agents:
* 6420 agent_3par: Certificate verification can now be enabled/disabled
* 6127 FIX: ucd.include: Astaro and Synology are Linux but should use hr_mem
NOTE: Please refer to the migration notes!
* 6391 FIX: multipath: Fixed unrecognized paths which include a dot
* 6395 FIX: mk_cups_queues: Fixed discovery of several printers
* 6442 FIX: huawei_osn_if: Fixed broken check (check_if_common is not defined)
* 6393 FIX: check_bi_aggr: Fixed link in 'Open this aggregation' in the dropdown menu of the aggregation service
* 6444 FIX: brocade_mlx.module_mem: Fixed broken discovery function (KeyError: state)
* 6419 FIX: agent_3par: Prevent InsecureRequestWarning error when ignoring SSL cert issues
* 6194 FIX: Windows fileinfo: wrong size for files exceeding 4 GB
* 6246 FIX: Windows Powershell: Scripts are now always called with the options -noprofile -executionpolicy bypass
* 6193 FIX: OpenHardwareMonitorCLI.exe was broken
* 6445 FIX: Fixed broken openhardwaremonitor executable
* 6459 FIX: 3par_volumes: Fix crash due to unknown provisioning type
You can download Check_MK from our download page:
* http://mathias-kettner.de/chec
From: Check_mk Announcements
Date: Sat, Aug 11, 2018 at 6:16 AM
Date: Sat, Aug 11, 2018 at 6:16 AM
Changes in all Check_MK Editions:
WATO:
* 6247 FIX: The WATO edit folder page is no longer broken, when the tag group criticality gets deleted
* 6422 FIX: Prevent non-admin users from managing custom host/user attributes
* 6425 FIX: Improved validation of timeperiods before deletion
* 6439 FIX: Fixed upload of some icon files
* 6431 FIX: Fixed bulk discovery (addition to #6377 in 1.5.0)
* 6440 FIX: Backup: Deleting a backup job now deletes the state file
User interface:
* 6433 FIX: Raw edition: Fixed interface graphs when no warn/crit/bandwidth is reported
* 6432 FIX: Raw Edition: Fixed possible broken graphs related to lower/upper parameters
* 6436 FIX: Prevent metrics with "," in their names from breaking graphs
* 5918 FIX: New Theme: Fixed several bugs
* 6424 FIX: LDAP: Only set SSL/TLS specific options when SSL is enabled
* 6423 FIX: Fixed possible XSS in views with some filters
* 6421 FIX: Fixed interpretation of script tags when displaying werk texts
* 6441 FIX: Fixed broken bulk host import with discovery (Regression in 1.5.0)
* 6434 FIX: Background jobs: Not stoppable jobs ignore SIGTERM now
Site management:
* 6435 FIX: omd stop on all processes of a site terminates remaining site processes
* 6443 FIX: Fixed possible "omd backup" error when files vanish during backup
* 6396 FIX: Fixed 'Unhandled exception 452' in master control snapin if EC Daemon was disabled via 'omd config'
Notifications:
* 6399 FIX: Avoid failed notifications in case of crash dumps
Event console:
* 6427 FIX: Raw Edition: Fixed broken Event Console rule editing (1.5 regression)
* 6438 FIX: Fixed canceling of events when positive and cancel messages both match
* 6428 FIX: Fixed broken positive matching on syslog priority
* 6429 FIX: Fixed broken cancel event based on priority
Core & setup:
* 6372 FIX: Check_MK service: Piggyback data source reports the source hosts now
Checks & agents:
* 6420 agent_3par: Certificate verification can now be enabled/disabled
* 6127 FIX: ucd.include: Astaro and Synology are Linux but should use hr_mem
NOTE: Please refer to the migration notes!
* 6391 FIX: multipath: Fixed unrecognized paths which include a dot
* 6395 FIX: mk_cups_queues: Fixed discovery of several printers
* 6442 FIX: huawei_osn_if: Fixed broken check (check_if_common is not defined)
* 6393 FIX: check_bi_aggr: Fixed link in 'Open this aggregation' in the dropdown menu of the aggregation service
* 6444 FIX: brocade_mlx.module_mem: Fixed broken discovery function (KeyError: state)
* 6419 FIX: agent_3par: Prevent InsecureRequestWarning error when ignoring SSL cert issues
* 6194 FIX: Windows fileinfo: wrong size for files exceeding 4 GB
* 6246 FIX: Windows Powershell: Scripts are now always called with the options -noprofile -executionpolicy bypass
* 6193 FIX: OpenHardwareMonitorCLI.exe was broken
* 6445 FIX: Fixed broken openhardwaremonitor executable
* 6459 FIX: 3par_volumes: Fix crash due to unknown provisioning type
You can download Check_MK from our download page:
* http://mathias-kettner.de/chec
2018年8月10日 星期五
Plex: Artist Radio on more devices
| Already available on Alexa, Roku, and our very cool desktop music player, Plexamp, Artist Radio is now available on your iOS and Android mobile devices, as well as Android TV and Apple TV. With Artist Radio, pick any musician or band from your music collection and Plex will make a radio station with similar artists from your library. Give it a go and rediscover music from all corners of your collection. |
2018年8月9日 星期四
TrendLabs:Malware Targeting Bitcoin ATMs Pops Up in the Underground
Figure 1. Listing for a Bitcoin ATM malware
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/malware-targeting-bitcoin-atms-pops-up-in-the-underground/
2018年8月8日 星期三
[USN-3732-1] Linux kernel vulnerability
---------- Forwarded message ----------
From: Steve Beattie
Date: 2018-08-07 5:59 GMT+08:00
Summary:
The system could be made unavailable if it received specially crafted
network traffic.
Details:
Juha-Matti Tilli discovered that the TCP implementation in the Linux kernel
performed algorithmically expensive operations in some situations when
handling incoming packets. A remote attacker could use this to cause a
denial of service.
References:
https://usn.ubuntu.com/usn/
CVE-2018-5390
Date: 2018-08-07 5:59 GMT+08:00
Summary:
The system could be made unavailable if it received specially crafted
network traffic.
Details:
Juha-Matti Tilli discovered that the TCP implementation in the Linux kernel
performed algorithmically expensive operations in some situations when
handling incoming packets. A remote attacker could use this to cause a
denial of service.
References:
https://usn.ubuntu.com/usn/
CVE-2018-5390
2018年8月7日 星期二
Trello: Why Flexibility With Where, When, And How You Work Boosts Productivity
.png?t=1532643083020&width=2000&name=2018-06-28_FastLaneToFreedom_r05TP%20(1).png)
Many of us have access to freedom in our personal lives, but how often do we feel like our job is constraining us from doing what we want, when we want, and where we want? When it comes to flexibility at work, it’s common to feel like you’re in a constant battle. And thanks to micromanaging bosses and high expectations, productivity and happiness can fall by the wayside.
REF: https://blog.trello.com/fast-lane-to-freedom-why-flexibility-with-work-boosts-productivity
2018年8月6日 星期一
Two New Variants of Spectre Discovered
By Swapnil Bhartiya
Security researchers have discovered two new variants of Spectre 1 that can be used to compromise systems running AMD, ARM, and Intel chips.
2018年8月5日 星期日
TrendLabs: The Need for Managed Detection and Response: Persistent and Prevalent Threats in North America’s Security Landscape

Figure 1. Detections for information stealers, cryptocurrency-mining malware, and ransomware in North America in Q2 2018
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/the-need-for-managed-detection-and-response-persistent-and-prevalent-threats-in-north-americas-security-landscape/
2018年8月4日 星期六
Trello: How To Give Negative Feedback Beyond The Compliment Sandwich

“We need to talk.”
Those words strike fear into the heart of every employee. The minute we sense that our flaws are about to be pointed out, a deluge of worries fills our mind: Am I doing something wrong? Will I lose my job?
REF: https://blog.trello.com/how-to-give-negative-feedback-beyond-the-compliment-sandwich
2018年8月3日 星期五
TrendLabs: Adversarial Sample Generation: Making Machine Learning Systems Robust for Security
Figure 1. Using adversarial samples and AI to make an ML system more robust
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/adversarial-sample-generation-making-machine-learning-systems-robust-for-security/
2018年8月2日 星期四
[Check_mk Announce] New Check_MK beta release 1.5.0b10
---------- Forwarded message ---------
..Changes in all Check_MK Editions:
WATO:
* 6366 FIX: User and profile edit dialogs show wrong language when 'en' is configured
User interface:
* 6367 FIX: Fixed HTML fragments shown in hover title of perfometers
* 6360 FIX: Fixed HTML fragments in global settings titles
* 6363 FIX: Fixed "host_inventory" exception when using "Has inventory data" filter
* 6357 FIX: Facelift theme: Icon buttons were not using themed buttons
* 5917 FIX: Facelift theme: Fixed Logo in Browser tab
HW/SW inventory:
* 6386 FIX: esx_vsphere_hostsystem: Fixed crash if no hardware system information is available
* 6369 FIX: Fixed date shown for the first inventory history entry
DEB packaging:
* 6365 FIX: Another fix for debian package incompatibilities (extends 6340)
Core & setup:
* 6358 FIX: Fixed stale services on cluster nodes
Checks & agents:
* 6380 FIX: oracle_jobs: Bugfix for auto_drop=TRUE jobs
NOTE: Please refer to the migration notes!
* 6315 FIX: mssql_backup: Fixed missing default levels
* 6383 FIX: db2_bp_hitratios: Fixed conversion to float if any value contains a comma instead of a dot
* 6384 FIX: check_mk_agent.linux, check_mk_agent.solaris, check_mk_agent.openwrt: Quote command line in asynchronous MRPE call to prevent globbing and word splitting
* 6364 FIX: check_mk_active_bi: Fixed crashed checks (Regression in 1.5.0b9)
* 6381 FIX: apc_inrow_system_events, liebert_system_events: Fixed handling of empty section
* 6385 FIX: Check_MK service: Fixed 'missing agent sections' warning if the time period of a service is active
..You can download Check_MK from our download page:
* http://mathias-kettner.de/chec
Please mail bug reports and qualified feedback to feedback@check-mk.org.
We greatly thank you for using Check_MK and wish you a successful monitoring,
From: Check_mk Announcements
Date: Fri, Jul 27, 2018 at 4:36 PM
Date: Fri, Jul 27, 2018 at 4:36 PM
..Changes in all Check_MK Editions:
WATO:
* 6366 FIX: User and profile edit dialogs show wrong language when 'en' is configured
User interface:
* 6367 FIX: Fixed HTML fragments shown in hover title of perfometers
* 6360 FIX: Fixed HTML fragments in global settings titles
* 6363 FIX: Fixed "host_inventory" exception when using "Has inventory data" filter
* 6357 FIX: Facelift theme: Icon buttons were not using themed buttons
* 5917 FIX: Facelift theme: Fixed Logo in Browser tab
HW/SW inventory:
* 6386 FIX: esx_vsphere_hostsystem: Fixed crash if no hardware system information is available
* 6369 FIX: Fixed date shown for the first inventory history entry
DEB packaging:
* 6365 FIX: Another fix for debian package incompatibilities (extends 6340)
Core & setup:
* 6358 FIX: Fixed stale services on cluster nodes
Checks & agents:
* 6380 FIX: oracle_jobs: Bugfix for auto_drop=TRUE jobs
NOTE: Please refer to the migration notes!
* 6315 FIX: mssql_backup: Fixed missing default levels
* 6383 FIX: db2_bp_hitratios: Fixed conversion to float if any value contains a comma instead of a dot
* 6384 FIX: check_mk_agent.linux, check_mk_agent.solaris, check_mk_agent.openwrt: Quote command line in asynchronous MRPE call to prevent globbing and word splitting
* 6364 FIX: check_mk_active_bi: Fixed crashed checks (Regression in 1.5.0b9)
* 6381 FIX: apc_inrow_system_events, liebert_system_events: Fixed handling of empty section
* 6385 FIX: Check_MK service: Fixed 'missing agent sections' warning if the time period of a service is active
..You can download Check_MK from our download page:
* http://mathias-kettner.de/chec
Please mail bug reports and qualified feedback to feedback@check-mk.org.
We greatly thank you for using Check_MK and wish you a successful monitoring,
Plex: Polishing Podcasts
| We are super duper psyched to share with y’all that podcasts are officially out of beta*! Along with rich metadata and features like On Deck, personalized recommendations, variable speed playback, and a customizable home screen, we’ve got some awesome new goodies for your podcast pleasure: |
[USN-3722-1] ClamAV vulnerabilities
---------- Forwarded message ----------
From: Marc Deslauriers
Date: 2018-07-25 2:44 GMT+08:00
Summary:
ClamAV could be made to hang if it opened a specially crafted file.
Details:
It was discovered that ClamAV incorrectly handled parsing certain HWP
files. A remote attacker could use this issue to cause ClamAV to hang,
resulting in a denial of service. (CVE-2018-0360)
It was discovered that ClamAV incorrectly handled parsing certain PDF
files. A remote attacker could use this issue to cause ClamAV to hang,
resulting in a denial of service. (CVE-2018-0361)
References:
https://usn.ubuntu.com/usn/usn-3722-1
CVE-2018-0360, CVE-2018-0361
From: Marc Deslauriers
Date: 2018-07-25 2:44 GMT+08:00
Summary:
ClamAV could be made to hang if it opened a specially crafted file.
Details:
It was discovered that ClamAV incorrectly handled parsing certain HWP
files. A remote attacker could use this issue to cause ClamAV to hang,
resulting in a denial of service. (CVE-2018-0360)
It was discovered that ClamAV incorrectly handled parsing certain PDF
files. A remote attacker could use this issue to cause ClamAV to hang,
resulting in a denial of service. (CVE-2018-0361)
References:
https://usn.ubuntu.com/usn/usn-3722-1
CVE-2018-0360, CVE-2018-0361
Trello: Tweak These 5-Minute Productivity Tricks To Make Your Workdays More Organized
Start Your Morning Routine The Night Before
Mastering productive morning routines has become an art over the years. Olympic Gold medalists, movie stars, and millionaires all share their strategies on how to maximize the early hours of their days in order to set themselves up for a productive workday. It’s true that people who wake up earlier are often more productive, but you can get an additional boost the night before.
REF: https://blog.trello.com/tweak-5-minute-productivity-tricks-make-workdays-more-organized
New Version of the Spectre Vulnerability Allows Attack from the Network
By Swapnil Bhartiya
Monthly reports of new Spectre-related vulnerabilities are keeping security experts busy. Now a team of security researchers at the Graz University of Technology (Austria) has discovered another flaw, dubbed NetSpectre, that allows attacks over the network.
TrendLabs: Spam Campaign Abusing SettingContent-ms Found Dropping Same FlawedAmmyy RAT Distributed by Necurs
Figure 2. Infection chain of the spam campaign
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/spam-campaign-abusing-settingcontent-ms-found-dropping-same-flawedammy-rat-distributed-by-necurs/
訂閱:
意見 (Atom)











