|
2018年2月28日 星期三
2018年2月27日 星期二
Application Debugging and Troubleshooting
2018年2月26日 星期一
TrendLabs: Update on Pawn Storm

Figure 1. A sample of a credential phishing email Pawn Storm sent in October and November 2017
REF: http://blog.trendmicro.com/trendlabs-security-intelligence/update-pawn-storm-new-targets-politically-motivated-campaigns/
2018年2月25日 星期日
2018年2月24日 星期六
Plex news on all of your devices
Your news on all of your devices
Plex News gives you a consistent experience on every screen — watch your morning headlines on the TV then continue catching up on your phone during your commute. This feature is currently available on Android TV, NVIDIA SHIELD, Amazon Fire TV, Apple TV, Roku, Plex Web, Android Mobile, and iOS, with other platforms to follow. Plex News is ad-supported, which means that it comes at no additional cost to you, allowing everyone to enjoy high quality news content.

2018年2月23日 星期五
2018年2月22日 星期四
2018年2月21日 星期三
Using OpenBSD on a thinkpad
---------- Forwarded message ----------
From: Peter N. M. Hansteen
Date: Mon, Feb 19, 2018 at 8:05 PM
Subject: Re: Using OpenBSD on a thinkpad?
To: misc@openbsd.org
On Mon, Feb 19, 2018 at 08:00:30PM +1100, crimeangothic@nigge.rs wrote:
>
> Hey everyone, I am pretty stupid when it comes to less user friendly operating systems. I currently use slackware/windows and am thinking of using OpenBSD on either my thinkpad e420 or my libreboot t400. Are either supported(or at least possible to install on?
Thinkpads in general are well supported. Part of the reason is that quite a few
of the developes have a strong preference for the machines.
That said, the is always a non-zero risk of some variant being odder than others,
but a brief glance on the specifications for the models you mention do not raise
any obvious red flags here.
From: Peter N. M. Hansteen
Date: Mon, Feb 19, 2018 at 8:05 PM
Subject: Re: Using OpenBSD on a thinkpad?
To: misc@openbsd.org
On Mon, Feb 19, 2018 at 08:00:30PM +1100, crimeangothic@nigge.rs wrote:
>
> Hey everyone, I am pretty stupid when it comes to less user friendly operating systems. I currently use slackware/windows and am thinking of using OpenBSD on either my thinkpad e420 or my libreboot t400. Are either supported(or at least possible to install on?
Thinkpads in general are well supported. Part of the reason is that quite a few
of the developes have a strong preference for the machines.
That said, the is always a non-zero risk of some variant being odder than others,
but a brief glance on the specifications for the models you mention do not raise
any obvious red flags here.
2018年2月20日 星期二
BSD patches for Spectre/Meltdown
The OpenIndiana project is still alive and well with a recent announcement of migrating the project to GCC 6.4. Unfortunately, this version does not cover the Spectre/Meltdown vulnerabilities, although the next version planned is 7.3 which will cover these hot issues.
While on the topic, the FreeBSD Unix distribution finally patched and fixed their operating environment for both Spectre and Meltdown in revision 329462.
The NetBSD team has been working to improve the security of their highly portable operating system. Several of the enhancements coming to NetBSD's stable branch involve the removal of legacy code and patches to work around the Meltdown and Spectre CPU bugs: "Ilja Van Sprundel presented at Defcon 25 (July 2017) and 34c3 (December 2017) the results of his audit of the BSD kernels. The issues affecting NetBSD were fixed overnight in the NetBSD-current branch, and were propagated to the stable branches within a month. Kernels from NetBSD-6 and NetBSD-7 built after August 23rd 2017 had all the necessary fixes. Some reports published recently suggest that the stable branches remained vulnerable for months, and that NetBSD was lagging behind; that is simply not true. In Ilja Van Sprundel's report, NetBSD was criticized for having too much legacy and buggy code. Several proactive measures were taken, within a month again, to clean up the system." Further details can be found in a blog post on the NetBSD website. http://blog.netbsd.org/tnf/entry/recent_security_affairs
REF: http://www.linuxjournal.com/content/kernel-patch-releases-winehq-openindiana-project-freebsd-unix-distribution-xubuntu-community
While on the topic, the FreeBSD Unix distribution finally patched and fixed their operating environment for both Spectre and Meltdown in revision 329462.
The NetBSD team has been working to improve the security of their highly portable operating system. Several of the enhancements coming to NetBSD's stable branch involve the removal of legacy code and patches to work around the Meltdown and Spectre CPU bugs: "Ilja Van Sprundel presented at Defcon 25 (July 2017) and 34c3 (December 2017) the results of his audit of the BSD kernels. The issues affecting NetBSD were fixed overnight in the NetBSD-current branch, and were propagated to the stable branches within a month. Kernels from NetBSD-6 and NetBSD-7 built after August 23rd 2017 had all the necessary fixes. Some reports published recently suggest that the stable branches remained vulnerable for months, and that NetBSD was lagging behind; that is simply not true. In Ilja Van Sprundel's report, NetBSD was criticized for having too much legacy and buggy code. Several proactive measures were taken, within a month again, to clean up the system." Further details can be found in a blog post on the NetBSD website. http://blog.netbsd.org/tnf/entry/recent_security_affairs
REF: http://www.linuxjournal.com/content/kernel-patch-releases-winehq-openindiana-project-freebsd-unix-distribution-xubuntu-community
2018年2月19日 星期一
Trello: Emoji Reactions!
Adding an emoji reaction to a comment
Open the card in question and scroll down to the comments. You'll see the option to add an emoji reaction:

TrendLabs: Vulnerabilities in Apache CouchDB Open the Door to Monero Miners
Figure 1: Chart showing the detection of potential attacks; early February was when the peaks occurred
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/vulnerabilities-apache-couchdb-open-door-monero-miners/
2018年2月17日 星期六
New Check_MK stable release 1.2.8p27
This maintenance release of the current "old stable" version ships with 19
changes affecing all editions of Check_MK, 1 Enterprise Edition specific
change and 0 Managed Services Edition specific changes.
Checks & Agents:
* 5302 FIX: oracle_instance: Fixed crash if output contains more than 12 columns
* 5316 FIX: cmciii.access: Fixed error state handling...
* 5518 FIX: win.mem: Fix incorrect representation of absolute memory levels in graphs...
* 5548 FIX: zpool_status: Fixed crash if pool has been deleted or vanished...
* 5549 FIX: mk_oracle.ps1: Fixed scattered information for configuration...
* 5550 FIX: mk_oracle.ps1: Fixed exceptions because of useless backslashes...
* 5451 FIX: logwatch: Fixed reclassifying mechanism: Patterns did not apply correctly if they have changed
* 5417 FIX: Windows: allow whitespace in eventlog event source...
* 5608 FIX: temperature.include: Fixed device levels handling
* 5557 FIX: check_mk_agent.aix: Fixed bug in uptime because AIX is not able to interpret ? and + in regexes
Multisite:
* 4757 SEC: Fixed possible reflected XSS in webapi.py...
WATO:
* 4222 FIX: Services of host page: Fixed encoding issue for hosts with umlauts in alias
REF: http://mathias-kettner.de/check_mk_download.html
changes affecing all editions of Check_MK, 1 Enterprise Edition specific
change and 0 Managed Services Edition specific changes.
Checks & Agents:
* 5302 FIX: oracle_instance: Fixed crash if output contains more than 12 columns
* 5316 FIX: cmciii.access: Fixed error state handling...
* 5518 FIX: win.mem: Fix incorrect representation of absolute memory levels in graphs...
* 5548 FIX: zpool_status: Fixed crash if pool has been deleted or vanished...
* 5549 FIX: mk_oracle.ps1: Fixed scattered information for configuration...
* 5550 FIX: mk_oracle.ps1: Fixed exceptions because of useless backslashes...
* 5451 FIX: logwatch: Fixed reclassifying mechanism: Patterns did not apply correctly if they have changed
* 5417 FIX: Windows: allow whitespace in eventlog event source...
* 5608 FIX: temperature.include: Fixed device levels handling
* 5557 FIX: check_mk_agent.aix: Fixed bug in uptime because AIX is not able to interpret ? and + in regexes
Multisite:
* 4757 SEC: Fixed possible reflected XSS in webapi.py...
WATO:
* 4222 FIX: Services of host page: Fixed encoding issue for hosts with umlauts in alias
REF: http://mathias-kettner.de/check_mk_download.html
2018年2月16日 星期五
TrendLabs: February Patch Tuesday Is a Bouquet of Fixes for Privilege Escalation Vulnerabilities
Of note are three vulnerabilities:
- CVE-2018-0852: A memory corruption vulnerability in Microsoft Outlook that, when exploited successfully, can let attackers run arbitrary code. What’s notable with this flaw is that Outlook’s Preview Pane can become an attack vector — the would-be victim need only receive a preconfigured message for malicious code to run. If logged on with administrative rights, it can enable hackers to hijack the system, such as installing programs, viewing, altering or deleting data, or creating privileged user accounts. The malicious file can also be hosted on an attacker-owned or compromised website, in which case the hacker would have to trick users into clicking a link that will divert victims to the site.
- CVE-2018-0850: A privilege escalation flaw in Microsoft Outlook. The vulnerability can be exploited through an especially crafted email designed to force Outlook to load local or remote messages over Server Message Block (SMB).
- CVE-2018-0771: A security feature bypass vulnerability in Microsoft Edge. When exploited successfully, Microsoft Edge will be able to circumvent Same-Origin Policy (SOP) restrictions, which prevent a website’s scripts (i.e., JavaScript, Ajax) from accessing sensitive data from and interacting with other scripts used on other websites.
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/february-patch-tuesday-bouquet-fixes-privilege-escalation-vulnerabilities/
Plex: News on your terms
Real news, personalized by you
Personalize your news feed with over 190 global publisher partners (and growing!), including international sources, like Associated Press (AP), Reuters, Financial Times, Euronews, and top local news sources for over 80% of markets in the US.2018年2月14日 星期三
Adding NewTek Native File Codecs to Your System
 | |
|
2018年2月13日 星期二
TrendLabs: Detecting New Threats via Contextual Information and Reputation

Figure 1. Overview of detection method
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/xgen-detection-new-threats/
2018年2月11日 星期日
Six Trello boards to stay on track
Track progress as cards move across lists from To Do to Done. Invite friends, family, and colleagues to collaborate and help cheer you on!

Dream. Plan. Do. With Trello!
REF: https://trello.com/dreambig

Dream. Plan. Do. With Trello!
REF: https://trello.com/dreambig
TrendLabs: Attack Using Windows Installer msiexec.exe leads to LokiBot
Figure 1: Infection Chain for the attack
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/attack-using-windows-installer-msiexec-exe-leads-lokibot/
2018年2月9日 星期五
2018年2月8日 星期四
lavfi-generated streams with ffmpeg
2018年2月7日 星期三
TrendLabs: New Mobile Malware Uses Layered Obfuscation
Figure 1. Top countries where samples were detected; there were detections in other countries but they totaled less than 1%
REF: http://blog.trendmicro.com/trendlabs-security-intelligence/new-mobile-malware-uses-layered-obfuscation-targets-russian-banks/
Implementing Digital Rights Management In-Kernel
...Pavel Machek specifically said that he couldn't see any case where a user would set the feature to anything other than "off." He also asked, "If kernel implements this, will it mean hardware vendors will have to prevent user[s] from updating the kernel on machines they own?" And wondered, "If this is merged, does it open kernel developers to DMCA threats if they try to change it?"
REF: http://www.linux-magazine.com/Issues/2018/208/Kernel-News
REF: http://www.linux-magazine.com/Issues/2018/208/Kernel-News
2018年2月5日 星期一
TrendLabs: Hacking Group Spies on Android Users in India
Figure 10. The chart above shows the connections between the C&C servers of PoriewSpy and DroidJack-built apps, and the suspected cyberespionage group. The green dots represent the current malicious samples. IPs colored in yellow are the ones used by the group in their previous campaign, while the ones in red are presumably the extension to the mobile platform.
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/hacking-group-spies-android-users-india-using-poriewspy/
2018年2月4日 星期日
OpenBSD Errata: February 2nd, 2018 (kernel)
From: T.J. Townsend
Date: Sat, Feb 3, 2018 at 7:02 AM
Subject: OpenBSD Errata: February 2nd, 2018 (kernel)
To: announce@openbsd.org
Errata patches for a number of kernel issues have been released for
OpenBSD 6.2 and 6.1.
Specially crafted IPsec AH packets with IP options or IPv6 extension
headers could cause a crash or hang.
Processing IPv6 fragments could incorrectly access memory of an mbuf
chain that is not within an mbuf, which may cause a crash.
If the EtherIP tunnel protocol was disabled, IPv6 packets were not
discarded properly, which causes a double free.
Binary updates for the amd64, i386, and arm64 platforms are available via
the syspatch utility. Source code patches can be found on the respective
errata pages:
https://www.openbsd.org/errata61.html
https://www.openbsd.org/errata62.html
As these affect the kernel, a reboot will be needed after patching.
Date: Sat, Feb 3, 2018 at 7:02 AM
Subject: OpenBSD Errata: February 2nd, 2018 (kernel)
To: announce@openbsd.org
Errata patches for a number of kernel issues have been released for
OpenBSD 6.2 and 6.1.
Specially crafted IPsec AH packets with IP options or IPv6 extension
headers could cause a crash or hang.
Processing IPv6 fragments could incorrectly access memory of an mbuf
chain that is not within an mbuf, which may cause a crash.
If the EtherIP tunnel protocol was disabled, IPv6 packets were not
discarded properly, which causes a double free.
Binary updates for the amd64, i386, and arm64 platforms are available via
the syspatch utility. Source code patches can be found on the respective
errata pages:
https://www.openbsd.org/errata61.html
https://www.openbsd.org/errata62.html
As these affect the kernel, a reboot will be needed after patching.
2018年2月3日 星期六
2018年2月2日 星期五
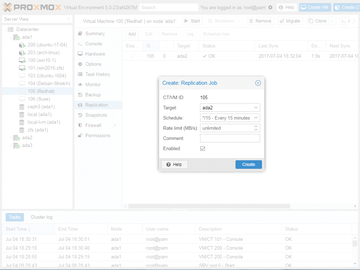
Proxmox virtualization manager / Cloudless
TrendLabs: Malicious Chrome Extensions Found

Figure 1. Droidclub Infection Flow
REF: https://blog.trendmicro.com/trendlabs-security-intelligence/malicious-chrome-extensions-found-chrome-web-store-form-droidclub-botnet/
訂閱:
意見 (Atom)